
Runtime protection Virtual Machine and Bare Metal systems
Accuknox is happy to announce the alpha availability of virtual machine/ bare metal systems. With this announcement, customers will be able to use our open source tooling and apply application hardening and runtime enforcement using AppArmor / SELinux (commonly known Linux Security Modules or LSM) and eBPF (extended Berkley Packet Filter). The solution for supporting […]
Reading Time: 3 minutes
Table of Contents
Accuknox is happy to announce the alpha availability of virtual machine/ bare metal systems. With this announcement, customers will be able to use our open source tooling and apply application hardening and runtime enforcement using AppArmor / SELinux (commonly known Linux Security Modules or LSM) and eBPF (extended Berkley Packet Filter).
The solution for supporting Virtual machines and bare metal systems consists of
- KVMService – a control plane for managing virtual machines and baremetal systems
- Host Policy support – available now with both Cilium and KubeArmor. This allows us to target a virtual machine (using a label) and processes to create policies that restrict access to network and other system resources using both KubeArmor and Cilium.
- Policy discovery for Virtual Machines which now enables Cilium and KubeArmor host policies to be discovered and enforced at a particular process level.
- SELinux policy support – this allows for virtual machines with Red Hat Enterprise Linux and CentOS to be supported for Host policy Enforcement. KubeArmor policies will now work on SELinux enabled operating systems with limitations. Specific limitation includes the lack of ability to block network access for applications.
Policy Orchestration for Virtual Machines with KVMService
The KVMService is an open source project build by Accuknox and is available at https://github.com/kubearmor . The KVMService was built with the goal of orchestrating policies to virtual machine and baremetal systems using either a K8s or a non K8s control plane.
Let’s look at the initial design goals for KVMServivce
- Onboard kubearmor/cilium to virtual machines/bare-metals/edge-devices
- Orchestrate Kubearmor and Cilium policies to VMs
- Handle observability in a unified manner
- Support hybrid deployments of k8s and Virtual machine-based workloads.
- Support automated policy discovery for kubearmor/cilium for VMs
Note: Virtual Machines, Bare-Metal machines, Edge Devices will be used interchangeably in this document.
KVMService can either run as:
- K8s service + operator in k8s based control plane to support hybrid deployments
- Directly on VM/Bare-metal as systemd process to support VM / Baremetal only deployments
Hybrid Deployments
A deployment might have workloads distributed across both k8s and non-k8s (VM-based) environments. The primary aim is to support kubearmor/cilium onboarding, policy orchestration, and observability across these environments using the same toolsets. This allows simplified management of workloads for organizations who are in the midst of migrating to k8s from VMs or for those who might rely on VMs for a foreseeable future.
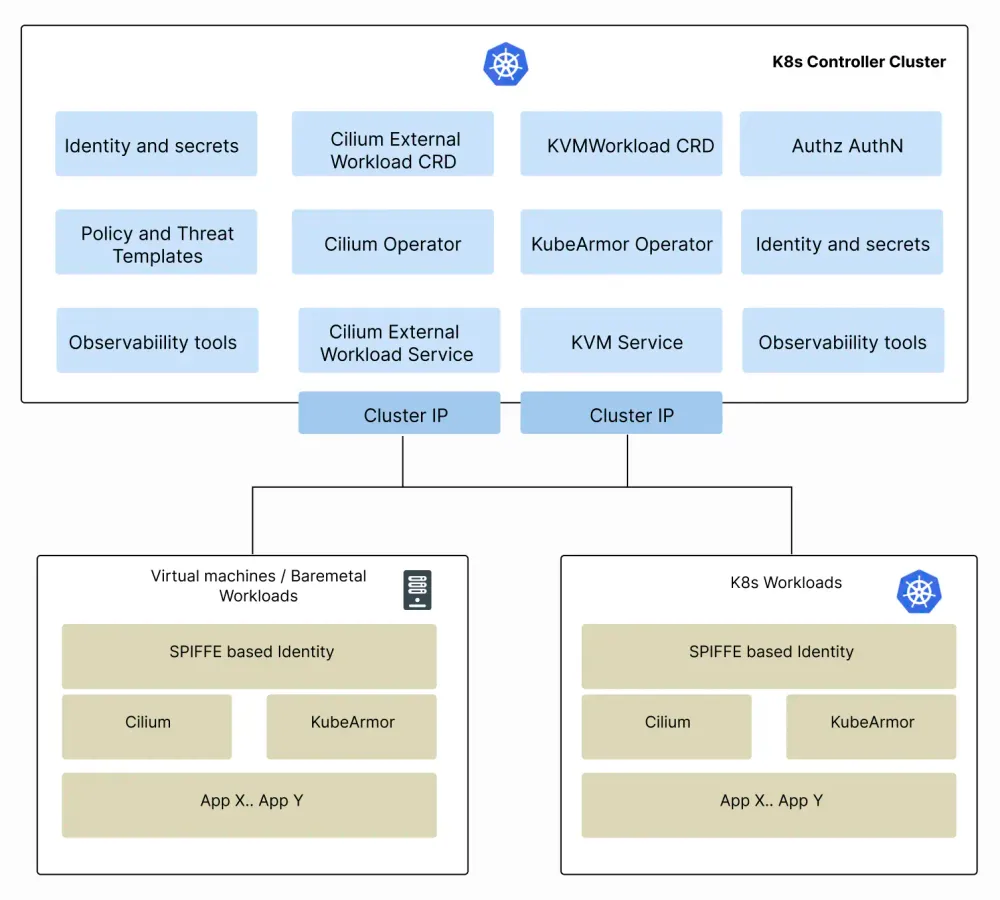
Kubernetes controller cluster
Virtual Machine / Bare Metal only deployments
There are organizations that might not support k8s for the foreseeable future and their workloads will primarily be on cloud VMs or their own data-center VMs or even bare-] metal machines. Accuknox supports VM-only deployments with KVMService enabling runtime security with boarding, policy orchestration, and observability.
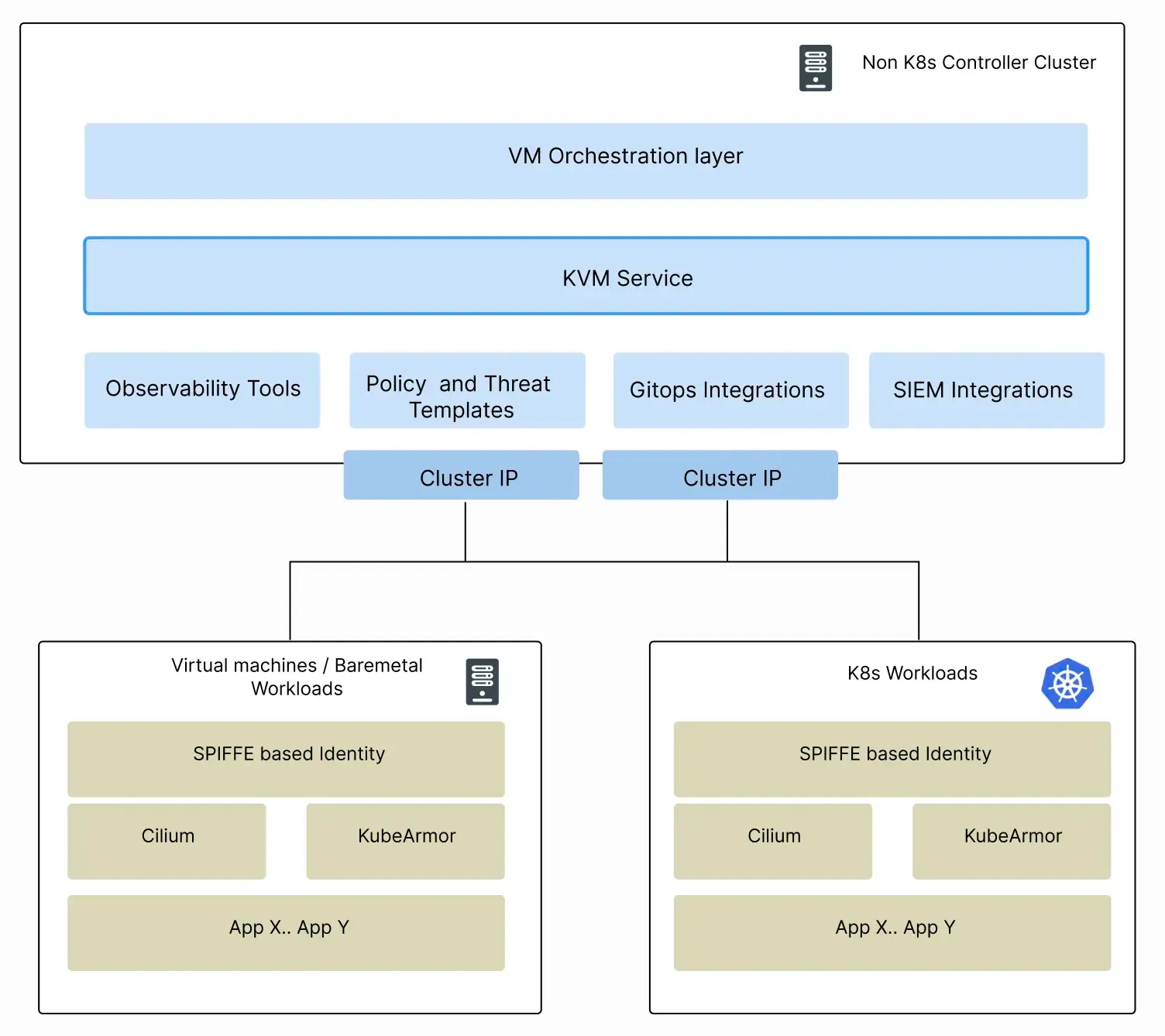
Virtual machine deployment
Additional Documents
- Deploying KubeArmor at scale on VMs using non-k8s control plane
- Google Slides for initial design discussions
Now you can protect your workloads in minutes using AccuKnox, it is available to protect your Kubernetes and other cloud workloads using Kernel Native Primitives such as AppArmor, SELinux, and eBPF.
Let us know if you are seeking additional guidance in planning your cloud security program.














