Zero Trust Secrets Scanning
The advanced secret scanning engine covers leaked secrets, such as API keys, access tokens and passwords, across workloads to proactively detect and mitigate risks.
Book a Demo
Understanding the Importance of Secret Scanning
- Leaked credentials are a major cause of modern cyber attacks, resulting in data breaches and resource exploitation.
- Attackers use automated tools to detect and exploit exposed secrets rapidly.
- AccuKnox’s multi-surface secret scanning mitigates risks, prioritizes remediation, and enhances security.
- Get Secrets Scanning on multiple deployment types (on-prem, air-gapped and public cloud platforms)
Centralized Secret Management for Multiple Deployments
Secrets in Container Scan
Seamlessly integrate with Jenkins, Azure DevOps, Gitlab and Bitbuck.With the integration of TruffleHog to detect sensitive data such as API keys, tokens, and secrets in the source code. The detected secrets are then uploaded to AccuKnox SaaS for centralized visibility and management.
Pipelines Security for Popular CI/CD Providers

Secrets in K8s Config Maps
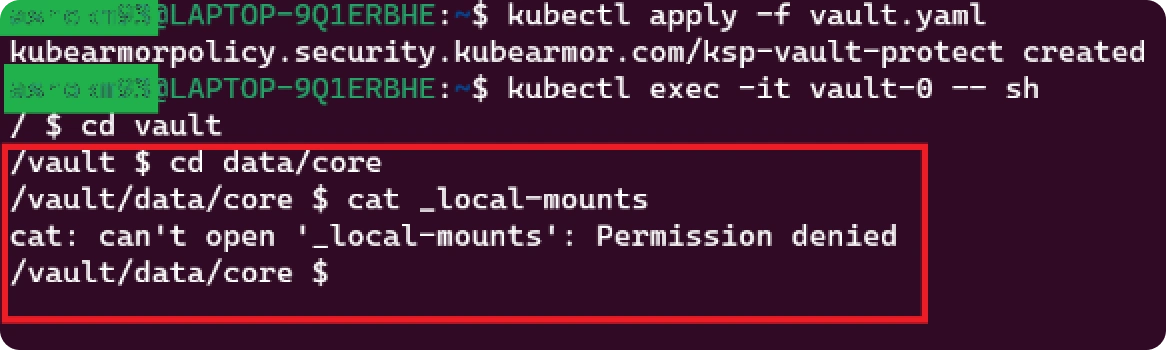
CyberArk Conjur (or) Hashicorp Vault when deployed in the Kubernetes cluster stores sensitive information in the volume mount points. Conjur-oss container has /conjure-server volume mount point where the sensitive information is stored. We harden it in runtime to provide observability and defense against unknown attacks.
Our users benefit the hardening of

Use Case – HashiCorp Vault Hardening
- Ransomware Protection: KubeArmor blocks unauthorized access to Vault secrets.
- Real-Time Defense: Prevents command injection and remote code execution using eBPF.
- Easy Management: AccuKnox monitors, applies policies, and provides alerts for proactive security.
Major Attacks AccuKnox can defend with Advanced Secret Scanning
| Attacks | What Happened | How AccuKnox Could Have Prevented This |
|---|---|---|
| CircleCI Incident (2023) | Attackers accessed customer environment variables, including secrets, through a compromised CI/CD system. | Flagged exposed environment variables during pipeline execution and prevented unauthorized access. |
| Uber Breach (2022) | Attackers exploited a hardcoded access key in a private repo to access Uber’s infrastructure. | Proactive scanning of code repositories could have detected and removed the hardcoded access key. |
| Toyota GitHub Leak (2022) | API keys for Toyota’s T-Connect service were publicly exposed in a GitHub repository. | Automated scans of repositories could have identified the exposed API keys before they became public. |
| Capital One Data Breach (2019) | Misconfigured S3 buckets led to the exfiltration of sensitive customer data. | Scanned S3 buckets for exposed secrets and misconfigurations to prevent unauthorized data access. |
| SolarWinds Cyberattack (2020) | Compromised build systems included leaked credentials, facilitating the attack. | Scanned container images and file systems to detect and remove embedded credentials in the build environment. |
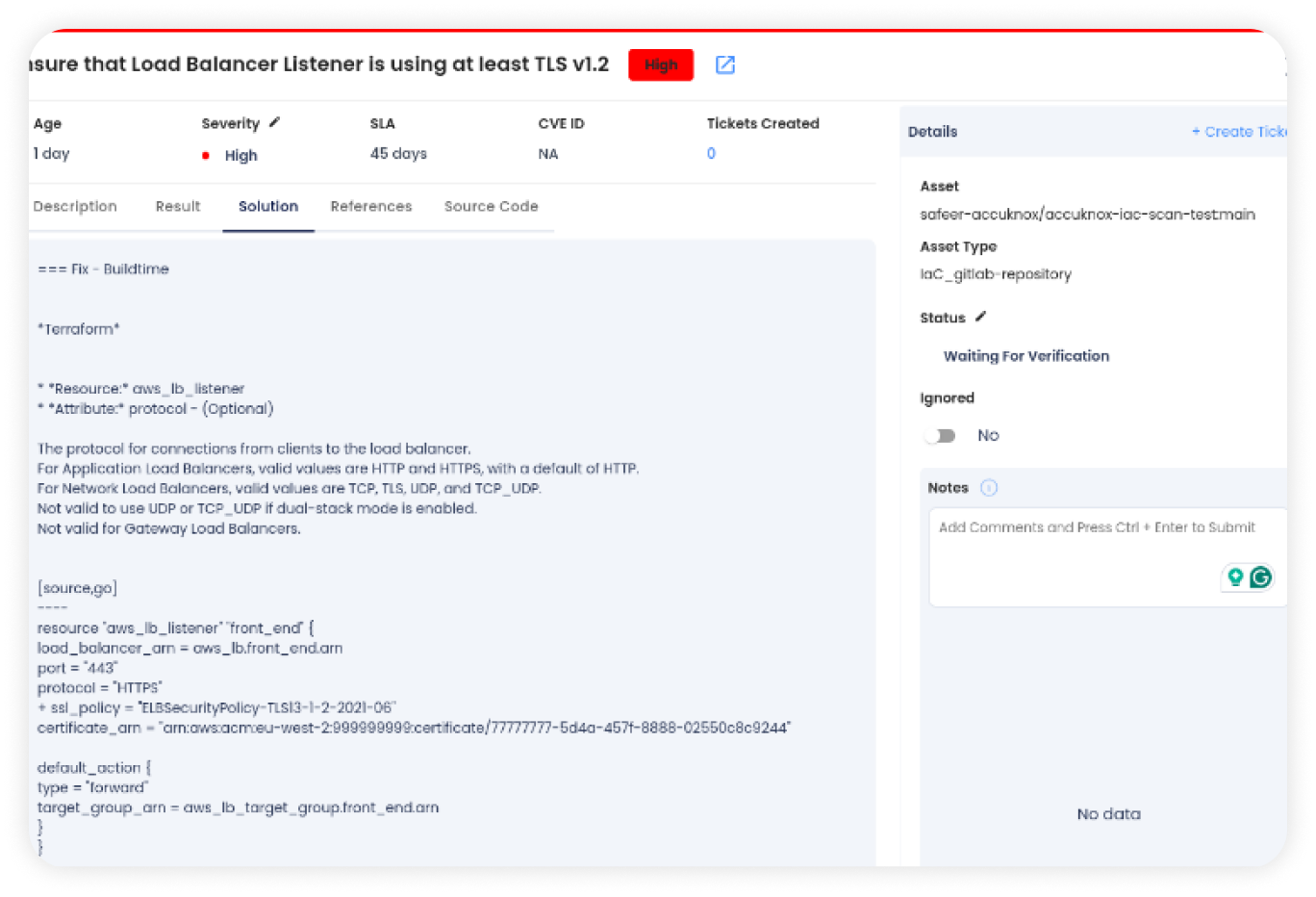
Azure DevOps IaC Scan Integration
for Secrets Scanning
Flexibility in secret scanning. Allowing integration with Azure DevOps to automate IaC security scans, detecting vulnerabilities during pipeline execution. Findings are sent to AccuKnox SaaS for advanced analysis and streamlined remediation.
- Automate IaC security checks with AccuKnox in Azure DevOps pipelines.
- Quickly resolve vulnerabilities with detailed insights on SaaS.
- Ensure secure, compliant deployments with best-practice alignment.
- Streamline DevSecOps with centralized issue tracking and re-scans.
Customer Reviews

AccuKnox is the best example of how to achieve NIST & MITRE conformance out-of-the-box. The team has done a great job of simplifying security concepts from the scratch, I highly recommend it to Kubernetes practitioners”

Scott Surovich
Principal Engineer - Global Container Engineering Lead


Kubernetes is the de facto Cloud Operating System, yet securing it efficiently and effectively presents a wide-ranging challenge. AccuKnox has been instrumental in bringing defense to unknown attacks at real-time”

Andrew Martin
CISO & CEO

AccuKnox is a must-try for every Cloud Native security engineer in Zero Trust Journey. With 1 Million+ KubeArmor downloads, the open-source tool chest is very helpful for Kubernetes runtime protection”

Gnanavelkandan Kathirvel
Head of Product
Google Distributed Cloud

AiDash was looking for a Comprehensive Cloud Native Security platform that spans Application Security and Cloud Security. AccuKnox’s very strong and Enterprise offering coupled with a strong roadmap of securing AI/LLM Models made them a compelling choice”

Rahul Saxena
Co-Founder, Chief Product & Technology Officer


Thanks to our existing partnership with AccuKnox, we were able to work with a pioneer in Zero Trust Security. Tible is committed to delivering comprehensive security, compliance, and governance for all of its stakeholders”

Merijn Boom
Managing Director


AccuKnox does a tremendous job at showing the complexity of different approaches to Kubernetes security in terms of the speed of sending a response against emerging CVEs and unknown cloud attacks”

James Berthoty
Founder & Security Analyst
FAQ
AccuKnox’s KubeArmor uses eBPF and LSMs like AppArmor to enforce runtime security policies, blocking unauthorized access to Vault secrets. It detects and prevents malicious activities, such as command injection and unauthorized file access, in real-time.
Yes, AccuKnox scans GitHub, GitLab, and other repositories to identify hardcoded secrets like API keys or credentials. By integrating into CI/CD pipelines, it flags issues during development, preventing exposed secrets from reaching production.
AccuKnox monitors Kubernetes configuration maps, secrets, and runtime behavior. Using KubeArmor policies, it restricts access to sensitive files and processes, safeguarding clusters from misconfigurations and secret exposures.
Unlike traditional tools, AccuKnox’s secret scanning spans multiple surfaces, including S3 buckets, file systems, container images, and IaC repositories. It also validates whether detected secrets are active, prioritizing remediation for live credentials, which is crucial for reducing attack risks.












