Zero Trust Security for Nutanix
AccuKnox delivers comprehensive Zero Trust Security for Nutanix On-premises and Managed deployments.
Let’s Demo
Hardened Security for Nutanix VMs, Containers, Kubernetes
- Automated Zero Trust Policies
- Vulnerability Management
- Risk Assessment
- Security Hardening using KubeArmor
- KIEM (Kubernetes Identity and Entitlements Management)
- App Behavior analysis
- Network Microsegmentation
- Forensics, Auditing

Key Features
| Features | |
|---|---|
| NKE or D2IQ or RH/OCP | |
| Nutanix DB Service | |
| Nutanix Flow; AccuKnox Micro segmentation | |
| AccuKnox Multi Layer Zero Framework | |
| AccuKnox k8s/container/VM Forensics | |
| NCS | |
| Scan registries and k8s dep. ECR, ACR, GCR, JFrog, Docker hub, Docker Org, Harbor, Quay, Nexus | |
| Supported | |
| Audit, Enforce/Block | |
| Supported with auto segmentation |
AI/LLM Algorithm Security Risks
Your sensitive assets require intensive monitoring. Get Workload & Cloud Compliances with continous visibility.
Security Risk
- Prompt Injection
- Insecure output Handling
- Training Data Poisoning
- Model Denial of Service
- Supply Chain Vulnerabilities
- Sensitive Information Disclosure
- Insecure Plugin Design
- Excessive Authorization
- Model Theft
AccuKnox Protection
- Sandbox with Preeptive Mitigation
- SBOM Verification
- Container Scanning
- Malware Protection
- Workload Hardening
- Fencing Data Assets in Workloads
- Network Microsegmentation
Nutanix GPT-in-a-box Assessment & Protection
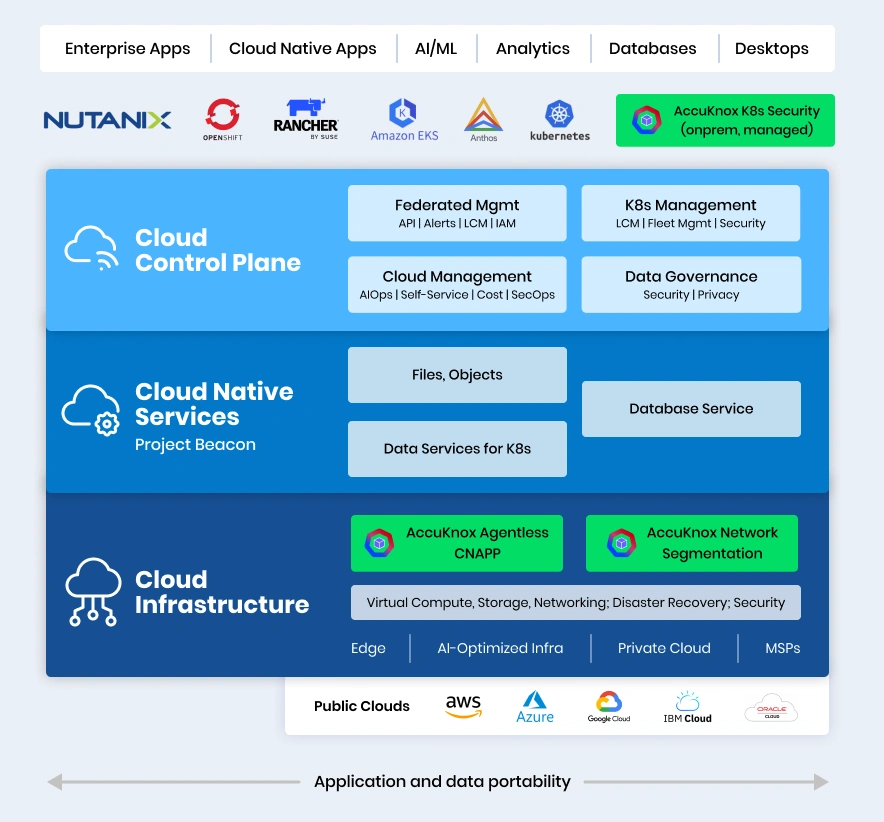
AccuKnox adds an effective security layer for Nutanix offerings
- Zero Trust CNAPP with focus on Kubernetes and Virtual Machines
- CSPM: Cloud account scanning, misconfiguration, remediation
- ASPM/SAST/DAST/IaC scanning and tools integrations
- CWPP: Workload Image Scanning for VMs, Containers, K8s assessment
- Runtime Security: Differentiated offering
- Identities & Entitlements
Latest Resources
All Advanced Attacks are Runtime Attacks
Zero Trust Security
Code to Cloud
AppSec + CloudSec

Prevent attacks before they happen
Schedule 1:1 Demo
FAQs
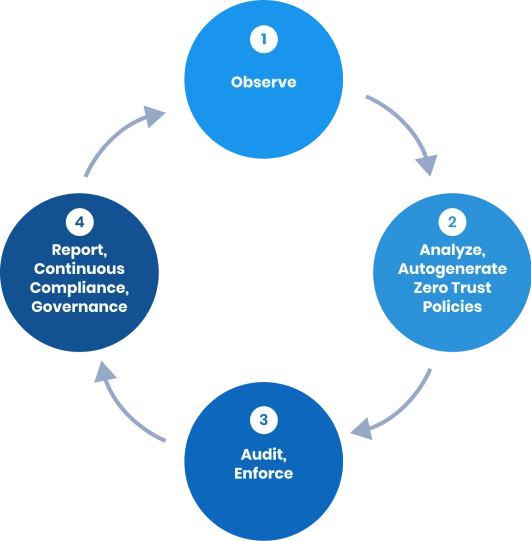
AccuKnox CWPP provides micro-segmentation at the lowest possible granularity level which is also a smallest execution unit in Kubernetes i.e. Pods. We will help you to identify process execution requests from the pods, network connections the pods are trying to make internally or externally and files-system the pods are accessing. By observing the behavior of a particular pod and restricting that behavior so that it functions according to the expected flow of process/events/traffic, one can develop a least permissive security posture from creating a whitelisting policy and auditing/denying everything else.
KubeArmor is a security solution for the Kubernetes and cloud native platforms that helps protect your workloads from attacks and threats. It does this by providing a set of hardening policies that are based on industry-leading compliance and attack frameworks such as CIS, MITRE, NIST-800-53, and STIGs. These policies are designed to help you secure your workloads in a way that is compliant with these frameworks and recommended best practices.
By implementing a zero trust posture, organizations can increase their security posture and reduce the risk of unauthorized access or activity within their Kubernetes clusters. This can help to protect sensitive data, prevent system breaches, and maintain the integrity of the cluster. KubeArmor supports allow-based policies which result in specific actions to be allowed and denying/auditing everything else.






