
Driving the Need for CNAPPs: Unified Risk Visibility, Vendor Consolidation, and DevSecOps
This blog highlights the importance of CNAPP (Cloud Native Application Protection Platform) in the cloud security landscape. We discuss agent and agentless approaches with use case-driven benefits in the domain of unified risk visibility, vendor consolidation, and DevSecOps practices shaping the market segment for robust protection.
Reading Time: 8 minutes
Table of Contents
In the constantly changing world of cloud-native applications, CNAPP (Cloud Native Application Protection Platforms) act as your reliable security friends. Even tech giants rely on these for their cloud app security from time to time.
💡TL;DR
- The complexity of multi-cloud architectures and the need to safeguard against online threats have put the spotlight on cloud security.
- CSPM tooling features include discovery, visibility, misconfiguration management, continuous threat detection, asset inventory, and testing cloud settings against best practices and compliance requirements.
- These solutions are suitable to deal with security issues in cloud infrastructures. Enterprises looking to enhance their cloud security procedures will benefit from adopting the CSPM toolset since it provides ready-made security solutions.
- 4 Steps to Improve Cloud Security Posture: Gain central access to all cloud assets, Locate information in context, understand the total cost of ownership (TCO), and focus only on cloud-native tools.
What makes them necessary, and how might they support your DevSecOps team?
Shifting left is the name of the game in today’s fast-paced tech industry. This means security issues get addressed early in the development process. Your ace in the hole is CNAPP, which can help you secure your applications from the start. These platforms have your back whether your apps are lounging in hybrid configurations or diverse cloud settings.
Speaking of Kubernetes, CNAPPs are all about maintaining container security. No security measures are overlooked for any environment (Eg. Red Hat OpenShift).
But wait, what’s the big deal?
Well, the cloud is flourishing, and our technology is becoming more advanced every day. Hybrid clouds, SaaS configurations, containers, serverless magic—you name it—are all topics of discussion. With so much complexity, we need novel tactics to maintain control. And this is where CNAPPs are useful.
We’ll discuss the value of having a CNAPP as your sidekick in the area of cloud security in this piece. We’ll also talk about the advantages and differences of each platform’s cybersecurity.
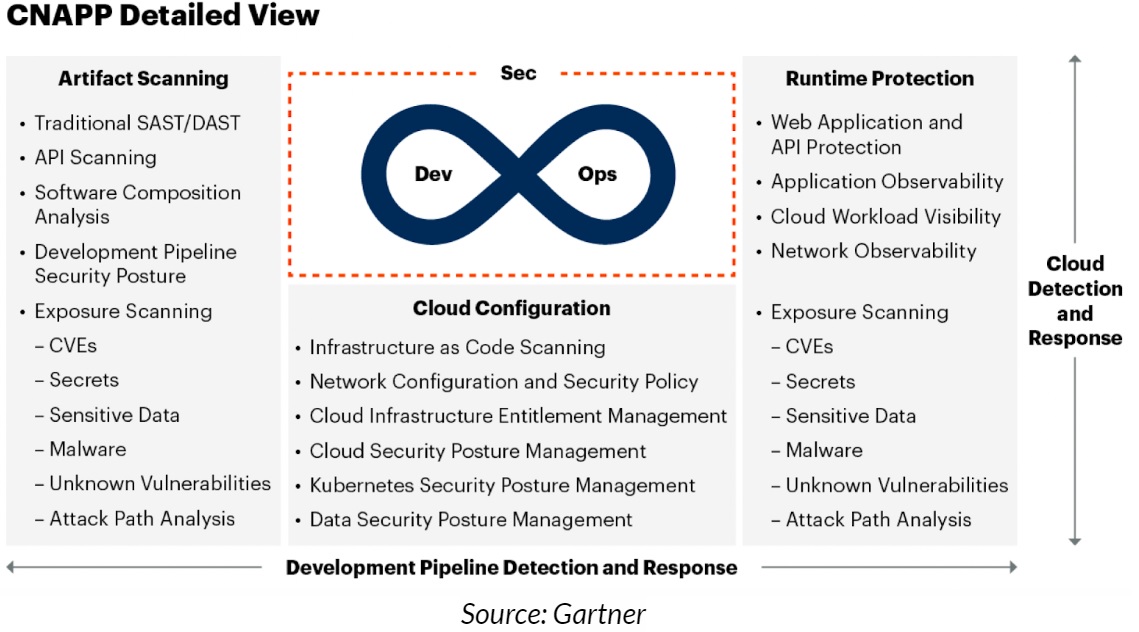
Understanding Cloud Native Application Protection Platform (CNAPP)
It unites many potent security features under one roof, which is why it is the most recommended. Two critical issues are addressed: lowering intrusion alarms and ensuring that your cloud apps have air-tight security. Consider it a complete solution for all security requirements:
- Unified Security Visibility
- Cloud Workload Protection
- Cloud Security Posture Management
- Cloud Infrastructure Entitlement Management
- Vulnerability Management, Detection, and Response
- Consolidation of Security Tools
- Integration with DevSecOps
- Zero Trust Architecture Support
What’s in the CNAPP toolbox?
- Cloud workload Protection Platform (CWPP). These operate as the app’s own bodyguards. They watch what goes on within to look out for any questionable activities.
- Cloud Security Posture Management (CSPM). It is the security checklist for your app. It makes sure everything is configured properly. Misconfigurations in the cloud can lead to severe financial losses! Not to mention the organizational reputational threat.
- Cloud Infrastructure Entitlement Management (CIEM). Consider CIEM as the great leveler that ensures that only the appropriate users get access to your app.
- Vulnerabilities Management, Detection, and Response (VMDR). These are your detectives, alert to any threats or vulnerabilities and ready to act.
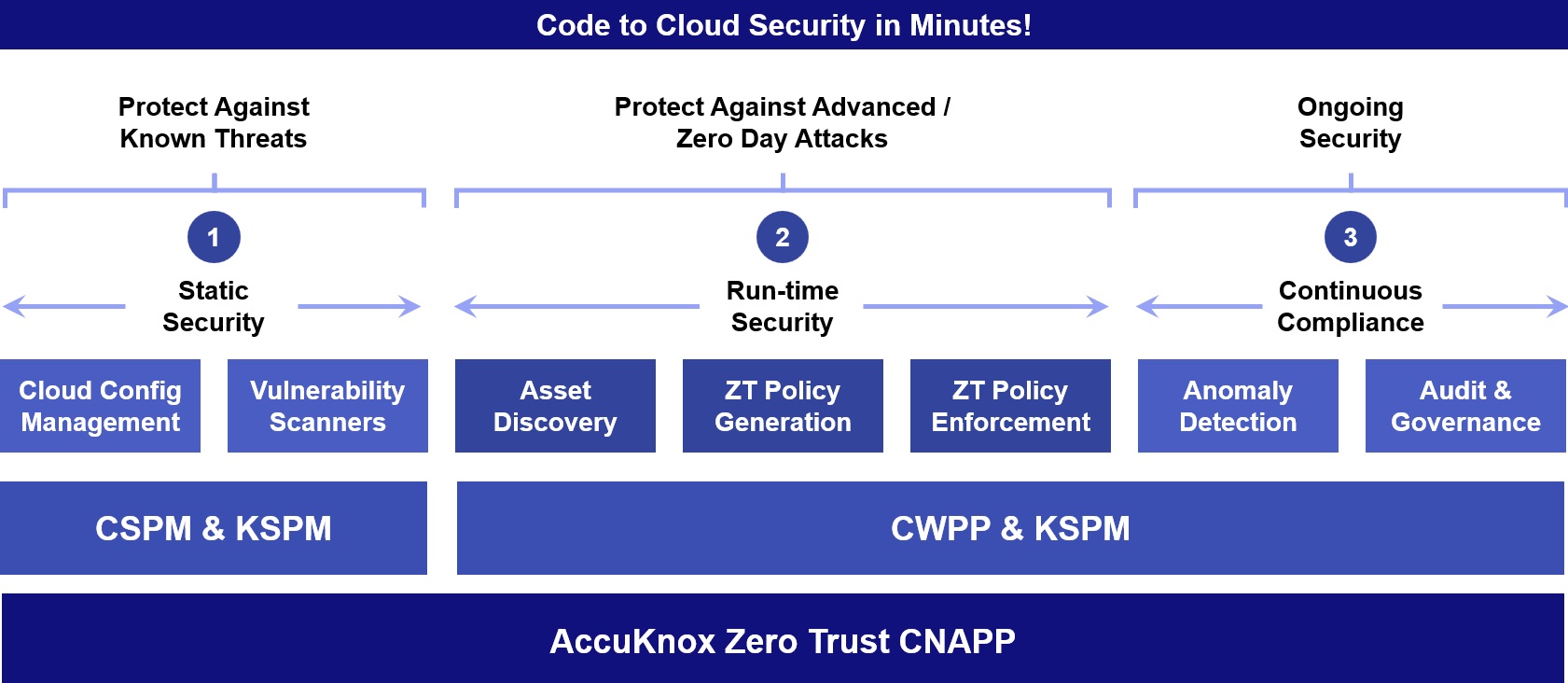
Why does it matter?
The majority of cloud data breaches are caused by minor configuration errors. This is where CSPM comes in to make sure everything is secure. CNAPP is like an all-in-one security team when it comes to securing cloud-native apps. Instead of needing a variety of tools and specialists, CNAPP combines everything. So, CNAPPs are your go-to option if you work in DevSecOps and want to streamline cloud security without compromising security. It simplifies security, minimizes alarms, and maintains the security of your apps.
CNAPP Benefits
- Container scanning
- Infrastructure as code scanning
- Cloud security posture monitoring
- Runtime cloud workload protection platforms

Unified Risk Visibility
A centralized view of security risks and vulnerabilities across cloud-native apps is presented. It keeps an eye on the entire environment and spots any possible threats. For instance, CNAPP can identify vulnerabilities across web and mobile applications. Stakeholders are notified of suspicious login attempts and detect strange traffic patterns. This unified visibility provides continuous service, protects client data, and allows quick response to threats.
Vendor Consolidation
A single platform with full security tools and functionalities makes vendor consolidation simpler. Your security stack is streamlined. This means lower complexity and expenses too! Access control, authentication, encryption, and vulnerability testing are a few of the capabilities. All these synergize and boost operational effectiveness and lower licensing costs. Thanks to the reduced security tool count, teams outperform and hit all the KPIs.
Enhanced visibility and observability
CNAPP gives enterprises more visibility by helping them define and enforce security policies. The biggest advantage is being able to track and analyze behavior in real time. By visualizing the most exploitable attack vectors and developing risk profiles for various assets, runtime environment data may be overlaid on vulnerability scan results. This assists businesses in identifying and responding to potential threats.

Improve continuous compliance
For data protection and security, firms must abide by many laws and standards. CNAPP assists businesses in meeting these standards with a variety of security controls and features that enable ongoing compliance. Here is the list of all the compliance standards and regulations an ideal
CNAPP can fulfill:
- NIST (National Institute of Standards and Technology) Cybersecurity Framework
- HIPAA (Health Insurance Portability and Accountability Act)
- GDPR (General Data Protection Regulation)
- PCI DSS (Payment Card Industry Data Security Standard)
- CIS (Center for Internet Security) Controls
- ISO 27001 (International Organization for Standardization)
- SOC 2 (Service Organization Control 2)
- FedRAMP (Federal Risk and Authorization Management Program)
- FISMA (Federal Information Security Management Act)
Higher scalability and performance
They make sure that security measures don’t have a detrimental effect on how well cloud-native apps function. Encrypted traffic is examined without invasive processing. It is purpose-built with scalability and efficiency in mind.
Compliance with DevSecOps’s promise
A unified platform for understanding and visualizing risk in your environment is created. Development teams have more context for why they need to patch and remediate environment vulnerabilities since risk is approached based on exploitability rather than severity. Security teams have a smaller attack surface to watch for potential threats as a result. These two roles reap the biggest benefit.
DevSecOps Practices
CNAPP integrates with DevSecOps practices by automating security checks. It fosters collaboration between development, security, and operations teams. It’s like having a security expert embedded in your development pipeline. The guiding principle is that security is not an afterthought but an integral part of the application lifecycle.
Consider a scenario where the development team is deploying updates to a cloud-native application. CNAPP can automate security testing, and scan code for vulnerabilities. It also verifies container images for compliance before deployment. This aligns with DevSecOps principles. It allows the team to release secure code faster without compromising on safety.
Agent vs. Agentless CNAPP
The need for agent-based approaches for detection and response vs. agentless-based solutions is a contentious issue. Let us discuss the techniques, their advantages and disadvantages, and how they impact the CNAPP space.
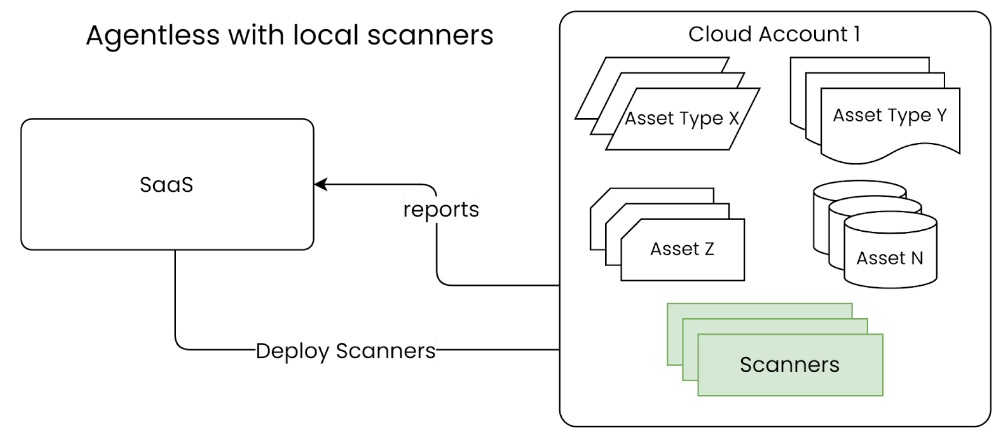
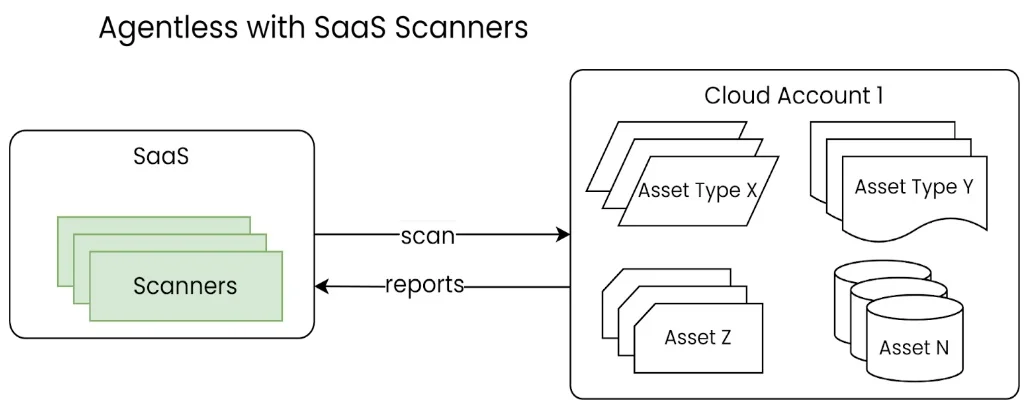

Agentless: What Is It?
It refers to security procedures where no background services, daemons, or processes are required on the machine. They use metadata, APIs, and the cloud to make decisions about security monitoring.
Pros
- Quick Deployment. Agentless technologies provide the first deployment and make the initial security scan the utmost priority.
- Visibility Breadth. When scanning the cloud, agentless technology sometimes takes a mile-wide approach. They do not focus in-depth on specific host-based security vulnerabilities.
- Reduced Maintenance Costs.
- Continuous Security and Compliance for Cloud Services. Agentless techniques keep an eye out for configuration changes. It negates any impact on the cloud’s regulatory or security posture. Businesses push for consistent security and compliance frameworks across all their various contexts.
Cons
- Runtime protection is lacking. As a result, remediation is limited to configuration change. The host or network-based security policy is not taken into consideration. Limited response to such threat actors.
- Lack of Visibility in Hybrid Cloud. It is limited to the public cloud due to the reliance on cloud service provider APIs.
- Focus on deployment speed over security posture tuning. While initial maintenance and deployment expenses are reduced, the security posture is inadequate after the initial deployment. This is due to the inability to do deep packet inspection (DPI) in the cloud and to detect and address threat actor TTPs. Additionally, it gives preference to cloud-wide policies over the ability to set specific security policies at the host level.
Agents – What Are They?
The specialized software components known as agents are installed on computers to carry out operations and actions related to security.
Pros
- Enables deeper inspection of hosts so that agents can do specialized process-level scanning. This is essential for identifying specific threat actors’ tactics, methods, and procedures (TTPs).
- Based on the recognized TTPs in the DPI of network traffic, runtime protection and agent-based approaches to security enable the blocking of traffic at the network and/or host level.
- Attack Path Modeling and Protection. Not just for public cloud APIs but also for hybrid cloud deployments Containers, Linux hosts, serverless, Kubernetes, and other types of infrastructure are among those against which it can identify risks.
Cons
- Prioritize tunability and security.
- Posture Configuration Over Deployment. Initial setup requires time, but once completed, it offers fine-grained control. Agent-based technologies are also incorporated into deployment scripts that run in a hyperscale setting.
- Maintenance costs. With agent-based systems, handling updates, modifications to deployment scripts, and OS upgrades is more of an operational issue.
- Agents that are not suited for high-performance cloud settings may have performance effects on the host.
Experts in the security field have realized that both are necessary for a sufficient level of cloud security. You can learn more about AccuKnox’s agent technology, its security use cases, and its capacity to offer in-depth observability of runtime traffic.
How is AccuKnox CNAPP different?
When examining the CNAPP space, these ideologies are still pervasive. Platforms still favor one technique over another despite having consolidated their feature sets.
Before attempting to stretch oneself too thin, AccuKnox contends that one must be an expert in all major security controls (vulnerability management, CSPM, malware, secrets, etc.).
To understand attack routes in the cloud, it is necessary to correlate agent-based data with agentless scans! We can only update our security posture in hybrid cloud settings by identifying attack vectors.
This way, we can add security protections and controls to get rid of the latest TTP. These are the same TTPs that threat actors use to travel across our environments.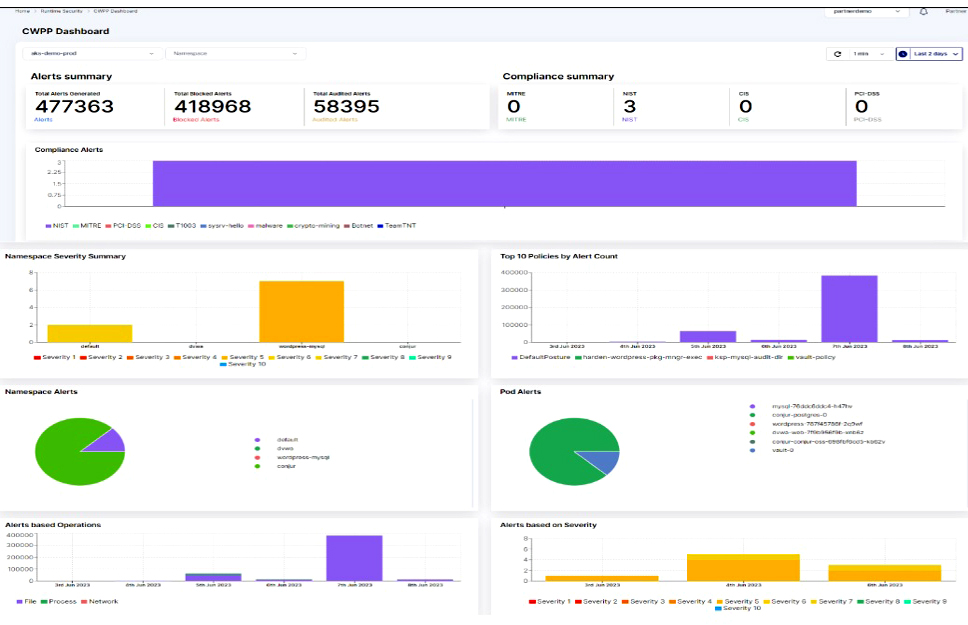

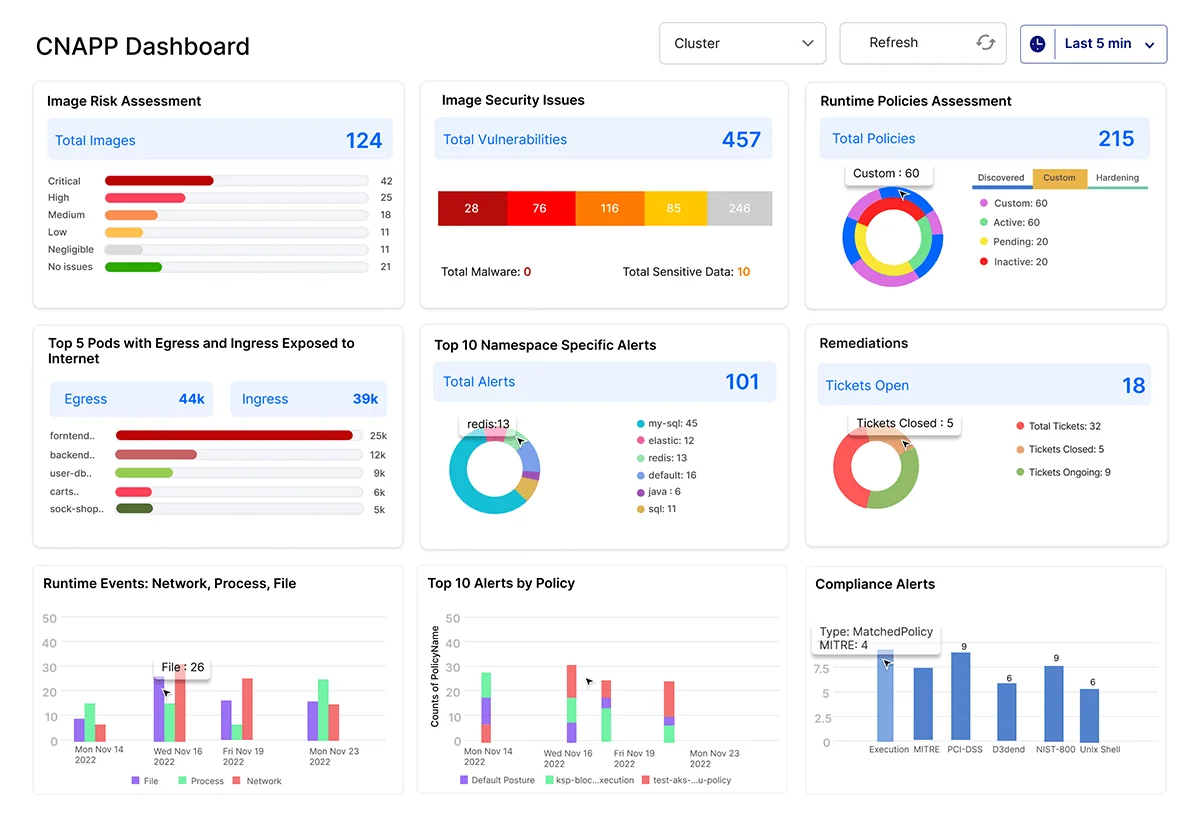
The extra context that cloud agents offer has definite advantages for organizations:
- Cost control. Improve security measures and invest in contexts, such as the exploitability of certain dangers in your environment.
- Alert reduction. Alert fatigue leads to turnover. Security professionals are better able to concentrate on higher-order tasks. (Eg. threat research and security policy authoring) rather than tedious alert triage.
- Consolidation of Security Features. By using a single platform to identify and address risks within their cloud, efficiency and the return on investment (ROI) on remediation is improved. Especially on efforts for key cloud security alerts.
Early players in the market chose to lead with “agentless” versions of these services. This is because the speed and simplicity of deployment were priorities. They relied on cloud API controls to notify businesses of security misconfigurations and remediations. Such an approach is heavily CSPM-focused.
AccuKnox CNAPP platform covers a vast array of cloud security threats to cater to many personas of the user base. Additionally, we double down on administrative simplicity and service coverage of cloud platforms.
Other CNAPP platforms opted to incorporate CSPM capabilities in the cloud as an agentless control plane, but they believed that a more thorough examination of workloads was crucial to the cloud security discussion! They emphasize CWPP and explore essential concepts in depth.
They contend that agentless scanning can only assist you in identifying risks in your environment; they are unable to assist you in determining how exploitable those risks are because they lack knowledge of the runtime traffic or context—what is coming in, what is going out, and what is changing!
The ability to implement security at the process, workload, and TTP levels rather than at the API level of cloud services is another benefit of being deeper on the CWPP side of CNAPP. This is crucial in zero-day circumstances or situations where a possible breach has already taken place.
All Advanced Attacks are Runtime Attacks
Zero Trust Security
Code to Cloud
AppSec + CloudSec

Prevent attacks before they happen
Schedule 1:1 Demo




