Kubernetes Professional Services
Kubernetes is at the core of the cloud native movement. AccuKnox consults and provides services for Kubernetes pods, clusters, containers to make cloud native deployment safe and resilient against advanced attacks.
REQUEST QUOTE
Top Reasons to Avail Kubernetes Services
- Helps professionals gain the knowledge and skills needed to excel in cloud security.
- Well-detailed modules with practical examples.
- Teaches how to secure cloud accounts, Kubernetes clusters, and container registries using AccuKnox’s state-of-the-art security solutions.


How to Achieve Zero Trust Cloud Security Posture
We Provide Tailored Kubernetes Security Services
| Check the Kubernetes API server’s TLS certificate expiration date to ensure secure communication. | |
| Scan the Kubernetes cluster for vulnerabilities using tools like kube-bench. | |
| Check the security configuration of Kubernetes deployments to identify potential risks. | |
| Audit the Kubernetes cluster configuration to ensure compliance with security standards. | |
| Scan container images for vulnerabilities using tools like Trivy. | |
| Verify Kubernetes resource manifests to ensure they adhere to security policies. | |
| Check Kubernetes API server and controller-manager logs for suspicious activity. | |
| Restrict Kubernetes API access using Role-Based Access Control (RBAC) to enforce the principle of least privilege. | |
| Enforce pod security policies with the admission controller to manage pod creation and access. | |
| Use network policies to restrict network access to pods, enhancing security through microsegmentation. | |
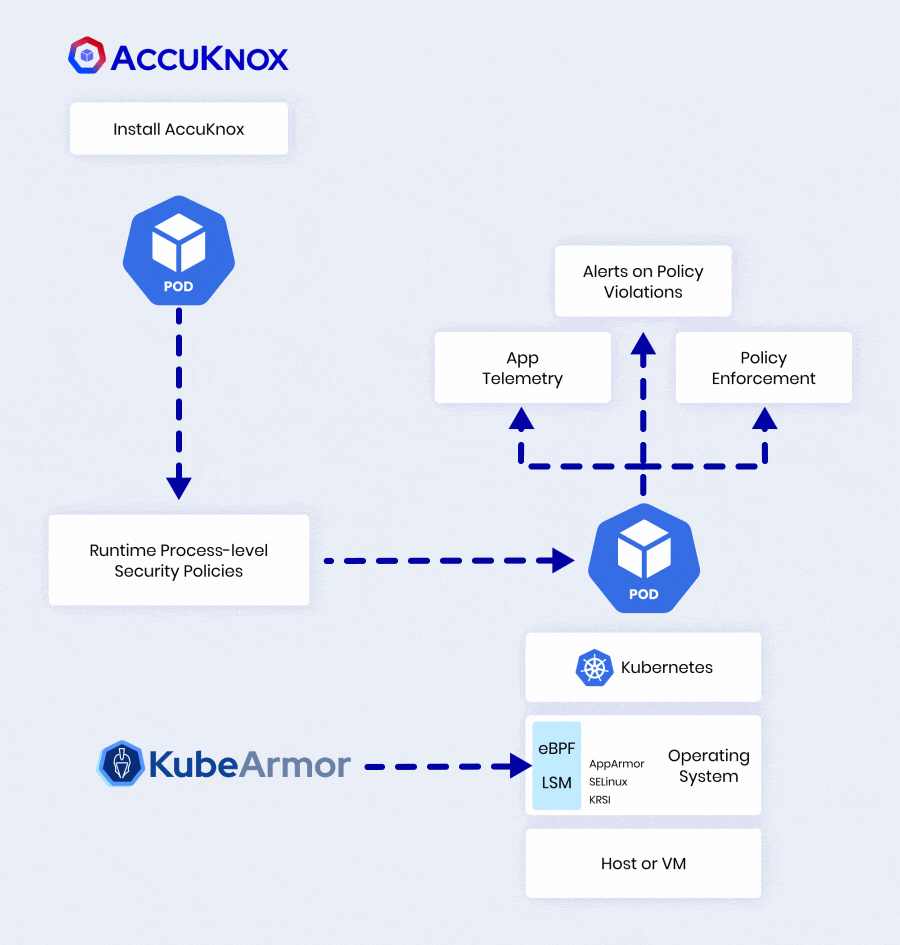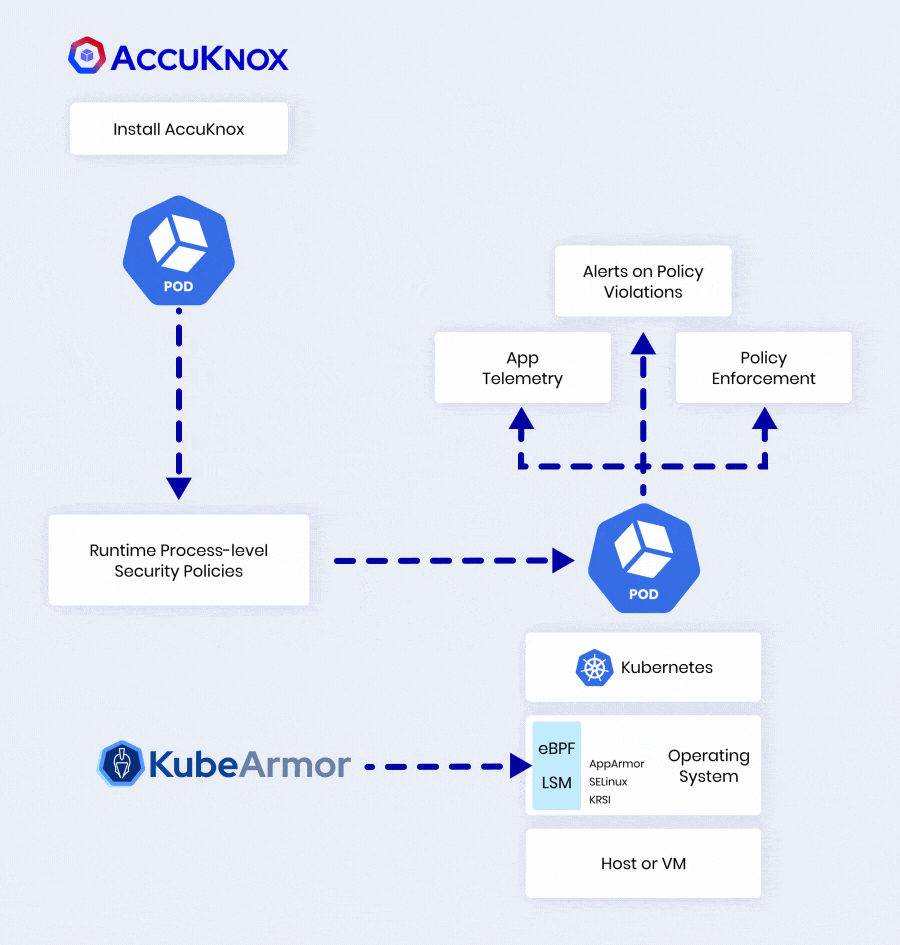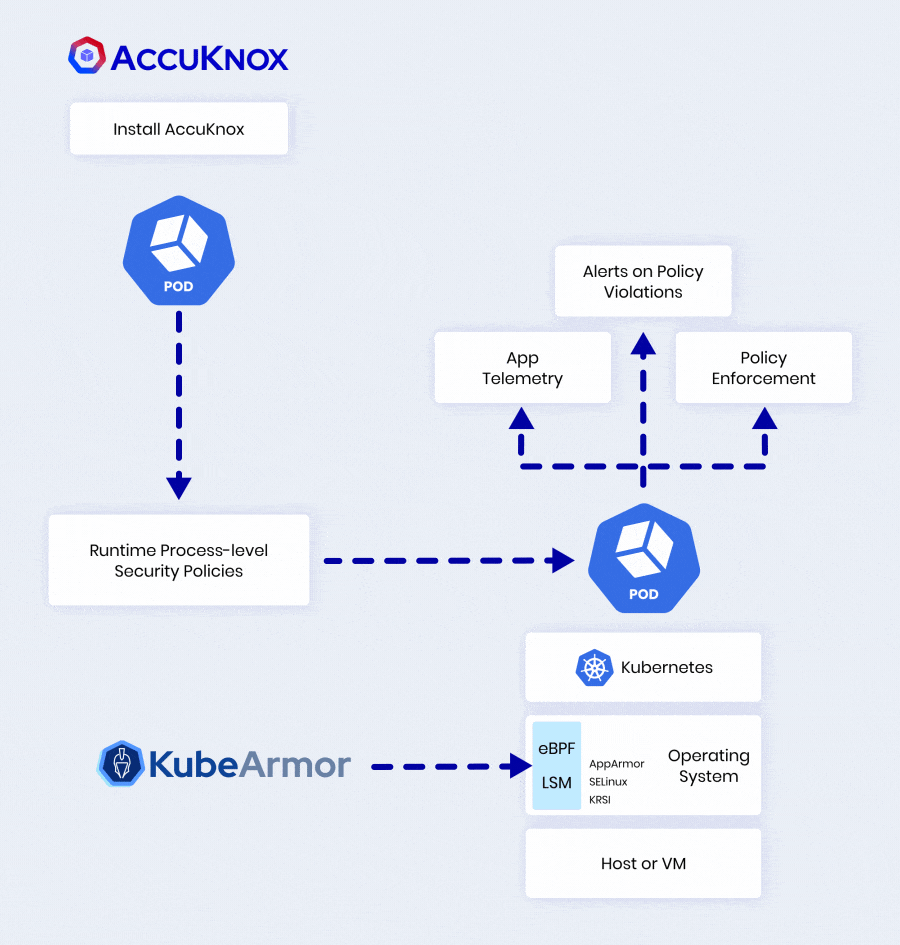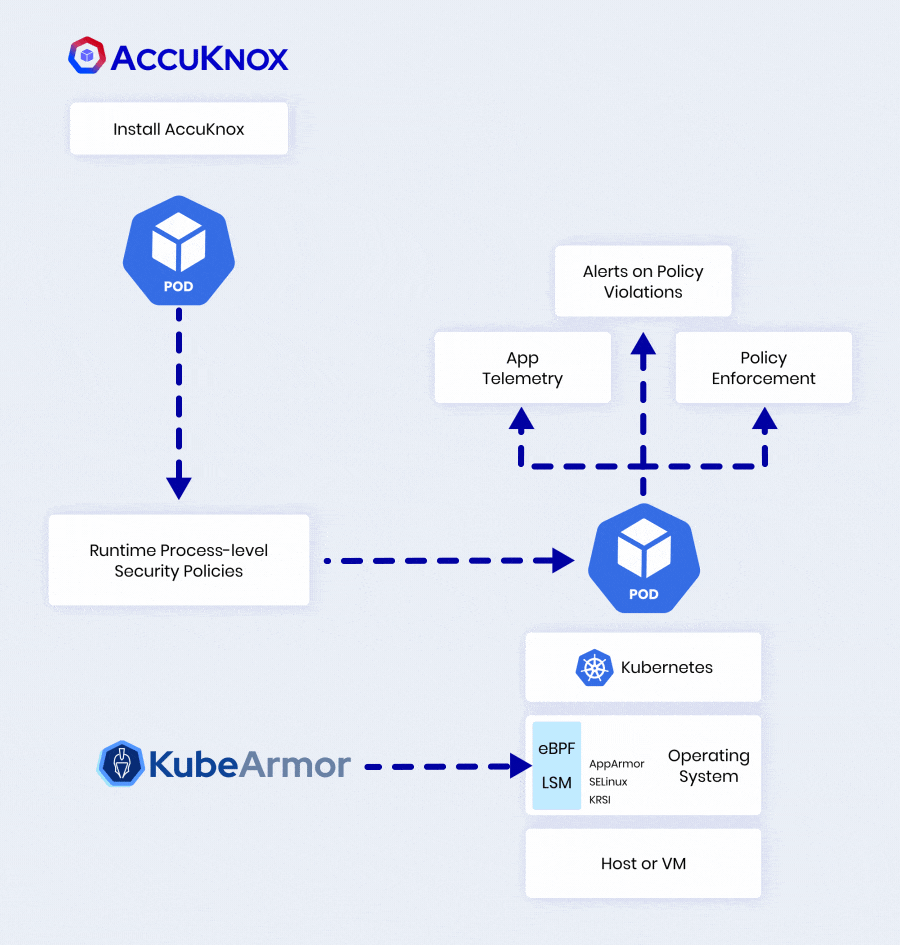
| Control execute, chroot, pivot_root, place | |
| Manage read/write operations on files, dirs, sockets | |
| Regulate connect, listen, accept on IP, port, protocol | |
| Identify privilege escalations, breakouts, crypto mining | |
| MITRE ATT&CK mapping, detailed audit trails |
Industry Best
Kubernetes Professional Services Pricing
 Professional Services Professional Services |
||||||
| Pricing | Volume based discount | |||||
| TIER | STARTER | DEPARTMENT | DIVISION | ENTERPRISE | CUSTOM | |
| Per Month | $1,000 | $2,500 | Contact Sales | |||
| Upto # Nodes | 100 | 250 | ||||
| Per Node Price | $10.00 | $10.00 | ||||
AccuKnox Leverages KubeArmor To Deliver 360° Security