
2021 – Cloud security year-end review
2021 began amid an unfolding large-scale supply chain infiltration from a Russian espionage team and the Solarwinds attack back in Dec 2020 by Fireeye 2021 began amid an unfolding large-scale supply chain infiltration from a Russian espionage team. Discovered back in December 2020 by Fireeye, the Solarwinds attack led to a year of reflecting on […]
Reading Time: 7 minutes
Table of Contents
2021 began amid an unfolding large-scale supply chain infiltration from a Russian espionage team and the Solarwinds attack back in Dec 2020 by Fireeye
2021 began amid an unfolding large-scale supply chain infiltration from a Russian espionage team. Discovered back in December 2020 by Fireeye, the Solarwinds attack led to a year of reflecting on whether we can trust the very applications that are used to monitor and protect our networks. It was also a year that continued to confirm how relentlessly and unapologetically nation-states will continue to attack the corporate and government assets of their rivals. In 2021, we saw the largest monetary ransomware demands ever, with Russia’s REvil hacker team’s $50M ransom demand to Apple supplier Quanta, and its $70M Kaseya VSA ransom. REvil’s Colonial Pipeline ransom in May 2021 even disrupted the U.S. Eastern fuel supply, leading to shortages, price hikes, and a geopolitical confrontation between the U.S. and Russia. The year ended with the Log4Shell attack, with a 10-out-of-10 severity rank, and a doomed race to patch this massive world-wide software hole before every cyber criminal and nation-state espionage team can plant malicious logic and backdoors that will haunt computing environments for years to come. Sadly, this was barely a small summary of the highlights. 2021 has truly been a challenging year for anything with a CPU [13]. It also became a year in which adversaries displayed their ability to migrate to the technical edge of commercial application development, centering their expertise on infiltrating virtualized application workloads at scale. 2021 saw many new exploits, attack patterns, and criminal business strategies arise (or mature) across all the dominant cloud platforms, APIs, and popular services. Here is a brief timeline that captures some of the more significant security incidents in 2021, along with some lessons we should consider.
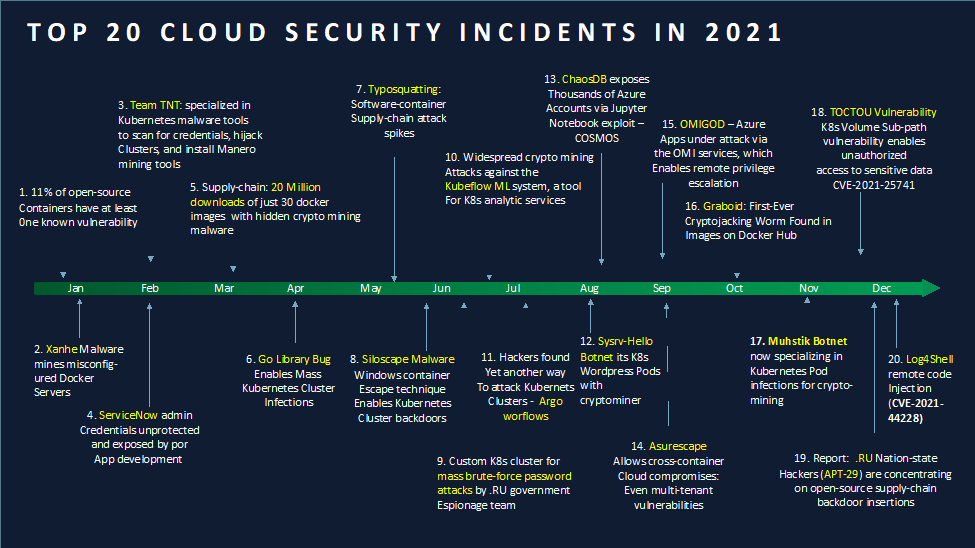
Malware migrates to the cloud – 2021 saw the emergence of newly packaged botnets and worms designed to infiltrate cloud environments, none of which were particularly sophisticated and nearly all of which carried cryptoming payload logic. Here are some example 2021 malware campaigns of note:
Xanthe:: A Monero miner that hijacks misconfigured Docker instances [17]
Sysvr-Hello:: A cryptominer designed to hijack WordPress Kubernetes pods [10]
Graboid:: A Cryptojacking worm found throughout images on Docker Hub [3]
TNTBotinger:: TeamTNTs IRC Botnet incorporates a range of malicious payloads [9]
Muhstik:: A web-app exploit botnet specializing in spreading cryptomining agents [5]. Targets of Muhstik included cloud instances of WordPress, Drupal, WebDave, Oracle’s WebLogic app server, as well as assort IoT and SOHO devices.
Siloscape:: Windows container malware implements an escape technique that enables Kubernetes cluster backdoors and raids nodes to steal credentials [20]. 2021 was a busy year for scan-and-mine malware and for spreading pre-infected images. The message is now clear: any public-facing container with poor credential management, or exploitable library, or that may be downloaded from untrustworthy image author, will more than likely lead to infections and malicious payload execution.
The rise of a cloud-focused hacking team –
2021 spotlighted a significant hacking team that built a reputation for infiltrating cloud applications. TeamTNT [18] distinguished itself among cloud-focused cyber-criminal teams, specializing in infiltrating and monetizing pods and containers around the world. In 2021, TeamTNT stood out by creating high-quality professionally developed tools for targeting misconfigured Amazon Web Services (AWS) or Kubernetes services [7, 11]. They specialized in credential theft, data theft, and crypto mining (including full use of GPUs, when presented). While they gained notoriety throughout the year, that were one among a community of hacking groups adept at constructing attacks that can keep pace with the adoption trends and DevOps design patterns of the latest cloud environments.
Cloud infrastructure vulnerabilities –
2021 unveiled a stream of exposed attack surfaces present within cloud services, popular images, tools and applications that DevOps teams rely on to create, manage and host their applications. For example, Kubeflow ML, a popular cloud platform for machine learning workloads on Kubernetes included a vulnerability that enabled widespread crypto mining attacks [21]. Argo workflows, an open-source Kubernetes workflow orchestration engine, included a vulnerable web-facing dashboard that allowed remote attackers to inject cryptomining apps into Argo-managed containers [22]. WordPress, among the most popular pods used for cloud web services, included libraries that became the target and the highly successful Sysrv-Hello cryptomining Botnet. A high severity vulnerability was found in Kubernetes itself, in which the filesystem introduced a TOCTTOU flaw that allowed workloads to have access to parts of the host filesystem outside the mounted volumes boundaries [12]. In August, COSMOS DB provided a DB access loophole, dubbed #ChaosDB, that enabled hackers to access thousands of MS Azure customer credentials, including from many Fortune 500 customers [4]. Among #ChaosDB activities was a vulnerability that enabled attackers to scan for and manipulate local Jupyter Notebooks to escalate privileges of other customer notebooks [23]. In September, the Azurescape vulnerability was found within the Azure Container Instances (ACI) service, which enabled cross-container attacks and even the first cross-account container takeover in a public cloud environment [6]. OMIGOD was also revealed in September [19], uncovering four vulnerabilities in Microsoft’s Open Management Infrastructure (OMI) service. OMIGOD enabled a remote privilege escalation attack on servers within Azure. Finally, 2021 closed in December with a critical zero-day Log4Shell exploit, offering a remote code Injection (CVE-2021-44228) vulnerability that has caused well-founded panic across cloud computing ecosystems worldwide [24]. It has been a rough year.
DevOps Insecurities –
2021 also saw many instances of misconfiguration, poor security practices, bad coding errors, and credential mismanagement. These mistakes are natural, as DevOps teams continue to learn the ins and outs of container workload migration to the cloud. In February, one example of an egregious DevOps blunder occurred within the ServiceNow cloud infrastructure [25]. The error occurred in the implementation of ServiceNow’s ‘Help the Help Desk’ feature, which left unencrypted password, including administrative passwords, stored in publicly viewable and accessible locations. More than 600 enterprises, universities, and government agencies may have had login credentials exposed because of this flaw. The resulting administrative access would have given adversaries access to IT Tickets, customer support tickets and other sensitive customer information, employee data, and internal data stores.
Nation states in the cloud –
One cannot help it. If you are developing virtualized application and deploying them into cloud environments, then you depend on the global open-source supply chain. All cloud computing environments are dependent on the open-source supply chain, with more than 1.5 trillion open-source component and container download requests in 2020. Unfortunately, a ‘State of the Software Supply Report,’ published by Sonatype, reported a 430% growth in next generation cyber attacks are actively targeting open-source software projects [1]. More ominously, reports in 2021 emerged claiming that Russia’s foreign espionage teams, including the APT-29 team, which led the Solarwinds attack, are now concentrating on open-source supply-chain backdoor insertions [26]. In fact, nation states don’t just target cloud technologies, they use these technologies to scale their attacks. In July, the NSA warned that Russian state-sponsored hackers were hosting new containerized cyberwarfare campaigns targeting U.S. Government and private sector [2, 14]. They warned of what brute-force password attacks that were being launched from a specially crafted Kubernetes cluster
Author
Phillip Porras is the Program Director and Internet Security Group Leader, Computer Science Lab at SRI International and the co-founder, Chief Scientist of AccuKnox. Visit www.accuknox.com or follow us on Twitter (@accuknox).
Reading List
2.https://thehackernews.com/2021/12/solarwinds-hackers-targeting-government.html
4. https://www.wiz.io/blog/chaosdb-how-we-hacked-thousands-of-azure-customers-databases#
5. https://sysdig.com/blog/muhstik-malware-botnet-analysis/
6. https://thehackernews.com/2021/09/microsoft-warns-of-cross-account.html
7. https://malpedia.caad.fkie.fraunhofer.de/details/elf.teamtnt
8. https://unit42.paloaltonetworks.com/malicious-cryptojacking-images/
10. https://sysdig.com/blog/crypto-sysrv-hello-wordpress/
12. https://www.sdxcentral.com/articles/news/worst-cyberattacks-of-2021-so-far/2021/12/
15. Software-Container Supply Chain Sees Spike in Attacks
16. https://kc.mcafee.com/corporate/index?page=content&id=KB94179
18. https://www.zdnet.com/article/omigod-azure-users-running-linux-vms-need-to-update-now/
19. https://threatpost.com/windows-containers-malware-targets-kubernetes/166692/
20. https://d2iq.com/blog/what-you-need-to-know-about-cryptomining-attacks-on-kubeflow
21. https://threatpost.com/kubernetes-cyberattacks-argo-workflows/167997/
22. https://blog.wiz.io/protecting-your-environment-from-chaosdb/
25. https://securityboulevard.com/2020/12/a-sobering-reminder-for-more-vigilant-supply-chain-security/
26. Exploring Container Security: A Storage Vulnerability Deep Dive
Now you can protect your workloads in minutes using AccuKnox, it is available to protect your Kubernetes and other cloud workloads using Kernel Native Primitives such as AppArmor, SELinux, and eBPF.
Let us know if you are seeking additional guidance in planning your cloud security program.














