
Potential of CSPM: Answering the Market’s Demands
Cloud security has gained prominence in a time of complex multi-cloud architectures and increased online threats. CSPM tools are essential for businesses looking to strengthen their cloud security procedures because they provide essential features and ready-made solutions for cloud security. Discover the four essential steps to improving your cloud security posture.
Reading Time: 11 minutes
Table of Contents
Benefits of CSPM for Testing, CI/CD, and DevSecOps
Although the cloud provides countless opportunities for innovation, it is challenging to manage the security Governance, Risks and Compliance. CISOs and IT directors must negotiate multi-cloud architectures that are becoming more complicated.
While doing this they also defend against ever-changing cyber threats. Simple service misconfigurations and excessive permissions result in expensive data breaches. This has necessitated the adoption of new methods and technologies.
Cloud Security experts now recommend Cloud Infrastructure Entitlement Management (CIEM) and Cloud Security Posture Management (CSPM).
CSPM solutions handle security-related concerns related to:
- Platform as a Service (PaaS)
- Infrastructure as a Service (IaaS)
- Software as a Service (SaaS)
Services provided by CSPM
- Security risk visualization
- Risk intensity assessment
- Security threat incident response
- DevOps integration services
The best feature of a CSPM solution is its deployment for all forms of cloud infrastructure. This includes cloud services delivered in a containerized environment, hybrid cloud, private cloud, and multi-cloud.
This article will discuss CSPM, its significance, and advantages over traditional security solutions. We will also throw light on its functionality, and comparison to other cloud infrastructure security solutions. Services and adjacent verticals that frequently use CSPM tools include CIEM, IaC security, and CNAPP.
What is CSPM?
CSPM tooling reduces and mitigates breaches in cloud data security. With the use of automation, CSPM systems test cloud settings against best practices. They also test compliance requirements. CIS, Azure, and GCP benchmarks, PCI or HIPAA guidelines among others are all checked by CSPM tools. This is done to ensure that cloud setups adhere to them.
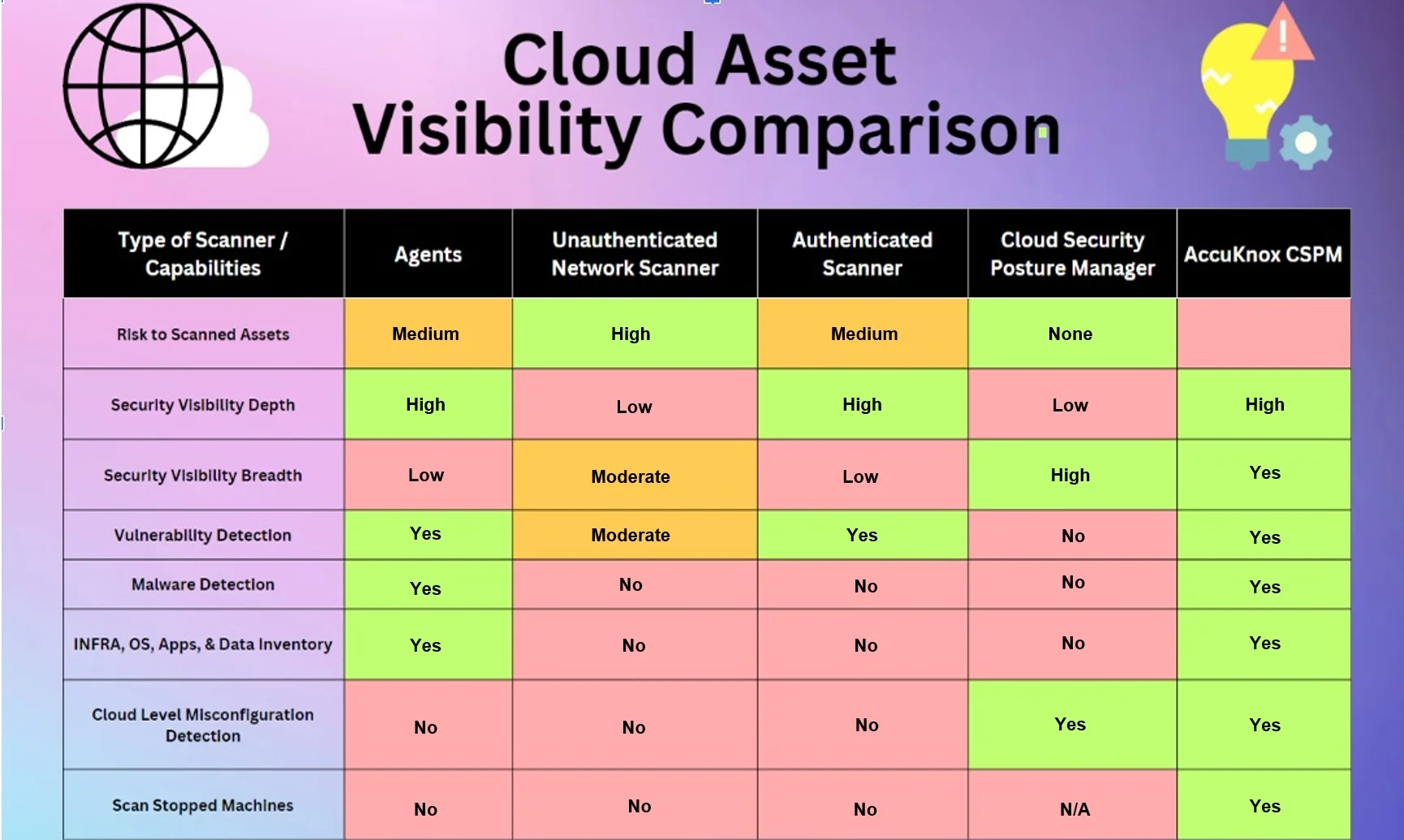
How CSPM Works
CSPM tools are developed to connect to the cloud infrastructure and test the following –
- data on cloud assets
- the networks to which they belong
- user rights, and tags
Data from the flow, configuration, and audit logs of the cloud environment are ingested, saved, and evaluated when a cloud account is added to a CSPM. Then, sysadmins work with this data to set up policies, look into and fix problems, and send alert messages. This also allows sending pertinent data to external tools for further analysis. With a CAGR of 14.4%, the worldwide CSPM market is anticipated to grow to USD 9.0 billion by 2026.
The CSPM provides the helpful services listed below:
- Discovery and Visibility
- Misconfiguration Management and Remediation
- Continuous Threat Detection
- DevSecOps Integration
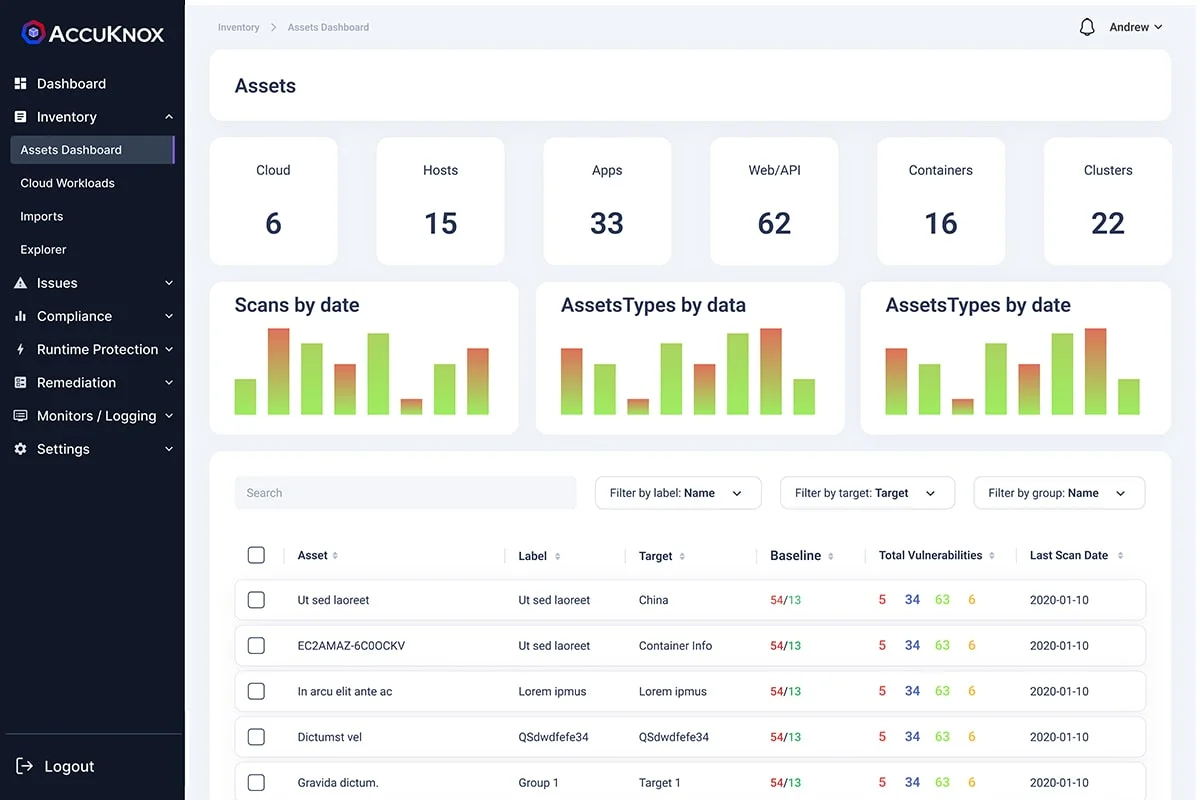
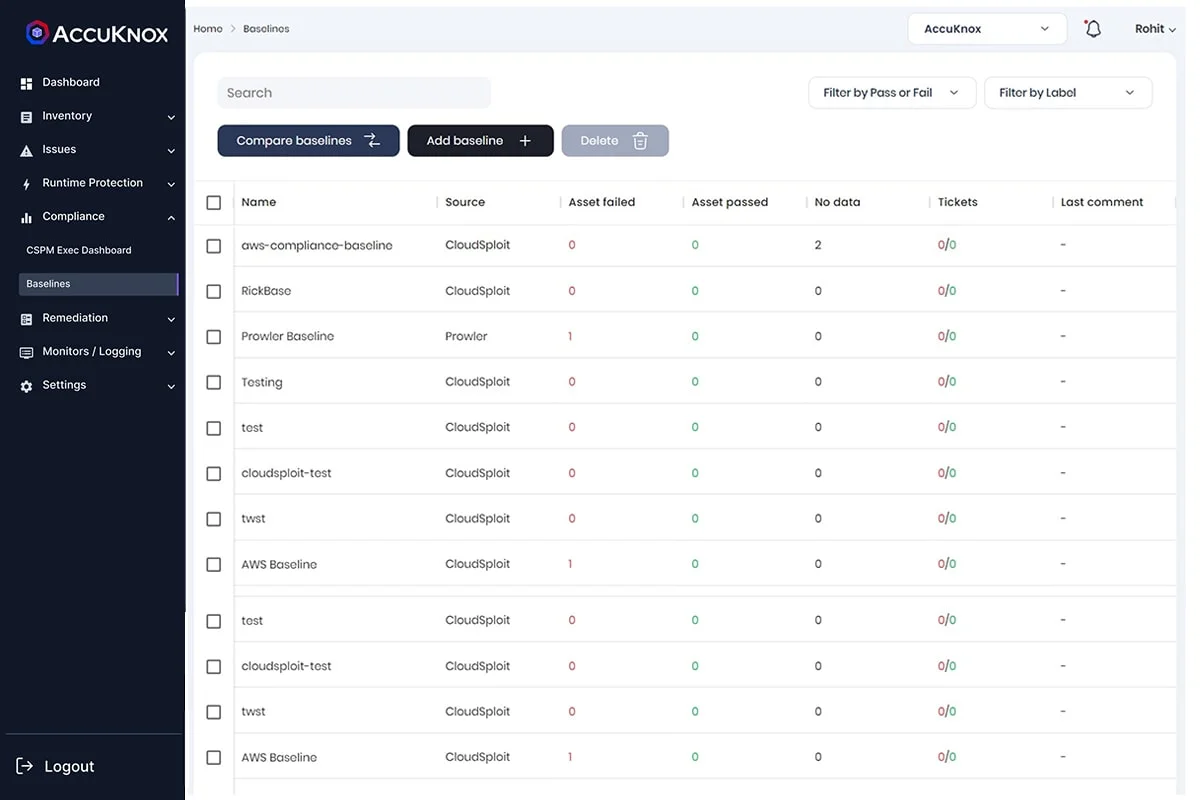
Asset Inventory listing severity of each asset along with the baselines in AccuKnox CSPM
Discovery and Visibility
For enterprises, major problems include a lack of knowledge and experience with cloud security best practices (62%), inadequate visibility into security and monitoring tools (59%), and insufficient access to security and monitoring data. The discovery and visualization of equipment assets and security settings carried out in cloud infrastructure are made possible by a CSPM security system. Users have access to a single source of truth across many cloud computing environments and accounts.
CSPM tools discover:
- System errors
- Metadata
- Networking flaws
- Any change in security operations
- The deployment of security group policies across user accounts specified in regions, projects, and the single interface.
Misconfiguration Management and its Remediation
To compare the configuration of apps placed in the cloud, industrial and organizational standards are created. This allows for the real-time detection and remediation of vulnerabilities. The CSPM system aids in identifying and removing security risks and vulnerabilities. Besides, it also monitors
- Application misconfiguration
- Open IP ports
- Unauthorized modifications
- Other pertinent problems that may expose cloud infrastructure resources to security threats
On identification, DevSecOps teams mitigate these issues using the security solution’s guided remediation procedure.
Guidelines are also offered to assist developers in avoiding errors related to incorrect configuration of cloud infrastructure applications. To keep them current and prevent data from being available to the public without authorization and authentication, cloud infrastructure storage permissions are also checked.
Keep an eye out on DB changes to make sure availability SLA is met. DB backups must be performed with the encryption for data security turned on. IaaS storage services, network segments, and applications are exposed to the public internet by 50% of businesses, according to Gartner Research. All this is mostly due to misconfigurations.
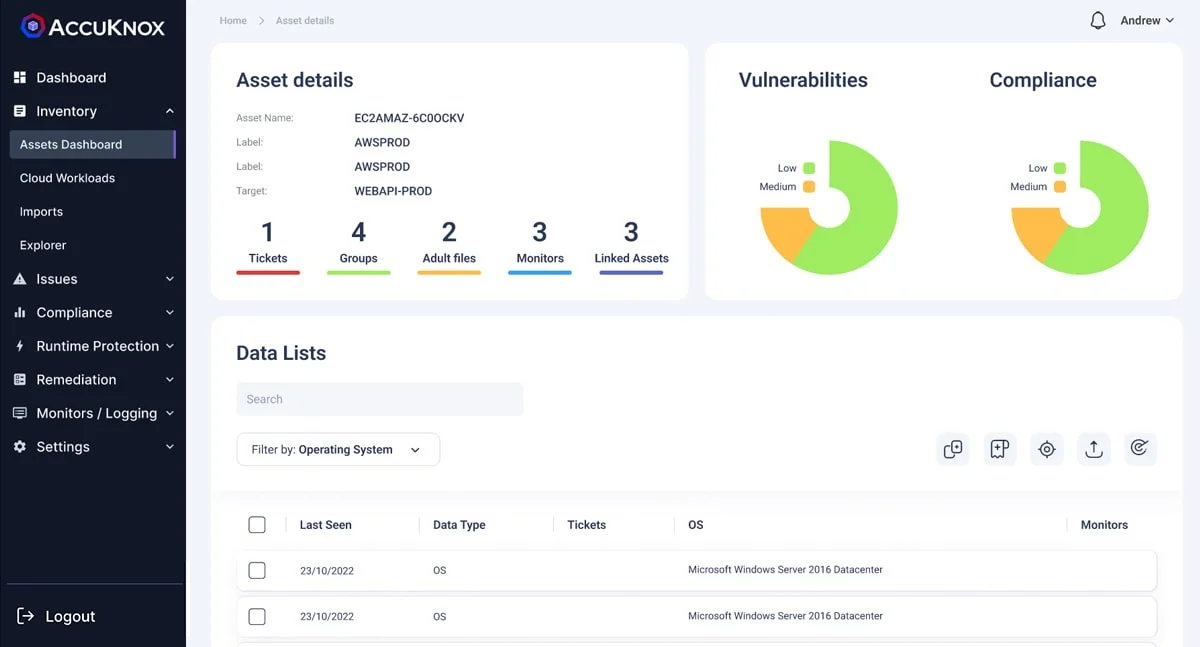
Asset Details and Misconfigurations in AccuKnox CSPM
Continuous threat detection
In a multi-cloud context, a CSPM uses a threat identification and management strategy. This identifies risks and alerts stakeholders. Throughout the application development life cycle, this proactive strategy comes in handy. Vulnerabilities in cloud infrastructure apps are pruned with the environment, and code errors are rectified before being pushed to production.
Gartner estimates that errors made by people are to blame for at least 99% of cloud security failures. Notifications are decreased as a consequence. This system also assists in the ongoing observation of harmful behaviors in the environment. I.e. detection of illegal permissions, and immediate recognition of unauthorized access to cloud infrastructure resources.
DevSecOps Integration
Conflict and complexity between cloud service providers and accounts are reduced by CSPM. It connects with DevOps technologies for quick reaction and mitigation. The centralized visualization and monitoring of cloud infrastructure resources are enhanced by agentless posture management. Throughout the entire lifespan of an application, security monitoring teams are responsible for intercepting and blocking compromised assets. For visualization and intelligence collection, CSPM security systems integrate with SIEM. Better communication between the infrastructure, DevOps, and security operations teams is made possible via reporting tools and dashboards.
Why is CSPM Important?
CSPM solutions are essential in assisting firms to maintain compliance with fundamental regulations or guidelines and to mitigate unintended risk, including:
- The exposure of databases holding sensitive information due to human error
- Wrong arrangements and settings that result in your organization’s noncompliance with key legislation
- Errors that allow unauthorized people to access servers, apps, or data
- Using ongoing cloud monitoring to find policy breaches
- Evaluating HIPAA, SOC2, and PCI compliance
Unlimited users establish and sever connections with cloud networks every day. Cloud network architecture gives connectivity from linked networks so they may access services. Thanks to the humongous amount of users (and possible attackers) traditional security measures are no longer practical for networks. This is obvious given the dynamic nature of cloud computing infrastructure.
The security complexity always rises due to the distributed nature of:
- Micro-services
- Kubernetes
- containerization
- Deployment of serverless functionality
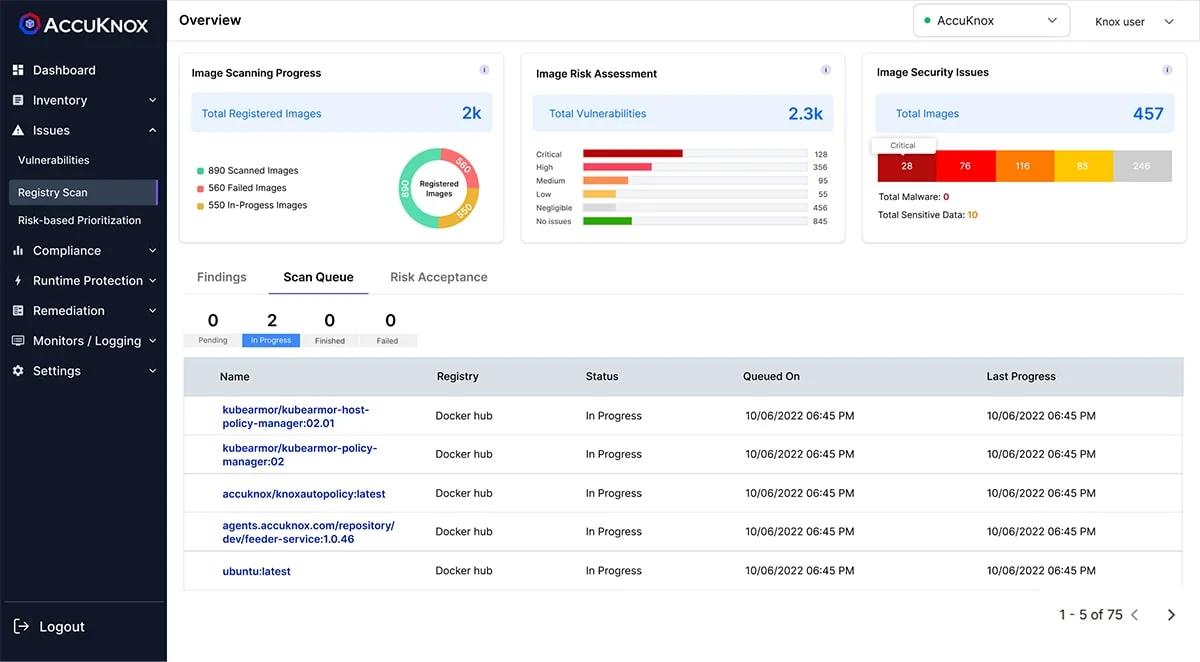
Registry Scanning and Container Security in AccuKnox CSPM
Cloud computing infrastructure also helps customers by lowering operating and administration costs. Traditional security techniques are unable to handle this due to – the absence of perimeters and manual procedures lacking scalability, speed, and centralization.
Misconfigured cloud computing systems contribute to vulnerabilities and data breaches. These get fixed quite easily using the CSPM Tool. Infrastructure as a Code (IaaC) allows for real-time modification of cloud infrastructure configuration.
A Gartner survey found that over 95% of security vulnerabilities in IT systems are caused by misconfiguration. This added up to $5 trillion in operation and maintenance expenses. Regular monitoring of cloud infrastructure is made easier by CSPM. As discussed above, it offers prevention, detection, prediction, and mitigation of potential vulnerabilities.
The Benefits of CSPM
Here is a list of the stated advantages of CSPM implementation:
- Better visibility and control by providing comprehensive security risk monitoring.
- Proactive risk mitigation through continuous cloud environments assessment.
- Real-time alerts and actionable insights.
- Compliance management is streamlined by identifying configuration drifts, and monitoring compliance against industry frameworks.
- Automated remediation recommendations.
- Cost optimization by identifying unused resources.
- Reducing unnecessary expenses on cloud spending through reports.
- Promoting accountability and establishing governance frameworks.
- Its scalability and flexibility allow it to adapt to dynamic cloud environments.
- Continuous security monitoring and risk assessment.
- Multi-cloud and hybrid cloud environments are supported.
- Allows organizations to maintain consistent security practices across different cloud platforms.
Baseline and Drift Detection in AccuKnox CSPM
A CSPM system can help governance and compliance teams monitor and report compliance with strict standards like PCI DSS, GDPR, SOC 2, and HIPAA.
- Monitoring your compliance status on a regular basis and automatically connecting it to standard compliance frameworks
- rapid production of audit-ready reports
- SOC teams’ ability to look at audit data for any anomalous user behavior or possible account breach
CSPM Use Cases and Capabilities
CSPM technologies offer continuous risk and compliance monitoring and evaluation for business cloud services. The following are the main use cases for security and risk management teams:
- Cloud workloads and services are continuously discovered and identified.
- insight into policies and uniform enforcement across many cloud service providers.
- Notifying users of potentially dangerous new deployments or modifications to the cloud environment’s hosts or services
- Risk assessment is in contrast to external standards set by organizations like the National Institute of Standards and Technology (NIST) and the International Organization for Standardization (ISO).
- Comparing risk assessment to technical guidelines and best practices (such as those recommended by the Center for Internet Security and cloud service providers, for example).
- Constant cloud capabilities for risk management, risk visualization, and risk prioritization
- Confirming that operational tasks (such as key rotations) are being carried out as planned
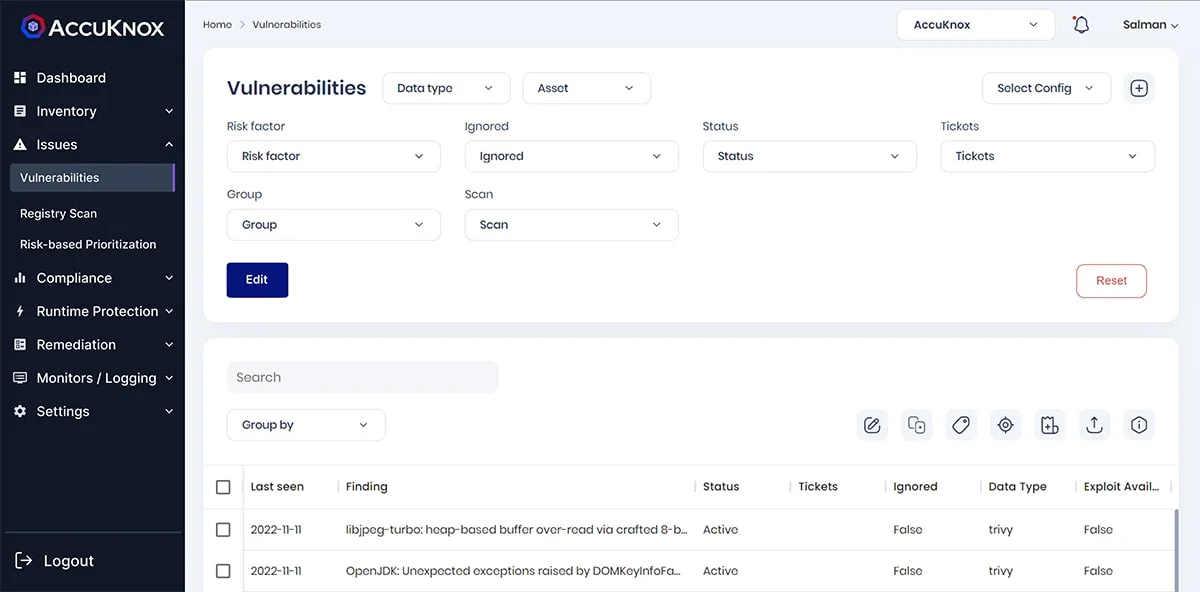
Vulnerability Management in AccuKnox CSPM
Cloud demands cloud-native solutions
The issues from before the cloud era have not been resolved by the transition to the cloud. Still, a major problem is vulnerabilities, incorrect settings, and compromised assets. But better solutions to such issues are brought about by the cloud.
Without dealing with deliberate threats and being able to accurately assess where an organization stands, CSPM cannot be considered comprehensive. Security rules that specify how security teams handle asset visualization, inventory, and management, incident response, as well as internal training and education, were first developed for on-premise settings and do not support the cloud’s security posture in a cloud-native manner.
Managing the posture of your whole cloud deployment across the full technological stack is referred to as cloud security posture management. To effectively handle all facets of security and compliance for your cloud workloads, CSPM solutions need to be complemented with deeper defensive and threat detection capabilities.
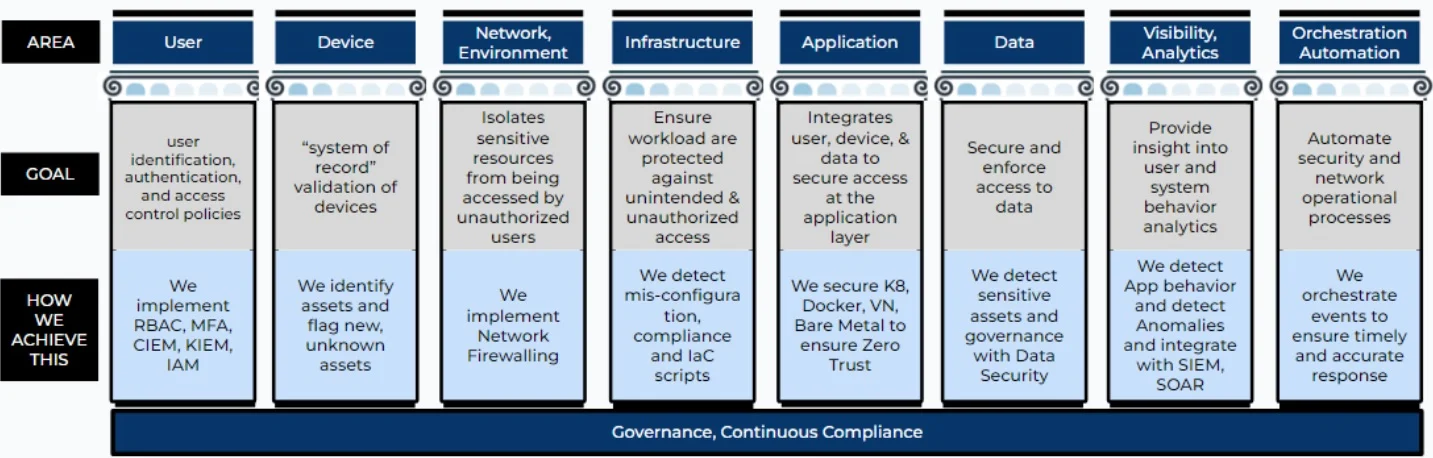
Four Steps to Boost CSPM
Consider taking the following actions to improve CSPM procedures:
1. Gain central access to all cloud assets
You need a broad perspective on risk and the degree of deviance from existing norms to appropriately handle security posture in the cloud. Let’s examine the following typical use cases:
- Incorrectly set S3 bucket that publishes your data
- Vulnerable web instances operating on an internet-facing server
- Contaminated resource in your network
- A device with sensitive data on it that is available to everyone online and is secured with a password that is simple to guess
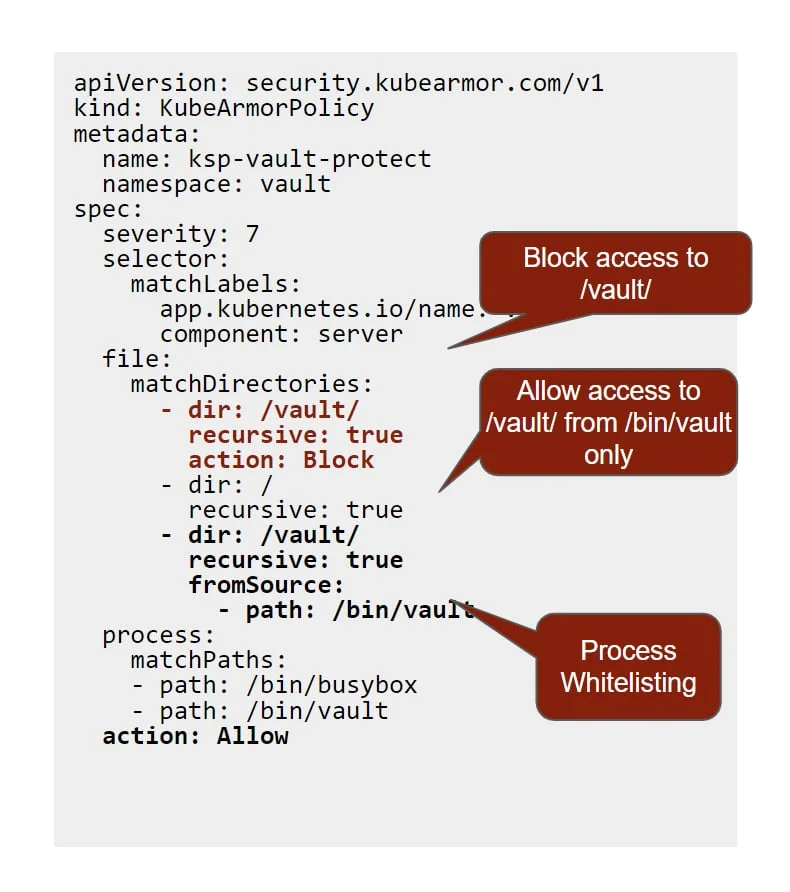
End-to-End Discoverability with KubeArmor Discovery Engine
A unified view of all your servers and assets in one location is necessary to strengthen your security posture in the cloud and avoid missing significant configuration errors, policy infractions, and blunders.
2. Find information in context
Security teams are ultimately overwhelmed by the flood of warnings, and closing security gaps relies on context that allows for prioritizing. Multiple data points cannot be manually integrated, for obvious reasons.
You need a thorough grasp of what’s happening and the capacity to interpret the data in order to assess your security posture in the cloud.
You must manually evaluate the alert using information received from two different tools, for instance, if you are using one tool to identify whether a system is running a vulnerable web server and another tool to pinpoint the machine’s location. As a consequence, you could identify 10 web servers that need to be patched right now.
Only one of them is Internet-facing, which is a problem since your valuable resources will be squandered on things that aren’t top priorities. It is simply insufficient for and security solutions to inform you of potential dangers or risk areas in order to improve your remedial skills.
Your team needs a simple, automated method for sorting through these warnings and evaluating them contextually.
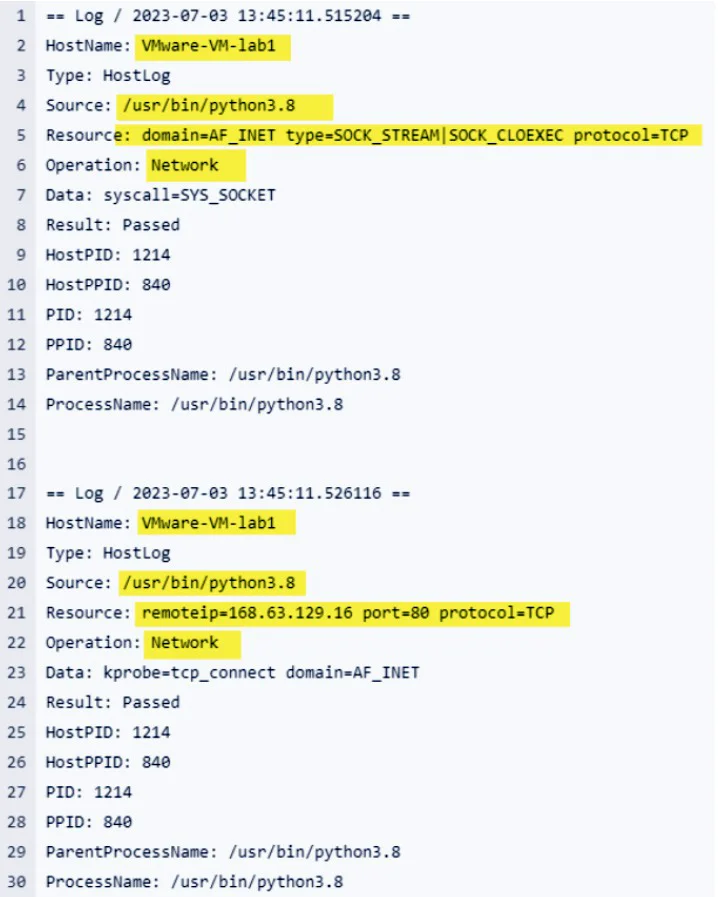
Root cause analysis is an must-have CSPM feature
3. Understand your TCO
Another crucial component of the problem is the total cost of ownership (TCO). When thinking about the various cloud security assessment tools, consider these questions:
- How long will it take your team to put the tool to use?
- How much internal conflict will it bring about? What number of integration points will I have to make?
- Will investing this much time result in adequate coverage? Will I have to spend more money to have this coverage when my cloud environment expands?
You need tools that support essential cooperation to accomplish security and compliance results in the future without wasting valuable resources, and CSPM solutions provide critical capabilities for DevOps, security, IT, and GRC teams alike.
4. Focus exclusively on cloud-native tools
Cloud security is different from the security we are accustomed to in on-premises situations, as we covered above. On-premises and in the cloud, the same concerns have distinct implications and require different mitigating techniques.
Will you see a vulnerability or setup error on 20 spot instances running the same image as one issue or 20 independent problems, for instance? They must be able to recognize that they are all copies of the same picture for a CSPM solution to be effective.
Mitigation strategies also need to be updated for the cloud. When you refresh photographs in the cloud rather than fixing them, your company is vulnerable.
However, the ideal approach for the cloud is to completely regenerate your photos using updated versions rather than merely patching them. Make sure the tools you’re employing can give appropriate actionable advice and are compatible with the cloud method of doing things.
Why AccuKnox CSPM?
- Our asset inventory tool offers insight across a multi-cloud infrastructure by connecting assets with vulnerabilities and misconfigurations.
- The type of cloud resource is used to categorize assets. The basis for segregation in various contexts.
- In a cloud system, misconfiguration is seen as a leading vulnerability with serious ramifications. A single pane of glass with explicit action items and findings tracking is available from AccuKnox.
- Utilizing scan findings to establish a baseline on the first day of your infrastructure, our solution platform builds baselines from various sources and tools.
- Deviations from the baseline trigger notifications via Slack and Jira integration mechanisms. When security measures are breached, users can specify unique baselines and receive personalized notifications.
- AccuKnox protects containers by scanning container images on a regular basis, continuously monitoring code and dependencies, and analyzing continuous compliance through auto-recommended hardening policies based on common frameworks such as MITRE, NIST, CIS, HIPAA, and PCI-DSS.
- The flexibility is provided by integrating many security scanning technologies via built-in parsers and automating collection and execution via “Playbooks Builder.”
- Zero Trust Approach
- To avoid alert fatigue, we prioritize and duplicate data from several security scanning technologies.
Your questions, our answers
Which use cases for CSPM are most typical?
Identifying and fixing configuration errors, lowering the risk of data breaches and other security events, and ensuring compliance with industry standards and laws, etc.
In what ways does CSPM support cloud governance?
By giving visibility and control over cloud resources. It checks whether it is correctly configured and protected. Compliance is tested with organizational and regulatory standards.
What remedial activities may CSPM tools carry out?
Applying patches, altering security settings, and revoking access to cloud resources are just a few examples of the remediation tasks.
Which cloud resources may be managed using CSPM tools?
Numerous cloud resources, such as virtual machines, containers, storage, databases, and network settings.
What kinds of security threats are detectable by CSPM tools?
Security hazards like:
- improperly set security groups
- Unprotected storage bins
- Exposed ports
- Misconfigured networks
All Advanced Attacks are Runtime Attacks
Zero Trust Security
Code to Cloud
AppSec + CloudSec

Prevent attacks before they happen
Schedule 1:1 Demo




