
The Need for Runtime security in the cloud – Part #2
As we saw in part #1, it is easy for a workload to be exploited and to have your environment attacked if it is compromised due to unpatched vulnerabilities, un-detected misconfigurations, or zero-day. In the absence of runtime security i.e. guardrails to observe and continuously protect and harden the workload. Accuknox Runtime security tools for […]
Reading Time: 3 minutes
Table of Contents
As we saw in part #1, it is easy for a workload to be exploited and to have your environment attacked if it is compromised due to unpatched vulnerabilities, un-detected misconfigurations, or zero-day. In the absence of runtime security i.e. guardrails to observe and continuously protect and harden the workload.
Accuknox Runtime security tools for the Cloud
Before we move forward, it is important to understand the components that Accuknox provides to enable runtime cloud security. This list includes:
- KubeArmor – a runtime security tool that hardens and audits your K8s/cloud workloads using eBPF, and Linux Security Modules. Accuknox is the core maintainer of this CNCF Sandbox project. KubeArmor can help restrict whether applications can initiate network connections or not, what files or directories they can access, what processes they can access and fork and what other Linux capabilities they can request.
- Cilium – a network CNI observability and security tool for K8s and cloud workloads. Accuknox is adding extensions to support pure Virtual Machine workloads, identity (SPIFFE id) based security, audit mode, and more. Cilium provides L3, L4, and L7 support with support for identity-based security.
- Auto Policy Generation tool – This is an open-source tool from Accuknox that automatically generates security as code policies that can be enforced on your cloud workloads to provide run-time security.
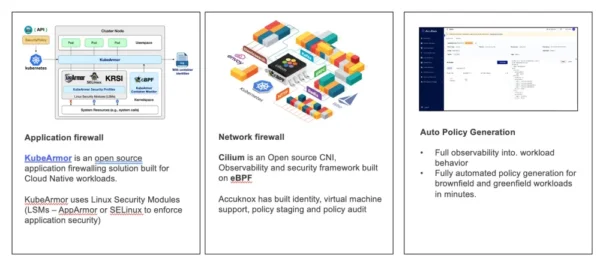
Run Time Tools
All of the above tools are a) fully open-source b) provide security as code c) are fully automated to the extent possible to deploy large production workloads with runtime security.
How can we protect your workload at runtime?
There are a few simple steps to applying Zero trust at runtime to protect your cloud workload and restrict them from engaging in malicious activities.
Step #1: Identify the baseline security of your application while it is running, in a safe environment such as a test cluster.
Accuknox’s open-source auto policy discovery tool enables DevSecOps engineers to fully automatically observe and generate granular security policies for the runtime behavior of the application.
Auto-policy discovery generates the following policies
– Cilium Policy Discovery based on
- L3/L4 discovery based on CIDRset/Ports/FQDN/Labels
- L7 HTTP based policy discovery
- Kafka based auto policy discovery
– KubeArmor Policy Discovery based on
- File System Access
- Process invocation
- Network access
- Capabilities
To learn more on how to generate and apply the policies on your workload, visit the accuknox help link.
Step #2: Apply Least privilege policies using Open source policy templates
Clone the free and open source policy templates that have many standard hardening solutions and technical STIGS (Security Technical Implementation Guides) available for various workloads. Apply these policies (as relevant) to your workload to put your workload in the least permissive mode. These policy templates provide the ability to harden your workload and restrict malicious activity.
Step #3: Monitor the workload for new accesses/breaches and continuously apply or decline new policies discovered.
Accuknox’s open-source and SAAS tooling enables developers to be able to be discovered while the workload is running based on new behavior observed. These policies can be generated as Yaml files directly into a git repository or a local file system after which you can review and approve/decline the new behavior that was previously unobserved.
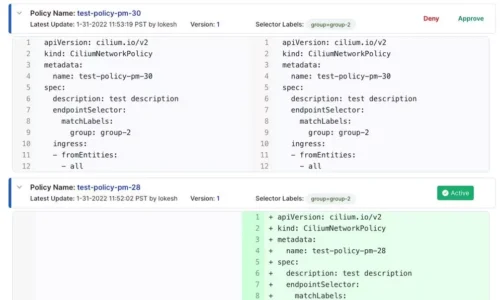
A typical CI/CD pipeline and workflow for using Accuknox’s open-source tools for runtime security might look like this:
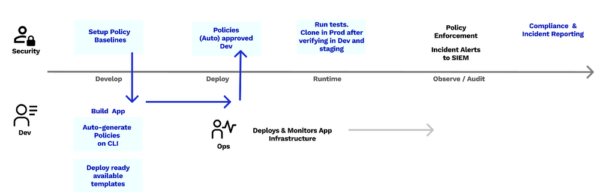
Once enforced, Accuknox will enforce runtime security and audit on an ongoing basis – explicitly giving you full coverage of workloads security at runtime.
Conclusion
Runtime security helps prevent malicious activity on your workload if and when it is compromised. Accuknox’s open-source tools
Please reach out to us if you have any questions or comments.
- Schedule 1:1 Demo
- Product Tour
On an average Zero Day Attacks cost $3.9M

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support



