Zero Trust Security Solutions

AccuKnox is the top CNAPP Security Pick
Unique Differentiators
- AI-Powered Security Intelligence
- Platform Approach (50+ Security Tools Integrations)
- Consume/Deploy Anywhere (OnPrem & SaaS)
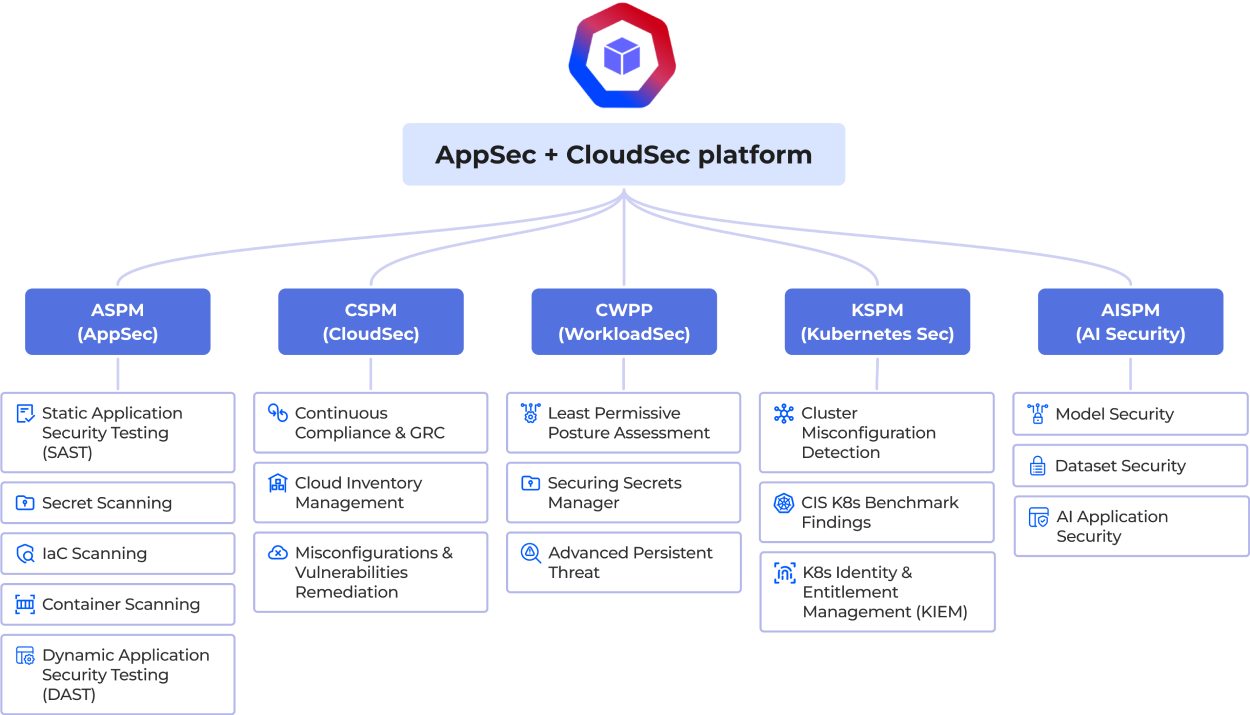

How to Achieve Full Transparency of your Cloud Security Posture
Single AppSec + CloudSec Platform: Consolidated Visbility of ongoing threats
Cloud Security
Asset Inventory
Graphical view of asset findings, count, and types
Misconfigurations & Drift Detection
Detect drifts during pre and post production deployments
Continuous Compliance
Dynamic approach to fortifying networks and systems
Cloud Detection and Response (CDR)
Defend against cloud account compromises and insider threats
Workload Security
Admission Controller Security
Runtime detection to assess attacks and unusual behavior
Zero Trust Runtime Security
Whitelist and block system events at runtime kernel layer
Container and VM Forensics
Visualize granular logs to investigate attack scenario
Automated Zero Trust Policy Enforcement
Apply, update, and delete policies automatically
Application Behavior Modeling
Automatically discover application posture during runtime
Application Security
Static Application Security Testing (SAST)
Identify code vulnerabilities during software development
Dynamic Application Security Testing (DAST)
Integrate runtime findings with ticketing tools
Vulnerability Management
Advanced threat remediation with grouping, sorting and filtering
CI/CD Pipeline Security
Automate scanning CI pipeline for critical vulnerabilities
Software Composition Analysis
Advanced monitoring and attack defense for third party dependencies
Safeguard AI models with advanced defenses
AI/ML Security
- Untrusted Model Sandboxing
Constrains model execution within secure environments. - Preemptive Threat Mitigation
Blocks cryptomining, command injections, and GPU misuse. - Adversarial Attack Defense
Protects AI models from adversarial and injection attacks.
Simplify cloud compliance, eliminate risks
CloudSec Posture Management(CSPM)
- Automated Asset Inventory
Discover and categorize cloud resources effortlessly. - Drift Detection
Monitor and track configuration changes in real-time. - Continuous Compliance
Ensure adherence to 30+ frameworks across multi-cloud environments.
Shield workloads across hybrid clouds
Zero Trust Driven Workload Protection (CWPP)
- eBPF-Based Monitoring
Real-time kernel-level visibility and attack prevention. - Granular Access Control
Restrict processes, file systems, and network connections. - Zero-Day Mitigation
Proactive defense against unknown and emerging threats.
Integrate security into development pipelines
DevSecOps AppSec Solutions
- Agentless Scanning
Runs efficient scans without additional installations or disruptions. - CI/CD Integration
Embeds seamlessly into pipelines for automated security checks. - Unified Dashboard
Centralized insights for vulnerabilities, misconfigurations, and compliance.
Ensure Kubernetes configurations remain secure
Kubernetes Security PostureManagement (KSPM)
- Cluster Misconfiguration Detection
Identify and remediate insecure Kubernetes configuration issues. - CIS Benchmark Compliance
Automate compliance checks against Kubernetes industry standards. - Identity Management
Control Kubernetes resource access with secure, auditable permissions.
Uncompromising Zero Trust Security Every Step of the Way
VM, OnPrem and Airgapped Deployment Modes
- Cloud Misconfiguration Fixes
Identifies and resolves risks in virtualized environments. - Host Hardening
Reduces attack surfaces with industry-standard security practices. - Compliance Benchmarking
Ensures adherence to STIGs, CIS, and regulatory standards.
Protect Connected Devices & 5G Networks At Every Layer
5G & IoT/Edge Security
- Live RF Threat Monitoring
Real-time detection of RF-based attacks and anomalies. - xApp and RIC Policy Compliance
Auto-generates YAML policies for secure configurations. - Runtime Compliance Enforcement
Continuous monitoring to prevent security breaches in real time.
Let AccuKnox perform impact analysis and security posture
While your security teams are at work, having the automation and visibility becomes more harder as the platform becomes vulnerable. AccuKnox’s Security Suite performs the scans rapidly and integrates with 50+ tooling out of the box! Solving the visibility, observability and enforcement problems at scale.
Customer Reviews

AccuKnox is the best example of how to achieve NIST & MITRE conformance out-of-the-box. The team has done a great job of simplifying security concepts from the scratch, I highly recommend it to Kubernetes practitioners”

Scott Surovich
Principal Engineer - Global Container Engineering Lead


Kubernetes is the de facto Cloud Operating System, yet securing it efficiently and effectively presents a wide-ranging challenge. AccuKnox has been instrumental in bringing defense to unknown attacks at real-time”

Andrew Martin
CISO & CEO

AccuKnox is a must-try for every Cloud Native security engineer in Zero Trust Journey. With 1 Million+ KubeArmor downloads, the open-source tool chest is very helpful for Kubernetes runtime protection”

Gnanavelkandan Kathirvel
Head of Product
Google Distributed Cloud

AiDash was looking for a Comprehensive Cloud Native Security platform that spans Application Security and Cloud Security. AccuKnox’s very strong and Enterprise offering coupled with a strong roadmap of securing AI/LLM Models made them a compelling choice”

Rahul Saxena
Co-Founder, Chief Product & Technology Officer


Thanks to our existing partnership with AccuKnox, we were able to work with a pioneer in Zero Trust Security. Tible is committed to delivering comprehensive security, compliance, and governance for all of its stakeholders”

Merijn Boom
Managing Director


AccuKnox does a tremendous job at showing the complexity of different approaches to Kubernetes security in terms of the speed of sending a response against emerging CVEs and unknown cloud attacks”

James Berthoty
Founder & Security Analyst
FAQs
AccuKnox scans container images at various stages, from CI/CD pipelines to registries, ensuring vulnerabilities are detected early and preventing deployment of compromised containers.
Registry Scan helps secure container repositories by scanning images stored within registries, ensuring compliance with security standards and identifying risks even before deployment.
RAT evaluates your deployed configurations against best practices (e.g., DISA STIGs) to detect potential vulnerabilities in systems post-deployment, even if the initial container image is secure.
AccuKnox’s SCA analyzes the individual components of your software, checking for risky modules, license violations, and vulnerabilities, enabling organizations to proactively manage their software supply chain.
AccuKnox secures edge and 5G workloads with real-time enforcement, offering visibility and protection for mission-critical environments such as ORAN deployments and ensuring compliance with security policies.
AccuKnox enforces hardening policies on virtual machines, securing applications by ensuring proper configurations, and defending against runtime threats to improve overall security posture.
AccuKnox secures Kubernetes clusters by providing runtime security, monitoring configurations, enforcing policies, and detecting vulnerabilities to maintain a strong security posture across containerized workloads.
AccuKnox’s CWPP focuses on providing runtime protection and visibility for workloads across hybrid and multi-cloud environments, ensuring consistent security for Kubernetes, containers, and serverless workloads.
AccuKnox integrates seamlessly with CI/CD pipelines to provide security across the development lifecycle, enabling DevSecOps teams to automate security policy enforcement and vulnerability scanning.
Yes, AccuKnox uses kernel-level monitoring and proactive enforcement techniques to identify and block attacks in real-time, effectively mitigating the risks from zero-day vulnerabilities and other threats.



























