SAST Solution – Secure Your Code with AccuKnox
Eliminate Threats Before They Become Attacks
Building an application with advanced features requires detection and remediation of vulnerabilities. Learn how AccuKnox differentiates with the unique value proposition in shift-left SAST scanning.
Aggregated Visibility of CI/CD Pipelines and Code Scanning
Secure Coding Made Simpler
- Scan and detect vulnerabilities at multiple stages, (IDE, CI/CD pipelines) with compliance checks.
- Early vulnerability detection and remediation reduce risks during development.
- Analyzes both application code and libraries for comprehensive vulnerability management.
- Integrates seamlessly into developer workflows without disruption.
Unified SAST Offering
- Centralized platform integrates SAST with other security tools like DAST.
- Supports container image scanning with KubeArmor for continuous monitoring.
- Software Composition Analysis (SCA) identifies vulnerabilities in open-source components.
- Insights for vulnerability remediation in the development environment.
- Facilitates ongoing security improvements through regular updates.
Full-Proof Your Code with AccuKnox’s SAST Solutions
Enhanced security measures
By identifying the vulnerabilities in your source code, our SAST services help prevent security threats before they can be exploited.
Risk management and compliance
With our services, you can stay compliant with the relevant security rules and regulations. This minimizes financial and legal risks.
Cost saving and efficiency
Early detection and remediation of vulnerabilities can lead to cost savings by avoiding the need to implement expensive post-deployment fixes.
Improved application quality
Integrating SAST solution into your product development cycle can increase the overall quality and reliability of your applications.
Automating SAST with CI/CD Pipelines
- Automates security testing in the CI/CD pipeline for continuous protection.
- Provides immediate feedback on vulnerabilities, accelerating remediation.
- Supports multiple frameworks and languages for versatile integration.
- Enhances overall security without disrupting workflows.

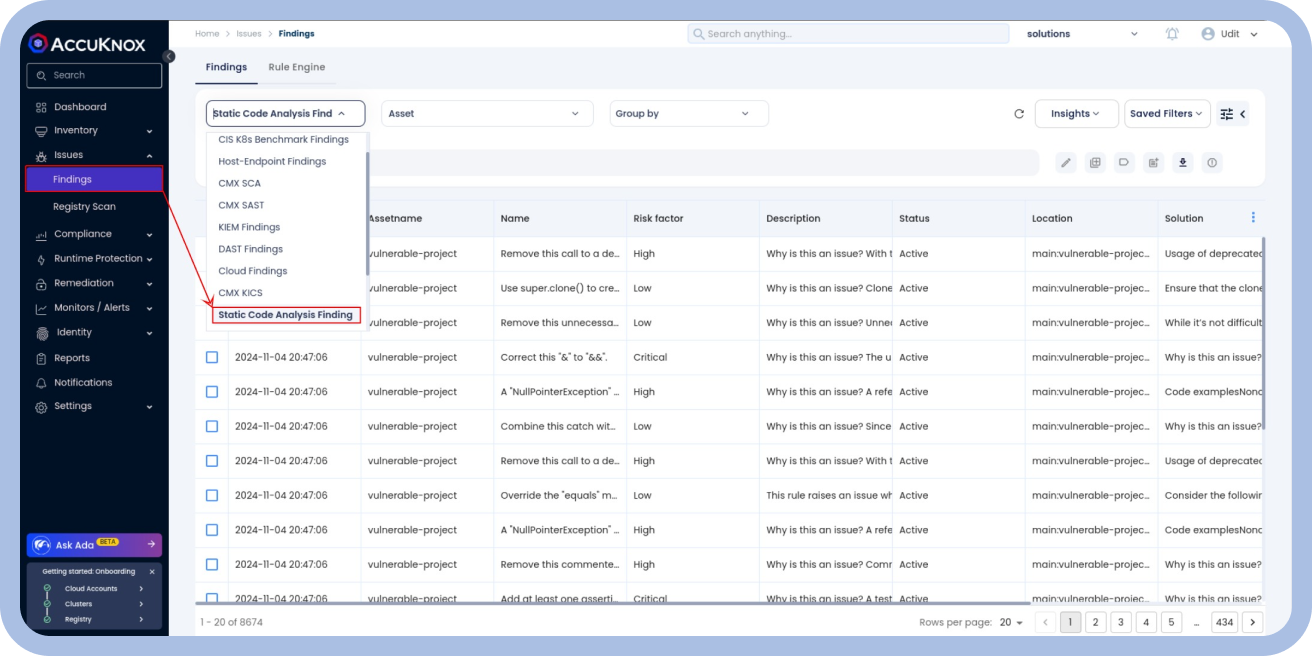
Integrated SAST with existing pipeline tooling
- Reduces false positives and improves vulnerability management.
- Seamlessly integrates container security into app protection.
- Strengthens security posture and builds customer trust.
FAQ
Static Application Security Testing (SAST) analyzes source code or compiled versions of code to identify security vulnerabilities. It examines the code without executing the application. SAST tools scan the entire codebase to find potential security flaws early in the development process.
SAST analyzes source code statically, while DAST tests running applications from the outside. SAST can provide earlier feedback in the development process and cover more code paths. However, SAST may miss runtime and environment-related vulnerabilities that DAST can detect.
SAST can detect many vulnerabilities, including buffer overflows, SQL injection, cross-site scripting (XSS), and insecure cryptographic practices. It’s particularly effective at finding coding errors, insecure API usage, and coding standards violations. However, it may struggle with complex runtime issues or configuration-related vulnerabilities.
SAST can be implemented very early in the development process, as soon as the code is written. It can be integrated into developers’ IDEs for real-time feedback, run during code commits, or as part of the build process. Early implementation helps catch and fix vulnerabilities before they become entrenched in the codebase.
SAST is a crucial component of a well-rounded security program. It should be used alongside other techniques like DAST, manual code review, and penetration testing. SAST is particularly valuable for continuous testing in CI/CD pipelines and for maintaining code quality throughout development.
Organizations can reduce false positives by fine-tuning SAST tools to their specific codebase and practices. Regular updates to the SAST tool and its rule set are important. Implementing a triage process for SAST findings, where experienced developers review and validate results, can also help manage false positives effectively.











