
CVE-20 21-45105 Stack Overflow Error due to Recursive Lookups
Another important vulnerability CVE-20 21-45105 for Log4J was discovered. This vulnerability involves Apache Log4j2 not being able to protect from infinite recursion in lookup evaluation. This vulnerability has been upgraded in Log4J versioion 2.17.0 for Java 8 and up. The easiest way to mitigate this vulnerability is to upgrade log4j. The following details have been published […]
Reading Time: 2 minutes
Table of Contents
Another important vulnerability CVE-20 21-45105 for Log4J was discovered. This vulnerability involves Apache Log4j2 not being able to protect from infinite recursion in lookup evaluation.
This vulnerability has been upgraded in Log4J versioion 2.17.0 for Java 8 and up. The easiest way to mitigate this vulnerability is to upgrade log4j.
The following details have been published from https://logging.apache.org/log4j/2.x/index.html
Deep dive: What is this vulnerability and what kind of attack does this lead to?
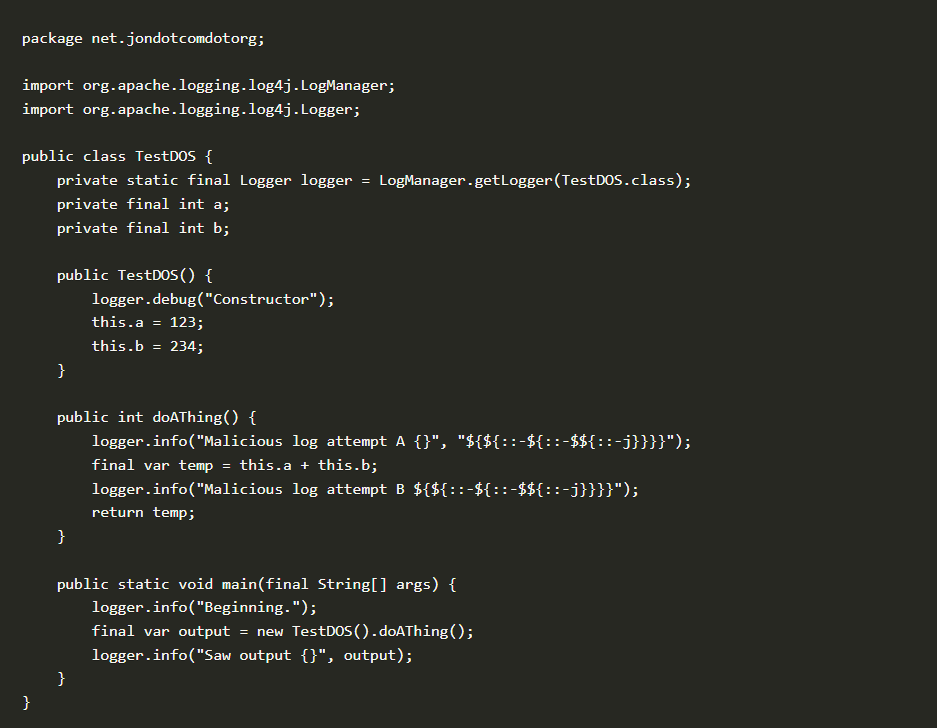
This vulnerability is a Denial of Service attack that happens through the following steps:
- Attackers craft malicious input
- If the logging configuration uses a non-default Pattern Layout with a Context Lookup (for example, $${ctx:loginId}),
- and if attackers craft malicious input
- The malicious input can cause recursive lookups
- Recursive lookups cause Denial of Service (DOS) attack to due StackOverflowError that will cause a termination of the process attacked.
Mitigation as suggested by the Log4J team:
- In PatternLayout in the logging configuration, </span >replace Context Lookups like ${ctx:loginId}or $${ctx:loginId} with Thread Context Map patterns (%X,%mdc, or %MDC).
- Otherwise, in the configuration, remove references to Context Lookups like ${ctx:loginId} or $${ctx:loginId} where they originate from sources external to the application such as HTTP headers or user input.
MDC or Mapped Diagnostic Context allows applications to log in scenarios with multiple threads and multiple simultaneous clients where mapped information can be stored for individual clients in an MDC which is a ThreadLocal. A ThreadLocal class provides thread-local variables.
The Context lookups like ${ctx:loginId}or $${ctx:loginId} lead to a recursive call with the right kind of malicious input. Details at https://issues.apache.org/jira/browse/LOG4J2-3230
Mitigating with Accuknox Open source Repo:
Apply mitigations with Accuknox’s open sourced policy repo for Log4J vulnerabilities at the following URL https://github.com/kubearmor/log4j-CVE-2021-44228
The primary approach to mitigation for this is to block any malicious input for older versions, and follow mitigations suggested by the Log4J team by disabling recursive lookups or the best solution upgrade the Log4J + Apply Accuknox policy templates on the repo at https://github.com/kubearmor/log4j-CVE-2021-44228














