API Security – Protect Cloud APIs with AccuKnox's Zero Trust CNAPP
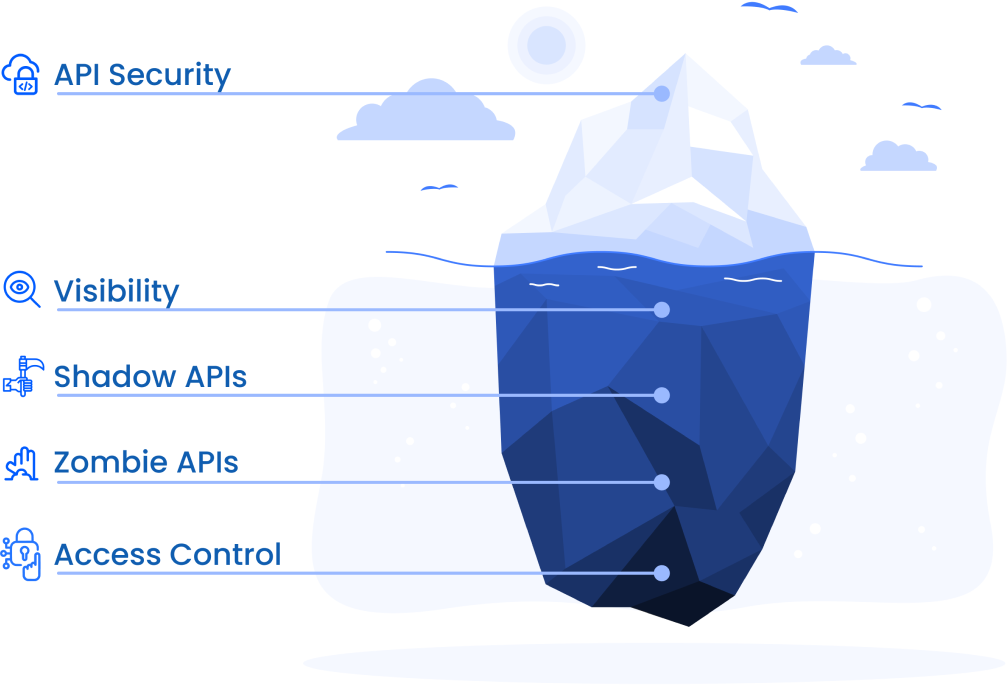
Deep visibility into APIs, detecting shadow and zombie APIs while ensuring least-permissive access. Secure API ecosystem with integrated onboarding and runtime AI/ML access.
Book a Demo
Here’s Why You Need API Security
- Lack of comprehensive API visibility, leading to security blind spots.
- Shadow and zombie APIs expose organizations to hidden attack surfaces.
- Weak API access controls undermine Zero Trust principles and AI/ML security.
AI-enhanced attacks top the list of the biggest percieved threats to API security today, followed by unauthorized access/breaches and insufficient data protection/encryption
74%
are very concerned about AI-enhanced attacks
92%
are taking measures to counter AI-enhanced attacks
40%
aren’t confident in their current security investments
API Discovery, Monitoring & Security -The Zero Trust Way
Runtime API Security
- Uses service mesh sidecars or proxies to inspect secure traffic and detect anomalies.
- Exports API instrumentation data in OpenTelemetry format for seamless monitoring.
- Identifies access patterns with a discovery engine and provides a SaaS or on-prem control plane for management.
Static API Security
- Scans code repositories and analyzes API specs (OpenAPI, Swagger, WSDL) for security gaps.
- Extracts endpoint details, peer connections, and access requirements for better enforcement.
- Integrates into CI/CD pipelines to detect and mitigate risks before deployment.
Support Across All Workloads & Environments
| Category | Support Details |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
Enterprise Grade API Security Use Cases
API Discovery & Traffic Analysis
- Discover service-to-service communication, shadow/zombie APIs, and internal/external API access using platform abstractions (e.g., Kubernetes).
- Capture and inspect traffic metadata for empirical analysis and compliance.
API Performance & Monitoring
- Track API access metrics (latency, success rate) and protect against OWASP Web & API attacks using traffic signatures.
DoS Attack & TLS Security
- Detect and mitigate DoS attacks early with eBPF XDP.
- Identify TLS/certificate misconfigurations and manage secure connections with tools like “k8tls.”
Authentication & Sensitive Data Protection
- Identify brute force authentication attempts and detect sensitive data exposure in API responses.
Fault Injection & Deployment Support
- Perform chaos testing and fault injection.
- Support Kubernetes and non-Kubernetes deployments with compatibility for Nginx, Istio, Mule, and Kong ingress controllers/gateways.
You Bring The Infrastructure,
We Bring the Security

Why DevSecOps and Security Teams Love our AppSec Platform?


“AccuKnox offers us the protection we need for our cloud infrastructure, while ModelKnox ensures that our AI assets remain secure and resilient against evolving threats.”
Utku Kaynar
CEO


“At Prudent, we advocate for a comprehensive end-to-end methodology in application and cloud security. AccuKnox excelled in all areas in our in depth evaluation.”
Manoj Kern
CIO


“Choosing AccuKnox was driven by opensource KubeArmor’s novel use of eBPF and LSM technologies, delivering runtime security”
Golan Ben-Oni
Chief Information Officer


“As 5G starts getting broad industry adoption, security is a very critical challenge. It is delightful to see an amazing innovator like SRI work with AccuKnox to deliver critical innovations”
Jim Brisimitzis
General Partner


“The discovery process is crucial to making drug discovery faster, smarter, and secure. We are pleased to partner with AccuKnox for their AI Security prowesses”
Matt Shlosberg
Chief Operating Officer


“AccuKnox very strong and Enterprise offering coupled with a strong roadmap of securing AI/LLM Models made them a compelling choice”
Rahul Saxena
Co-founder, Chief Product & Technology Officer

“AccuKnox does a tremendous job at showing the complexity of different approaches to Kubernetes security in terms of responding to high severity cloud attacks”
James Berthoty
Founder & Security Analyst


“We were able to work with a pioneer in Zero Trust Security. Tible is committed to delivering comprehensive security, compliance, and governance for all of its stakeholders”
Merijn Boom
Managing Director












