All Advanced Attacks are Runtime Attacks
Secure all assets (Applications, Cloud, Containers, Kubernetes, APIs, Al/LLMs) with
Runtime Powered Zero Trust CNAPP
Trusted by global Innovation Leaders








Why DevSecOps and Security Teams Love our AppSec Platform?


“AccuKnox offers us the protection we need for our cloud infrastructure, while ModelKnox ensures that our AI assets remain secure and resilient against evolving threats.”
Utku Kaynar
CEO


“At Prudent, we advocate for a comprehensive end-to-end methodology in application and cloud security. AccuKnox excelled in all areas in our in depth evaluation.”
Manoj Kern
CIO


“Choosing AccuKnox was driven by opensource KubeArmor’s novel use of eBPF and LSM technologies, delivering runtime security”
Golan Ben-Oni
Chief Information Officer


“As 5G starts getting broad industry adoption, security is a very critical challenge. It is delightful to see an amazing innovator like SRI work with AccuKnox to deliver critical innovations”
Jim Brisimitzis
General Partner


“The discovery process is crucial to making drug discovery faster, smarter, and secure. We are pleased to partner with AccuKnox for their AI Security prowesses”
Matt Shlosberg
Chief Operating Officer


“AccuKnox very strong and Enterprise offering coupled with a strong roadmap of securing AI/LLM Models made them a compelling choice”
Rahul Saxena
Co-founder, Chief Product & Technology Officer

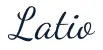
“AccuKnox does a tremendous job at showing the complexity of different approaches to Kubernetes security in terms of responding to high severity cloud attacks”
James Berthoty
Founder & Security Analyst


“We were able to work with a pioneer in Zero Trust Security. Tible is committed to delivering comprehensive security, compliance, and governance for all of its stakeholders”
Merijn Boom
Managing Director
Everything you need to secure, monitor, and stay compliant in the cloud
 5+ Public Clouds Support
5+ Public Clouds Support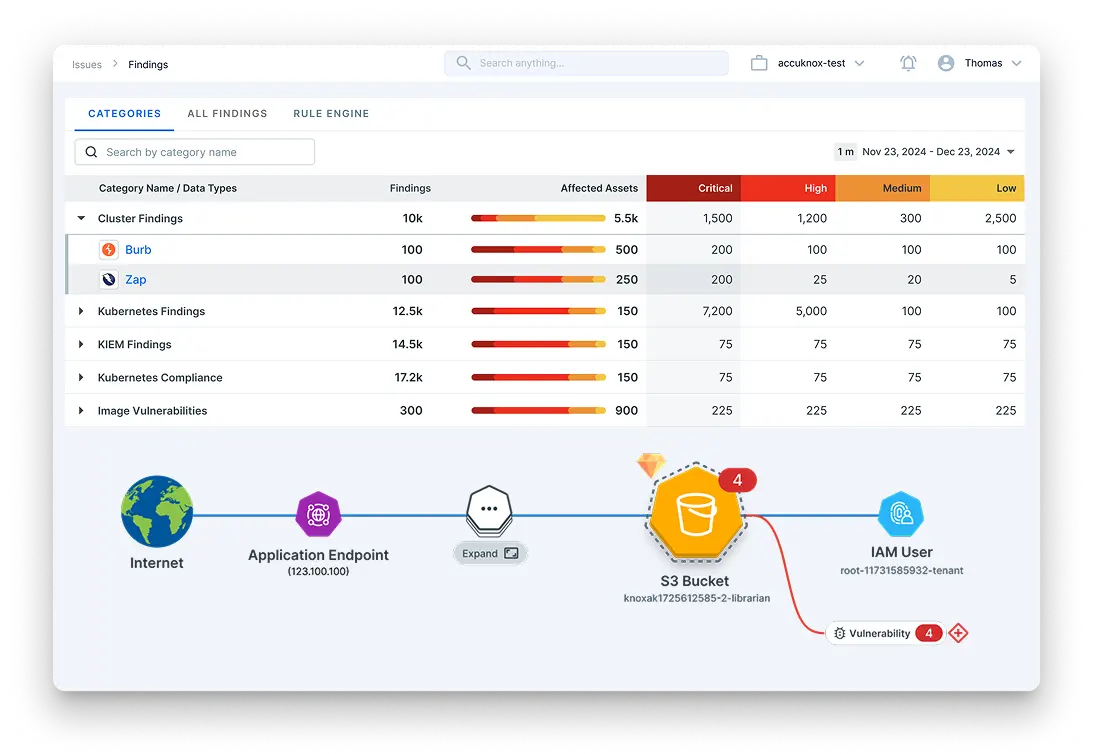
Everything you need to write secure code and fix risks fast
 9+ CI/CID Platforms Supported
9+ CI/CID Platforms Supported
Everything you need to keep your AI models, datasets and inferences safe from threats
 100+ Supported Models across Leading LLMs
100+ Supported Models across Leading LLMs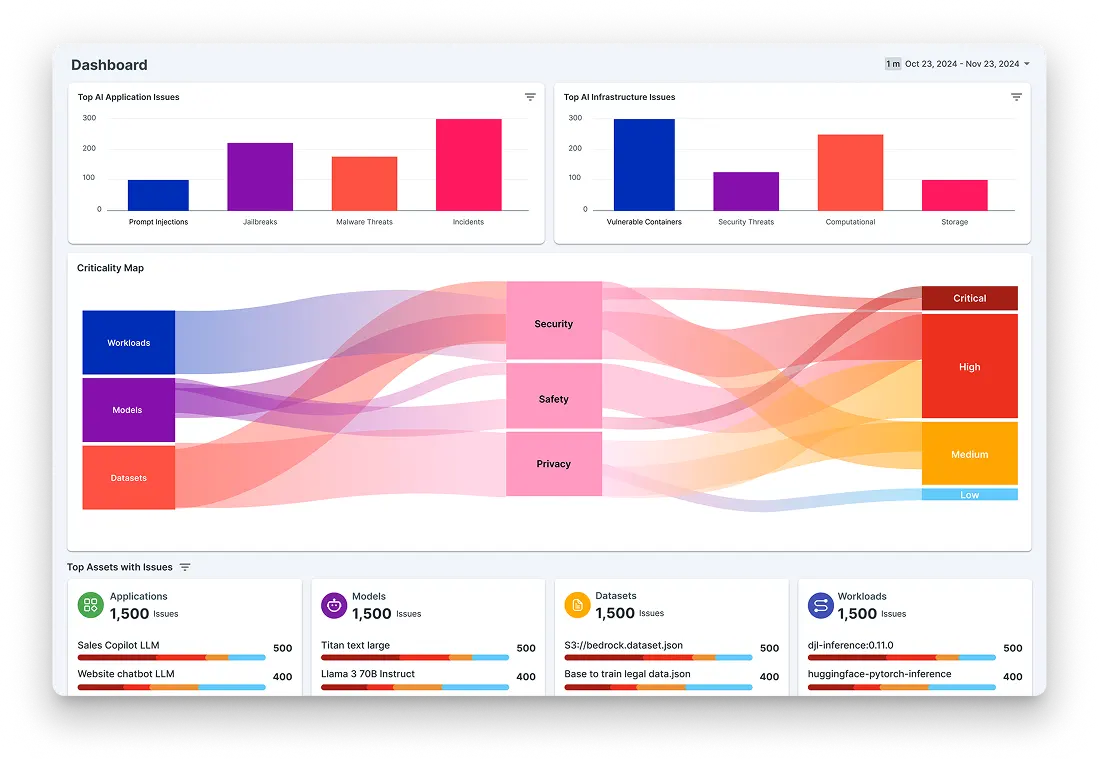
Vulnerability Management. Security Posture. Container Security. Zero Day Attack. Workload Protection
Vulnerability Management. Security Posture. Container Security. Zero Day Attack. Workload Protection
Zero Trust Cloud. Kubernetes Security. Threat Intelligence. Open Source. Ransomware Detection.
Zero Trust Cloud. Kubernetes Security. Threat Intelligence. Open Source. Ransomware Detection.
Container Image Security. Multi-Cloud Security. Run time Security. Protect Cyber Attack. 5G Security
Container Image Security. Multi-Cloud Security. Run time Security. Protect Cyber Attack. 5G Security
Experience Cloud Protect in Action
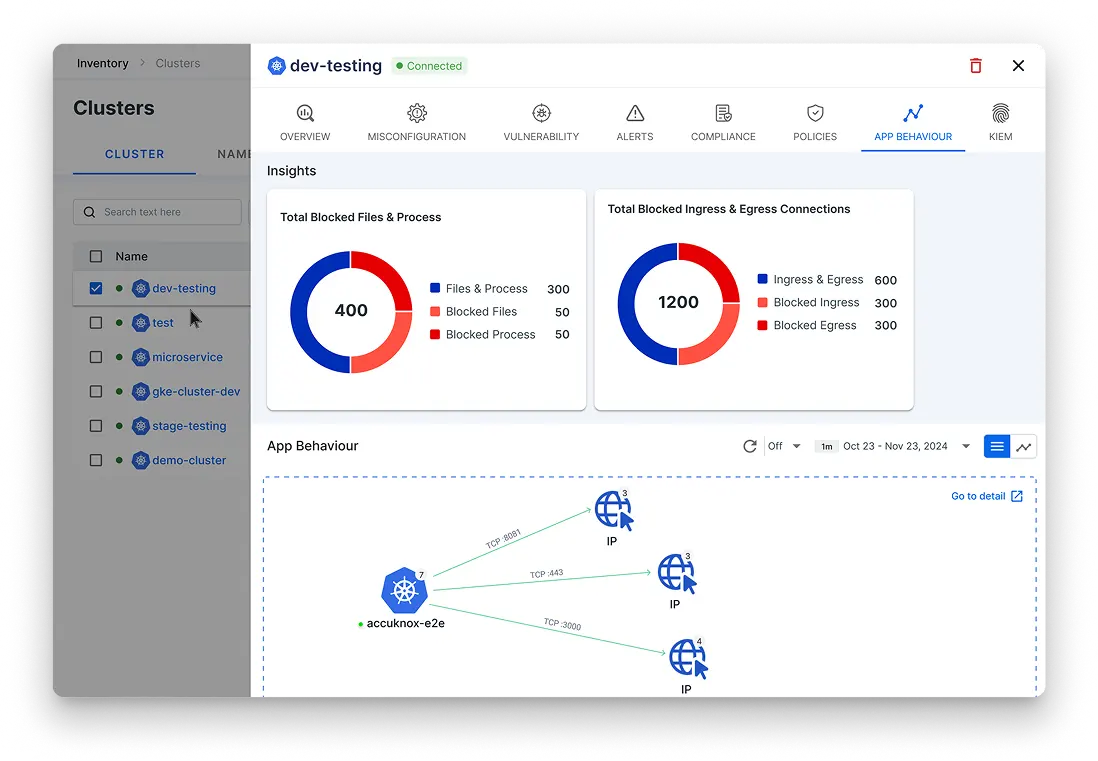
Everything you need to secure, monitor, and stay compliant in the cloud
 10+ K8 Engines Supported
10+ K8 Engines Supported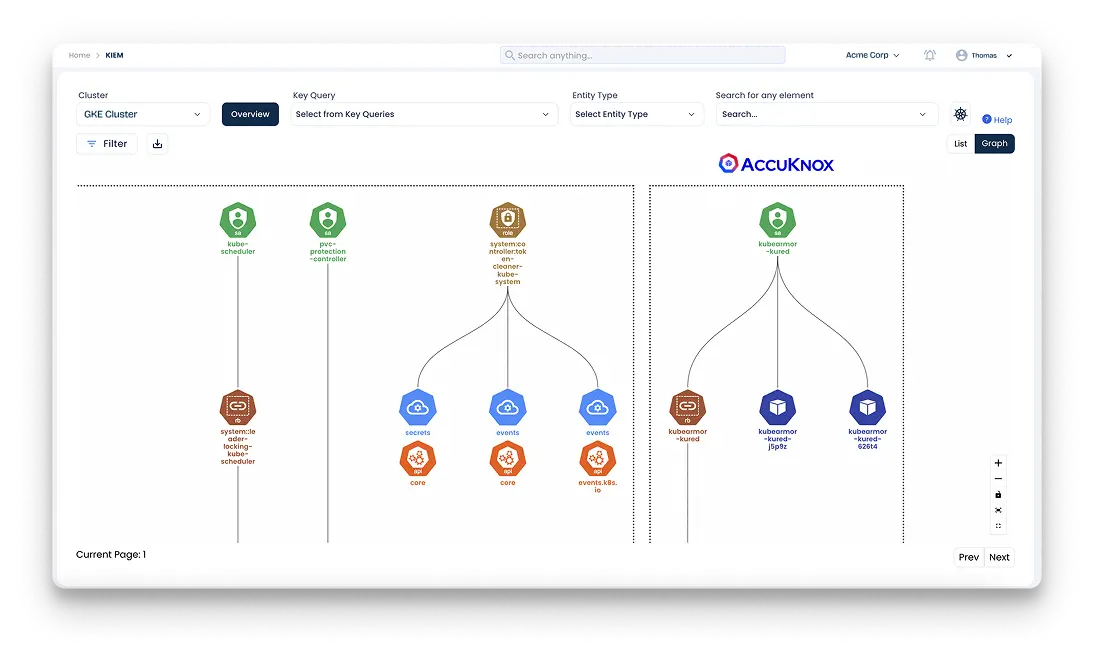
Everything you need to lock down Kubernetes and enforce security best practices
 10+ K8 Engines Supported
10+ K8 Engines Supported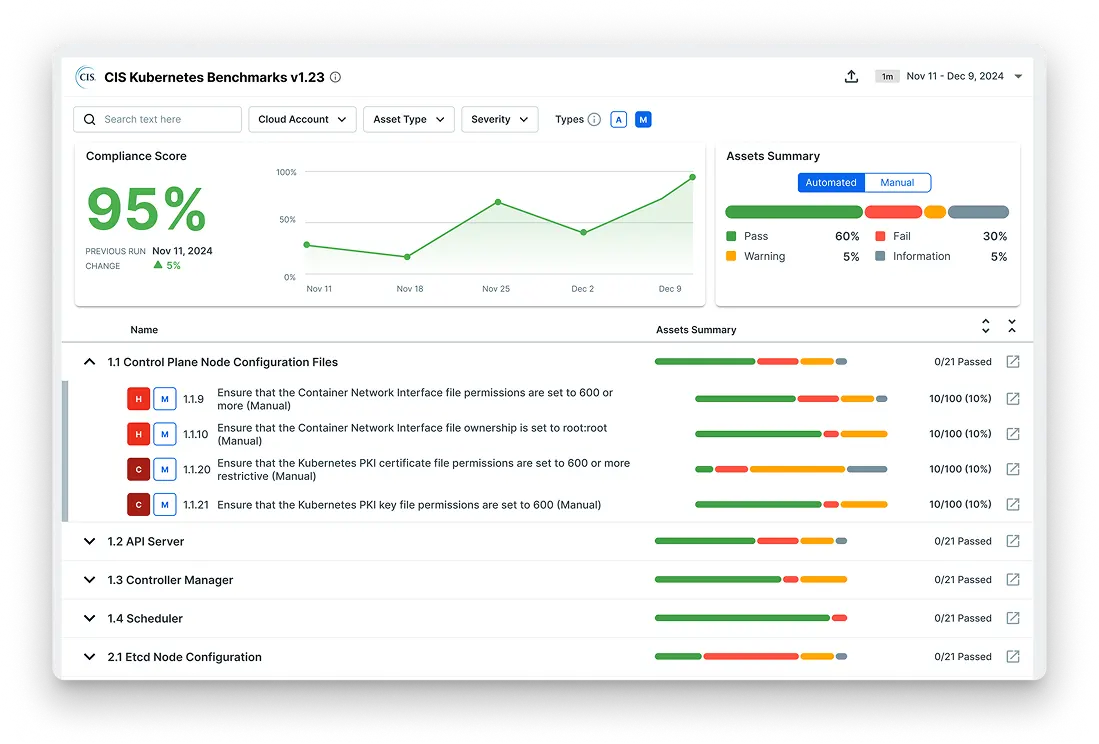
Everything you need to manage security policies, risks, and compliance
 30+ Integrated Compliance Frameworks
30+ Integrated Compliance FrameworksSecurity and Runtime Defence
Made Simple
AI Assisted Remediation + Automated Findings Lifecycle
37+
Native Integrations
89%
Fewer False Positives
91%
Reduced Remediation Time
Latest Resources & Publications
October 26, 2023
October 26, 2023
January 19, 2024
Backed by Leading Cybersecurity Investors





















