
Zero Trust: The Absolute Solution to Cloud Security Challenges
Discover the top reasons for implementing a comprehensive zero-trust cloud security strategy to overcome obstacles such as unethical behavior, data vulnerabilities, system faults, and zero-day assaults. See how this extensive strategy protects your cloud settings. This blog will address all your ZT concerns.
Reading Time: 13 minutes
Table of Contents
The evolution of cloud technology in the modern digital environment has fundamentally changed how organizations run. Although the cloud provides unmatched flexibility and scalability, it also introduces a whole set of security issues of various kinds. Traditional perimeter-based security methods prove to be insufficient in defending against sophisticated attacks and breaches when enterprises move their crucial applications and sensitive data to the cloud.
💡TL;DR
- The “never trust, always verify” maxim is prioritized in the zero trust cloud security strategy, which views users, devices, and apps as potentially dangerous entities.
- It overcomes the drawbacks of conventional perimeter-based security solutions, including insider threats and data breaches.
- Streamline application hardening, firewalling, and policy generation to achieve Zero trust or least privilege security for cloud-native applications.
- AccuKnox provides sophisticated threat detection, adaptable integration possibilities, and adherence to CyberSecurity standards (eg. app whitelisting). This limits unauthorized software execution and lessens malware infections.
Enter Zero Trust, the revolutionary approach that is redefining cloud security. Unlike the traditional security model that relies on implicit trust within the cloud network, Zero Trust operates on the principle of “never trust, always verify.” With Zero Trust, every user, device, and application is treated as a potentially untrusted entity, regardless of its location or network privilege. Hence, it’s essential to have a careful whitelisting of what is absolutely needed by your application to run and deny everything else.
Remember, in the realm of cloud security, trust is no longer enough. It’s time to embrace Zero Trust and unlock a new level of protection, resilience, and peace of mind.
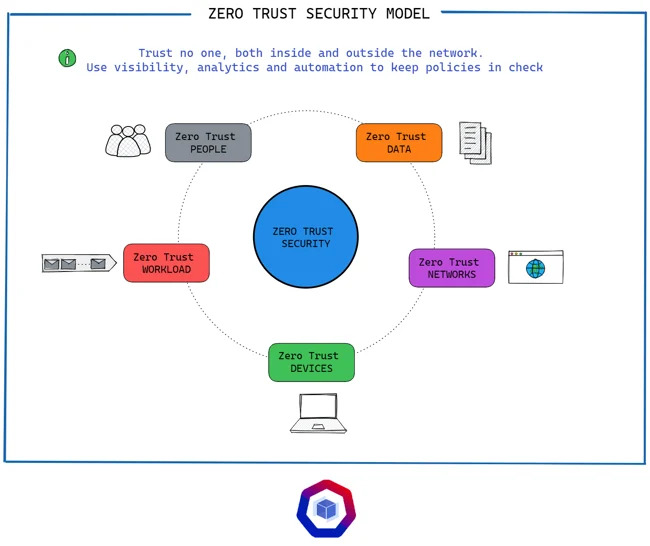
The Challenges of Cloud Security
Let us delve into the critical challenges faced by cloud security by uncovering the limitations of the traditional perimeter-based security model and its inability to address the dynamic nature of the cloud. You will discover the unique security challenges that arise in cloud environments, such as data breaches, misconfigurations, and insider threats. With cloud modernization, there is a requirement to discover an approach that transforms cloud security, providing formidable state of the art solutions that empower you to effectively safeguard your valuable cloud assets.
The Limitations of Traditional Perimeter-Based Security
The rapid adoption of cloud computing has brought numerous benefits to organizations, such as scalability, cost-efficiency, and enhanced collaboration. However, it has also introduced a new set of security challenges that traditional perimeter-based security models are ill-equipped to handle.
According to a study by Gartner, “Through 2025, 99% of cloud security failures will be the customer’s fault.” This highlights the importance of organizations understanding and implementing appropriate security measures in the cloud environment.One of the limitations of traditional security approaches lies in their reliance on a network perimeter as the primary line of defense. In cloud environments, the perimeter is no longer well-defined, as data and applications reside across multiple platforms, networks, and devices. This makes it difficult to establish a clear boundary and defend against external threats.
The National Institute of Standards and Technology (NIST) defines a network perimeter as “the boundary between an organization’s internal network and an external network.” In the context of cloud computing, the perimeter becomes more fluid and dynamic.
Uniqueness of Cloud Security Challenges
Cloud environments are highly dynamic, with resources being provisioned, scaled, and decommissioned on demand. This agility, while beneficial for business operations, makes it challenging to maintain consistent security controls and visibility across the entire infrastructure.
In a survey conducted by McAfee, it was revealed that 65% of 1,400 IT professionals across 11 countries reported that their organization adopts a “cloud-first” approach. The findings highlight the prevalent trend of prioritizing cloud solutions and strategies in the technology landscape, as organizations recognize the advantages and opportunities offered by cloud computing.
Additionally, the shared responsibility model of cloud providers introduces complexities. While the cloud provider ensures the security of the underlying infrastructure, the organization is responsible for securing its data, applications, and access controls. Failure to understand and implement the necessary security measures can result in vulnerabilities and potential breaches.
Adapting to the Cloud: Embracing a New Security Paradigm
As stated by the Cloud Security Alliance (CSA), “Organizations using cloud services should understand the shared responsibility model and their own responsibilities within that model”. This emphasizes the need for organizations to actively manage their cloud security.
John Kindervag, the creator of the Zero Trust model, defined it as “never trust, always verify”.
This principle underscores the importance of continuous verification and authentication within the cloud environment as a Zero Trust approach.
These challenges highlight the need for a new approach to cloud security: Zero Trust. It recognizes that trust cannot be assumed, even within the network perimeter. It requires verifying every user, device, and application attempting to access resources regardless of their location or network access. Implementing Zero Trust principles enables companies to mitigate the risks associated with cloud security challenges and strengthen their overall security posture.
💡Discover how AccuKnox can simplify and automate the process of achieving Zero Trust/Least Privilege Security for your cloud native applications. Streamline application hardening, firewalling, and policy creation with our unique insights and automated policy discovery engines. Start enhancing your security posture today with AccuKnox’s comprehensive solution.
Understanding Zero Trust Security
This section explores the underlying concepts of zero trust security, explains their significance, and demonstrates how they differ significantly from conventional approaches. You will look at the underlying principles that underpin this novel methodology and help businesses build robust defenses. Also shown are the incredible benefits that Zero Trust Security offers cloud environments, providing enhanced security and reinforced trust.
What is Zero Trust Security?
An approach to cybersecurity known as “Zero Trust Security” questions the conventional notion of presuming trust within the network perimeter. Regardless of their location or network connectivity, it necessitates checking and validating each person, device, and program trying to access resources.
The Zero Trust model operates on the principle of “never trust, always verify,” emphasizing the importance of continuous authentication and authorization.
Contrasting Zero Trust Security with Traditional Models
Traditional security models rely on the concept of a trusted network perimeter, where once inside, users and devices are considered trusted. However, this approach is no longer effective in cloud environments, where resources are distributed across multiple platforms and networks.
It shifts the focus from a perimeter-centric approach to an identity-centric approach, where access decisions are based on the identity and security posture of the user or device, rather than their location or network.
Core Principles of Zero Trust Security
Zero Trust Security is built on several core principles that guide its implementation:
- Least Privilege: Users and devices are granted the minimum level of access necessary to perform their tasks, reducing the attack surface and limiting the potential impact of a breach
- Micro-Segmentation: Networks are divided into smaller, isolated segments, allowing granular control over access and limiting lateral movement in case of a breach
- Continuous Authentication: Users and devices are continuously authenticated and their access is dynamically evaluated based on risk factors, such as user behavior and device health
Benefits of Zero Trust Security in Cloud Environments
- Enhanced Security: It provides a more robust and proactive defense against cyber threats by ensuring that only authenticated and authorized entities access resources
- Improved Compliance: With its granular control and continuous monitoring capabilities, Zero Trust Security helps organizations meet compliance requirements by effectively managing access controls and data protection
- Flexibility and Scalability: It is usually applied to dynamic cloud environments, allowing companies to scale their infrastructure while maintaining consistent security controls
💡 Implement Zero Trust security in the cloud with AccuKnox®. Secure your workloads across major cloud platforms, modern or legacy, with our comprehensive solution. Benefit from advanced threat detection, flexible integration options, and compliance with top Cloud CyberSecurity guidelines. Experience the power of AccuKnox in action – request a demo today.
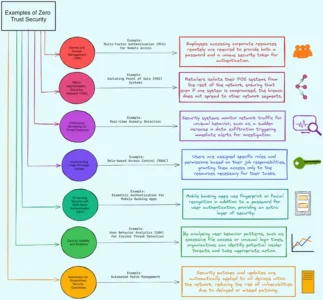
Key Components of Zero Trust Security
Let’s explore all the components of Zero Trust Security that work together to create a robust and comprehensive security framework.
Application Whitelisting
- Application Whitelisting is a security practice that allows only approved applications to run on a system, blocking unauthorized or malicious software.
- It creates a defined list, or “whitelist,” of trusted applications that are permitted to execute, while denying all others.
- By implementing Application Whitelisting, organizations can significantly reduce the attack surface and mitigate the risk of malware infections.
- Example: Imagine a company deploying Application Whitelisting on its employee workstations, allowing only approved business applications to run. This prevents the execution of unauthorized software or potential threats, enhancing overall system security.
Application Hardening
- This involves strengthening the security of an application by minimizing vulnerabilities and reducing its attack surface.
- It typically involves techniques like removing unnecessary features, implementing code obfuscation, enabling runtime application self-protection (RASP), and applying patches and updates.
- Application Hardening enhances an application’s resilience against common attack vectors, such as code injection, buffer overflows, and cross-site scripting (XSS), hence preventing unauthorized access, data breaches, and compromises of application integrity.
While Application Whitelisting focuses on controlling the execution of approved applications, Application Hardening strengthens the security of those applications, reducing the likelihood of successful attacks. Combining Application Whitelisting and Application Hardening is a vital step in enforcing the Zero Trust Security approach.
Identity and Access Management (IAM)
- IAM ensures that only authorized individuals or entities can access resources and has strong authentication mechanisms, such as multi-factor authentication (MFA) and identity verification, to establish trust before granting access.
- As the saying goes, “Identity is the new perimeter.” By focusing on identity, organizations can effectively control access and mitigate the risks associated with unauthorized access attempts.
Micro-Segmentation: Securing Network Traffic
- It involves dividing the network into smaller, isolated segments to limit the lateral movement of threats. Each segment has its security policies, allowing enterprises to enforce stricter controls and reduce the impact of a potential breach.
- With micro-segmentation, businesses can compartmentalize critical assets, applications, and sensitive data, preventing unauthorized access and containing potential threats.
Continuous Monitoring for Threat Detection
- Continuous monitoring detects and responds to threats in real time. By collecting and analyzing security events, companies can identify suspicious activities, anomalies, or potential breaches.
- Proactive monitoring enables timely incident response and helps you to stay one step ahead of attackers. It involves leveraging security information and event management (SIEM) tools, intrusion detection systems (IDS), and user behavior analytics (UBA).
Implementing Least Privilege Access
- The principle of least privilege ensures that users and devices are granted only the minimum level of access necessary to perform their tasks. By limiting privileges, corporations can reduce the attack surface and minimize the potential impact of a compromised account or device.
- Adopting a least privilege approach requires evaluating user roles, conducting access reviews, and implementing strong access control mechanisms.
Enhancing Security with Multi-Factor Authentication (MFA)
- MFA adds an extra layer of security by requiring users to provide multiple forms of authentication, such as passwords, biometrics, or security tokens, hence significantly reducing the risk of unauthorized access, even if one factor is compromised.
- This enables organizations to strengthen their authentication processes and protect sensitive data from unauthorized individuals.
Gaining Visibility and Analytics
- To effectively secure the environment, enterprises need visibility into network traffic, user behavior, and security events. This visibility allows for better threat detection, incident response, and policy enforcement.
- Leveraging advanced analytics and visibility tools, businesses can identify patterns, detect anomalies, and gain actionable insights to improve their security posture.
Automation for Streamlined Security Operations
- Automation plays a crucial role in Zero Trust Security by streamlining security operations and reducing human errors. It involves automating tasks such as provisioning, policy enforcement, incident response, and security orchestration.
- By automating repetitive and time-consuming tasks, security teams can focus on more strategic initiatives and respond rapidly to emerging threats.
Implementing Zero Trust Security in the Cloud
Implementing Zero Trust Security in the cloud requires careful planning and adherence to best practices. By following a systematic approach and addressing common challenges, institutions can successfully enhance their cloud security posture.
Steps to Implementing Zero Trust Security
| Step | Description | Example |
| Assess Current Environment | Evaluate the existing security infrastructure, identify vulnerabilities, and understand cloud-specific requirements. | Conduct a security audit to assess network configurations, identify outdated software, and detect potential entry points. |
| Define Security Policies | Establish comprehensive security policies aligned with Zero Trust principles, including user roles and access controls. | Define user groups and permissions based on job responsibilities and enforce strong password policies. |
| Implement IAM | Deploy robust Identity and Access Management solutions to manage user identities and enforce strong authentication. | Utilize a centralized identity provider to authenticate users and enable multi-factor authentication (MFA) for added security. |
| Segment Your Network | Implement micro-segmentation techniques to isolate critical assets and restrict access based on the principle of least privilege. | Segregate sensitive databases into separate network segments, applying strict access controls and encryption. |
| Continuous Monitoring and Threat Detection | Implement real-time monitoring tools to detect anomalies, identify potential threats, and enable prompt incident response. | Utilize intrusion detection systems (IDS) and security information and event management (SIEM) tools to monitor network traffic and detect suspicious behavior. |
Overcoming Common Challenges During Implementation
- Lack of Visibility: Ensure complete visibility into network traffic, user activities, and security events through advanced analytics and monitoring tools.
- Legacy System Compatibility: Address compatibility issues between legacy systems and Zero Trust security solutions by leveraging APIs and integration frameworks.
- User Adoption and Training: Provide comprehensive training and education to users, administrators, and stakeholders to foster understanding and acceptance of Zero Trust principles.
Best Practices for Successful Zero Trust Security in the Cloud
- Emphasize Automation: Leverage automation to streamline security operations, including provisioning, policy enforcement, and incident response, to reduce human errors and enhance efficiency.
- Regular Auditing and Updates: Conduct periodic audits to identify gaps in security controls and promptly apply updates and patches to mitigate vulnerabilities.
- Collaboration and Communication: Foster collaboration between IT, security teams, and stakeholders to ensure alignment and effective implementation of Zero Trust practices.
- Continual Evaluation and Improvement: Regularly assess the effectiveness of your Zero Trust security measures, adapt to evolving threats, and incorporate new technologies and best practices.
Zero Trust Cloud Security Use Cases
Discover the power of Zero Trust Security, a highly fortified strategy that offers complete protection and seamless control over your cloud assets. You will come to appreciate its versatility as we delve into real-world use cases, including safeguarding remote workers, securing edge workloads, protecting cloud-based IoT devices, fortifying the 5G Control Plane and xApps, and ensuring the security of containerized applications. In this section, we will showcase compelling reasons to adopt AccuKnox’s Zero Trust policies, creating a resilient and secure cloud environment that meets the evolving demands of the modern digital landscape.
Zero Trust Security in Multi-Cloud Environments
Businesses are faced with the difficulty of safeguarding their data and apps across many cloud platforms as multi-cloud architectures are increasingly adopted. By putting Zero Trust Security into practice, enterprises can maintain a cohesive and secure environment by ensuring uniform security policies and controls across various cloud providers. For instance, regardless of the cloud provider, a business may utilize Zero Trust principles to authenticate and approve user access to resources hosted on AWS, Azure, and Google Cloud Platform.
Ensuring Zero Trust Security for Remote Workers
As remote work becomes more prevalent, businesses need to ensure that employees accessing corporate resources remotely are subject to the same stringent security measures as those on premises. Zero Trust Security provides a framework to authenticate and authorize remote workers, enforce access controls, and monitor their activities. For instance, a company might require remote workers to utilize multi-factor authentication and VPNs to establish secure connections and grant access only to authorized resources.

Zero Trust Security for Edge Workload
This can be done effectively by implementing granular access controls, continuous monitoring, and authentication mechanisms. It enables organizations to enforce strict security policies for edge devices, preventing unauthorized access and mitigating the risk of potential breaches.
Example: Think of a manufacturing company that uses edge computing to monitor production systems in real-time. They can protect crucial production data and uphold operational resilience by implementing Zero Trust Security to make sure that only authorized users and devices can access and interact with the edge workloads.
Zero Trust Security for 5G Control Plane and Securing xApps
Zero Trust Security provides a comprehensive approach to protect the 5G Control Plane, which manages critical network functions, and securing xApps that leverage the 5G infrastructure. It involves implementing robust authentication, encryption, and access controls to safeguard the integrity and confidentiality of network communications and applications.
Example: In the telecommunications industry, a mobile network operator implementing Zero Trust Security for the 5G Control Plane and securing xApps can ensure that only authorized entities and applications can access and utilize the network resources, mitigating the risk of unauthorized network access or malicious activities.
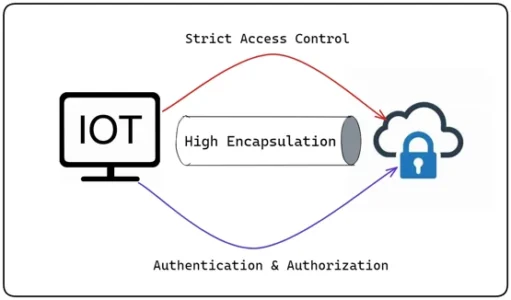
Securing IoT Devices in the Cloud with Zero Trust
The proliferation of IoT devices introduces new security risks, as these devices often have limited security features and may act as potential entry points for cyberattacks. Zero Trust Security helps mitigate these risks by enforcing strict access controls, authenticating and authorizing IoT devices, and monitoring their behavior. For example, a smart manufacturing facility may implement Zero Trust principles to ensure that only authorized IoT devices can connect to the cloud platform and access critical systems and data.
Zero Trust Security for Containerized Applications
Containerization has revolutionized application deployment, but it also requires robust security measures. Zero Trust Security provides granular access controls and monitors containerized applications to prevent unauthorized access and data breaches. For instance, an organization using Kubernetes for container orchestration can implement Zero Trust Security to authenticate and authorize containers, ensure the least privilege access, and monitor for any suspicious activities or vulnerabilities.

KubeArmor helps instantiate Zero Trust security posture at the system level; i.e., it understands the application’s behavior and enforces “allow” based policies and denies everything else. As an example, KubeArmor can allow only a specific set of processes to be executed within the pod and deny everything else such that when an unknown binary is attempted, that execution is denied. One can apply similar constraints at file system paths, volume mount points, and for socket primitives as well.
Other Use Cases
Zero Trust Security extends beyond the aforementioned scenarios and can be applied while securing data in cloud storage services, protecting cloud-based collaboration tools, ensuring secure access to serverless functions, and more. Companies across industries can leverage Zero Trust principles to address their specific cloud security requirements and mitigate evolving threats.
Conclusion
As businesses navigate the complexities of cloud security, Zero Trust stands out as the ultimate solution to address the evolving landscape of threats. By shifting from traditional perimeter-based approaches to a Zero Trust framework, organizations can establish granular control, strong authentication, and continuous monitoring. This comprehensive and proactive approach mitigates risks, protects sensitive data, and ensures the integrity of cloud environments. With Zero Trust, enterprises can embrace the benefits of the cloud while safeguarding their assets and empowering secure and resilient operations. It’s time to embrace Zero Trust as the ultimate solution for cloud security challenges.
💡Unlock the full potential of Zero Trust Security with AccuKnox®. Whether it’s securing cloud storage, protecting collaboration tools, or ensuring secure access to serverless functions, our solution has you covered. Take control of your cloud security and mitigate evolving threats. Explore our solutions to learn how AccuKnox can safeguard your organization’s cloud infrastructure.














