
Zero Trust Architecture, Framework and Model – A Comprehensive Guide
Get a comprehensive view of the Zero Trust Model and what powers it to effectively scale and secure your cloud applications
Reading Time: 8 minutes
Table of Contents
Are you struggling to keep up with cyber threats? Traditional security methods aren’t as effective anymore. Cloud computing and remote work have changed the game. They expand the attack surface and make it that much harder to protect data.
💡TL;DR
- This guide goes over the advantages of using a zero trust architecture and how it may assist you in developing a safe framework.
- A zero-trust architecture is necessary to secure data and provide users access to the resources they require to fulfill their tasks.
- Implementing a ZT architecture simplifies security administration by reducing complexity and overhead, sustaining high numbers of users, increasing visibility and control, improving compliance, and lowering costs.
- Its worldwide market is expected to reach US$38.6 billion by 2024. AccuKnox’s CNAPP cloud security platform simplifies compliance, enhances visibility, and strengthens organizations of all sizes’ entire cloud security posture.
- The ZT strategy presupposes zero trust for everyone and everything, whether they are inside or outside the network.
In an organization, the employee usually gets access to all resources within the network once they are authenticated through SSO. This could lead to data breaches as an attacker might be able to brute force his access into the network and all of the sensitive data could be exposed. Therefore, a Zero Trust (ZT) architecture is required, where users are allowed to have access to resources they need to complete their job, in order to have protection from insider threats and external attacks. And there is a constant need for monitoring and re-evaluation of those access controls behavior.
Data Integrity is a concern due to data often stored on centralized servers or volume mount points. This makes it a tempting target for attackers. Zero trust advocates for the use of decentralized data storage, which makes it more difficult for attackers to steal data.
Installing firewalls and antivirus software protects against malware attacks. But attackers can bypass these defenses if they have internal access to the network. Zero trust is better. It uses a layered approach to security that includes things like micro-segmentation, least privilege access, and continuous monitoring. This makes it more difficult for attackers to invade the network and to move laterally.
Implementing a zero trust architecture (especially in the network layer) has a ton of benefits.
- Simplifies security management
- Reduces complexity and overhead
- Sustains large numbers of users
- Increases visibility and control
- Improves compliance
- Reduces expenses by downsizing the cost implications for expensive hardware and software solutions
An environment without zero trust is more vulnerable to security risks. It is no surprise that the most effective and successful enterprises use ZT network security for protecting data and assets.
Zero trust works well with other automated practices like DevSecOps and NoOps. APIs help manage systems in a zero trust manner. Cloud services provide extra security. Microsegmentation is a key part of zero trust. It divides networks, data, and applications into smaller units. This microsegmentation helps contain breaches and limits access to sensitive data. A ZT Framework removes the assumption of trust in security. Every action, user, and device must pass an authentication check for a stronger security posture. It benefits both organizations and end-users.
Consider these questions to judge the need for ZT
- Have you faced challenges with traditional cybersecurity methods?
- How would you handle the insider threat in a changing IT environment?
- Are you familiar with micro-segmentation and how it helps contain breaches?
- Do you require conformance to compliance regulations continually?
Zero trust architecture works with DevSecOps and NoOps. They embed automation and orchestration capabilities. APIs provide a consistent control layer for system management. Cloud services leverage security investments made by cloud vendors.
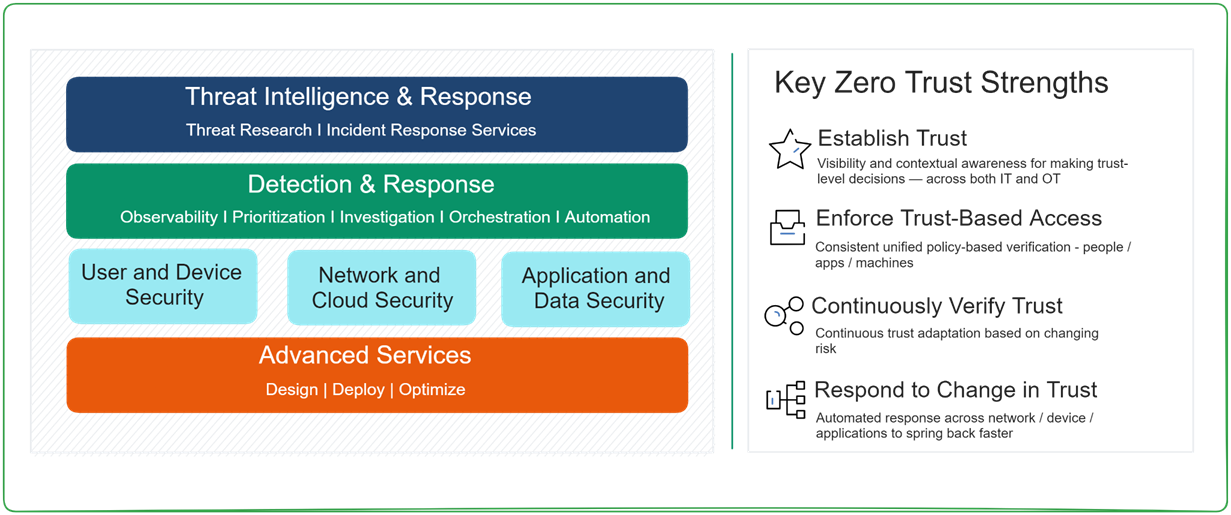
Zero Trust Framework
When adopting a zero trust approach, there are important design principles to consider. These principles build on existing security investments and processes.
- Data discovery and classification. Understand your data, where it’s located, how it’s classified, and who should have access to it. This creates trust zones and access controls.
- Asset discovery and attack-surface management. Keep an updated inventory of all IT resources. Include cloud and external assets. Make identification of security issues across the attack surface easier.
- Configuration and patch management. Manage configurations and apply patches. This prevents the exploitation of vulnerabilities.
- Identity and access management. Standardize and automate identity processes. Ensure the right people and devices have access. All this is via cloud services and advanced authentication. CNAPP solutions often rely on the Multi-Factor Authentication method as an added layer of security to the login.
- Third-party risk management. Understand risks from supply chains and partners. Assess the risk surface of dependencies and cloud native applications.
- Logging and monitoring. Use automated systems with AI and machine learning. Track and analyze data to detect potential incidents.
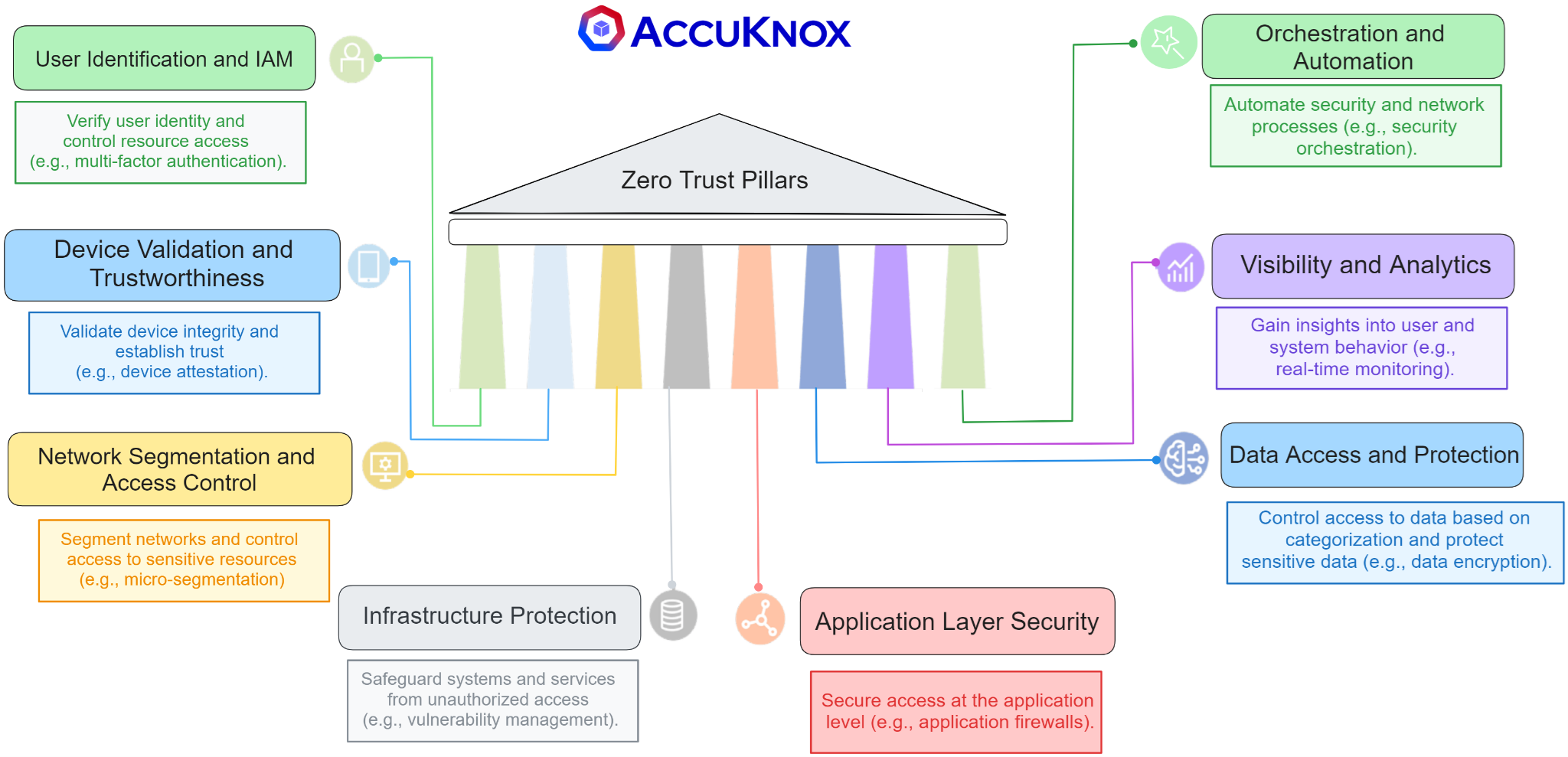 NIST SP 800-207 explains Zero Trust: a safe network foundation without implementation specifics. It ensures compatibility, defends against modern threats, and is appropriate for cloud settings and remote work models. The Biden administration has mandated that all US government agencies use NIST 800-207 as a critical step in combating security breaches.
NIST SP 800-207 explains Zero Trust: a safe network foundation without implementation specifics. It ensures compatibility, defends against modern threats, and is appropriate for cloud settings and remote work models. The Biden administration has mandated that all US government agencies use NIST 800-207 as a critical step in combating security breaches.
NIST 800-207 gains widespread acceptance from businesses, vendors, and government entities. It’s the trusted standard for private organizations embracing Zero Trust.
Zero Trust, guided by NIST principles, focuses on three objectives:
- Continuous verification. Often verify all resources for a secure environment.
- Minimize impact. Reduce consequences of breaches, whether external or internal.
- Automated context collection and response. Combine behavioral data with comprehensive IT context for reliable results.
These principles and practices are much needed in a modern environment. Aggressive implementation of the zero trust approach is the proven way. Adopt the most secure and resilient cybersecurity framework!
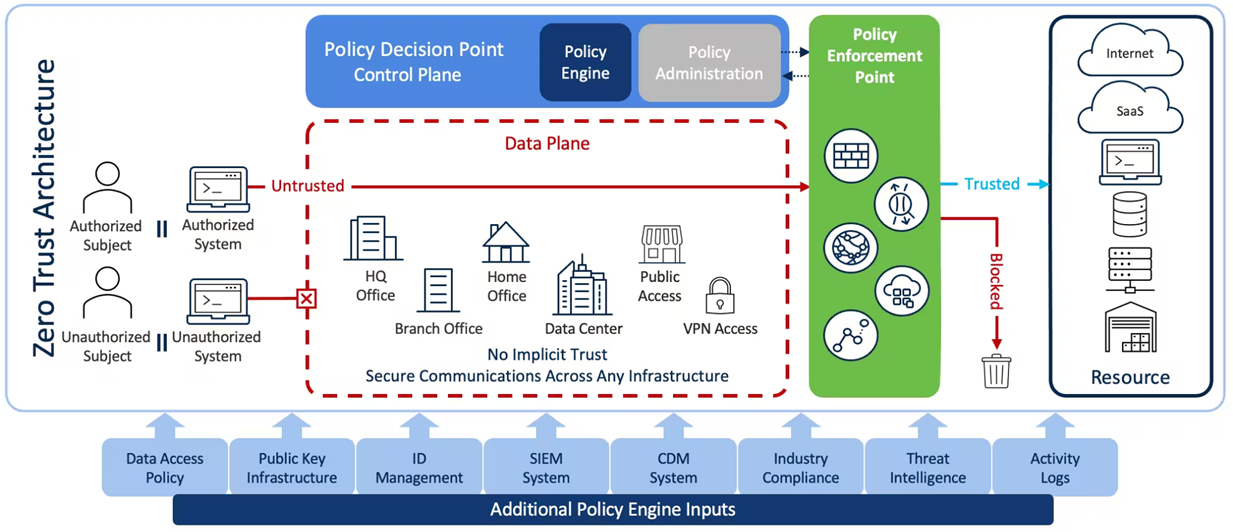
Unlike the traditional belief in trust within the corporate firewall, we challenge this notion. Our zero trust approach assumes a trust level of zero for everyone and everything. Regardless of whether they are internal or external to the network. ZT is not a product: It’s a comprehensive strategy and framework. The entire goal is for organizations to reevaluate their network security approach. It integrates with your current technology stack, adding tools and capabilities as needed. Refer to the seven pillars discussed above. The hallmark of our zero trust philosophy is simplicity. We treat every user, packet, interface, and device as untrusted, simplifying asset protection. Our approach automates tasks, consolidates tools, and addresses vulnerabilities.
Zero Trust examines access requests before granting them to corporate or cloud assets. Real-time insight into various user and application identity characteristics is the biggest factor when it comes to the ZT framework. These include:
- Geolocation.
- Reporting anomalies in usage, activity and recognizing attacks.
- Checking the technique and assessing the risk.
- Always choosing standard connections for credentials and devices.
- Understanding the type and purpose of endpoint hardware.
- Managing access privileges for each device.
- Keeping your operating systems and patches up to date.
- Monitoring installed applications on endpoints.
- Identifying yourself and specifying your credential type.
- Staying informed about firmware versions.
By having a clear view of these attributes, Zero Trust ensures that only trusted entities are granted access. Minimizing the risk of unauthorized entry and potential security breaches.
Zero trust is a journey taken one step at a time. Start with small protected surfaces and create microperimetry. Gain experience, build confidence, and migrate critical assets. Our solution evolves with your security needs.
Cut blind trust, focus on simplicity, and protect your assets. Take the first step with us on your zero trust journey. Together, we’ll strengthen your security posture in a changing threat landscape.
Achieving Zero Trust Security at Every Step
Checklists are a great resource for security engineers and sysadmins. They pinpoint pain points and give actionable steps to sort issues out. Deal with the challenges that arise while implementing the Zero Trust Framework by following the 3-step process:
#1 – Visualize
Identify vulnerabilities and attack vectors to strengthen your defenses. Increase visibility when dealing with different business departments and cloud environments. See the big picture: Understand all resources, risks, and access points. Everything must be visible, from endpoints to identities and workloads. Put in place strong identity and access management (IAM) policies.
#2 – Mitigate
Always keep revising machine learning models and policies. We have a full guide about it here. Use behavioral analytics to detect and respond to threats. Expand automation for faster response time and cost efficiency. Prevent credential theft and limit breach impact with segmentation and least privileged access. Take action against threats and minimize their impact. Cycle secret keys, have a dedicated vault, and keep rotating them frequently. Automate real-time risk mitigation and response. Assess policies before deployment and integrate them into existing workflows.
#3 – Optimize
Provide multi-factor authentication for legacy systems to ensure comprehensive coverage. Address threats in public clouds and SSO credentials. Even without deploying extra sensors. Apply context-based access control to ensure continuous examination of threats. Extend protection to all IT resources without sacrificing user experience.
 Remember, laying out the Zero Trust Model is a journey. Take it one step at a time, and increment security measure optimization. Following this checklist will make all cloud security watertight.
Remember, laying out the Zero Trust Model is a journey. Take it one step at a time, and increment security measure optimization. Following this checklist will make all cloud security watertight.
Actionable Plans and Use Cases
Zero Trust Application Posture
Ensure providing access to applications is based on user identity and context. Authorized users can access the application through a 2-factor authentication.
Implement Microsegmentation:
The default posture of most of the applications running in Kubernetes can communicate to other pods in a namespace even when there is no business or technical logic that requires them to. Hence, microsegmentation is very much a security technique that divides a network into small, isolated segments and gives users granular control as to “who gets to talk to whom?”. So in case of a breach, it will ensure there is no lateral movement or reconnaissance.
Enforcing least privilege access:
As the father of Zero Trust, John Kindervag emphasized the need to allow a specific set of applications through a whitelist and deny everything else, which significantly reduces the number of ways an organization can be attacked. Hence, least privilege access becomes very important where the machine identities as well as users must only be granted the access/permission they need for the app to run. It will ensure that the risk of unauthorized access to data is minimized.
Identity and Access Management
IAM manages user identities through authentication, allowing access to groups performing similar operations and management tasks, and authorizing access rights. This ensures that only authorized users have access to the applications and data to perform the task that they are supposed to as unused high privilege permission could be compromised.
Continuous Monitoring
The applications in a CI/CD pipeline need to be agile to push different versions/fixes. Also, the cloud resources as a part of the infrastructure could continually be detected for Compliance Drift and misconfigurations—because even if you get to Zero Trust, the harder problem is to stay Zero trust; therefore, feature-set like Anomaly Detection and Drift Detection helps. Also, the logs and telemetry could be proactively monitored through SIEM integration and can be responded to quickly before they cause damage.
Conclusion
Gone are the days of “trust but verify.” Advanced threats can now breach the organization’s perimeter. We need a new approach. Specifically, a ZT architecture that protects enterprise data, whatever the location of users and devices.
Boost your security with these simple steps:
- A “Never Trust, Always Verify” paradigm: Start with a least permissive approach to security within your network. Don’t trust anything!
- Micro-Segmentation: Isolate your workloads for added protection. Keep them separate and secure.
- IAM Solutions: Put in place strong identity and access management solutions. Control who can access what.
- Proactive Monitoring: Stay one step ahead by monitoring for any anomalies. Detect and respond to any potential threats with Drift-Detection.
Adhering to the above points strengthens security and moves you closer to a robust Zero Trust Architecture for SaaS applications.
Users, devices, applications, and data are no longer confined to the organization’s perimeter. At least not in today’s modern digital landscape. Spread across different locations, traditional security perimeters prove ineffective, thus increasing the risk and threatening the security of businesses undergoing digital transformation.
Takeaways
- The workforce is becoming more mobile, accessing applications from multiple devices.
- Relying on user credentials for access is risky. It exposes organizations to security threats.
- Traditional security perimeters are no longer effective in the digital era.
- Zero Trust network architecture provides enhanced security and seamless application performance.
- Digital transformation requires a new approach to security to stay competitive.
All Advanced Attacks are Runtime Attacks
Zero Trust Security
Code to Cloud
AppSec + CloudSec

Prevent attacks before they happen
Schedule 1:1 Demo




