
Zero Trust Use Cases
Our Zero Trust Framework secures cloud environments by implementing access controls, micro-segmentation, and monitoring. This helps to prevent unauthorized access, limit lateral movement, and detect attacks. Read how we secure multi-cloud environments by implementing access controls, micro-segmentation, and monitoring.
Reading Time: 19 minutes
Table of Contents
Cloud computing has revolutionized how businesses operate in our connected world. Why is strong security crucial? Traditional defenses aren’t enough. That’s where Zero Trust Security comes in.
Zero Trust Security challenges the old notion of trust within networks. Its principle is simple: “never trust, always verify.” Verify and authenticate every user, device, and application before granting access.
💡TL;DR
- Zero Trust Security means never assume trust but always verify devices, networks and people Attackers, after gaining access to the container, instantiate a new process (remote code execution), change trusted certificate bundles, and exfiltrate sensitive passwords.
- Establish trust among containers to reduce the chances of malicious entities infiltrating communication channels.
- By implementing micro-segmentation, application firewalling, network firewalling, continuous compliance, and workload hardening, kernel hardening strengthens the basis of security.
- The execution of unauthorized processes, backdoor operations, network interface usage, file system manipulation, and administrative tasks are all prevented by these security measures.
- It also enforces fine-grained app-level audits and alerts, apply strong identity management, and use container forensics for in-depth investigation and debugging.
In this article, we will dive deep into Zero Trust use cases.
You will:
- Understand the importance of cloud security and the limitations of traditional approaches.
- Explore the concept of Zero Trust Security and its underlying principles.
- Learn how Zero Trust can provide enhanced protection in the cloud.
- Discover real-world examples and case studies showcasing Zero Trust’s effectiveness.
- Gain practical insights for implementing a Zero Trust framework in your organization.
Zero Trust Security: Building Trust Through Continuous Verification
Zero Trust Security is a game-changer in cloud security. Instead of trusting everything, we adopt a proactive and comprehensive approach. So, what does that mean for you? It means we never assume trust but always verify. Treating every access request as risky is the norm. It does not matter where you are or what network you’re using. This ensures consistent and robust security across all layers of your organization. From users and devices to applications and data. It’s like having a security guard at every door, checking IDs, and making sure only the right people get in.
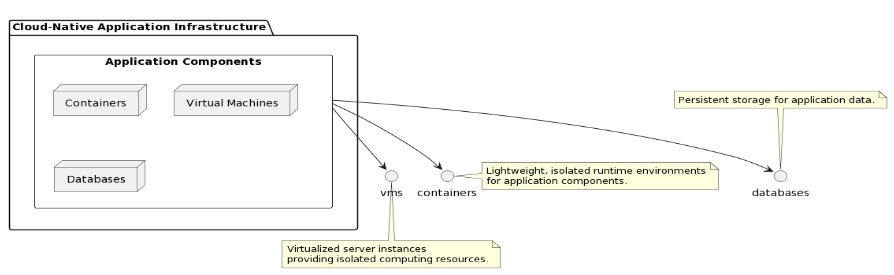
Key Principles of Zero Trust Security
Zero Trust Security doesn’t assume trust once someone’s on the network. Why is that important? Well, think about it: Shouldn’t we verify every access request to make sure it’s legit? That’s what Zero Trust Security does. It uses authentication and smart policies to confirm user or machine identity. So, even if someone slips through the cracks, suspicious activities won’t go unnoticed.
But it doesn’t stop there! Zero Trust Security also controls access with precision. Instead of giving everyone free rein, it follows the principle of least privilege. That means users and devices only get access to what they need. It’s like having a special key that unlocks exactly one door—no more, no less. This limits the damage if something goes wrong. Bad actors can’t move around undetected.
- Elimination of Implicit Trust
- Continuous Authentication
- Strict Access Controls
You gain better visibility, control, and resilience against ever-evolving threats. It’s a proactive approach that goes beyond the old-school perimeter defenses. A security system that protects your precious data, applications, and systems with vigilance. That’s the power of Zero Trust Security!
Kernel Hardening: Strengthening the Foundation
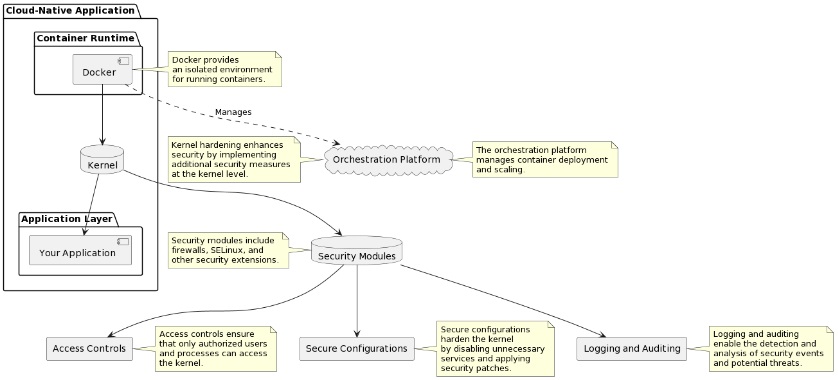
Kernel hardening protects the core of your operating system. But why does it matter? Think of it as adding extra armor to your system to defend against potential threats. By patching and configuring the kernel, we reduce vulnerabilities. This means better protection and fewer chances for bad actors to exploit weaknesses.
How does it make a difference?
- Enhanced Protection
- Mitigation of Vulnerabilities
- Access Control
- Prevention of Privilege Escalation
Access control is another perk of kernel hardening. It makes sure that only authorized entities can access critical system resources. Imagine having a bouncer at the door, letting in only the VIPs and keeping the troublemakers out. And let’s not forget about privilege escalation. Kernel hardening techniques make it difficult for attackers to gain elevated privileges. The impact of potential attacks is minimal.
At AccuKnox, we understand the importance of kernel hardening for comprehensive application security. Check out our solution page for a deep dive into how we achieve kernel hardening. Our products take care of secure configurations, system hardening, and continuous monitoring. Explore our approach, architecture, and tailored features that strengthen your cloud security infrastructure. Visit the AccuKnox Solution page today!
Micro-Segmentation: The Power of Segregation
In network security, micro-segmentation is a powerful way to protect your cloud environment. How does it work? It provides control and isolation by breaking the network into smaller segments. These isolated segments are manageable and not vulnerable to the same attack strategies. This approach prevents threat elements from moving around and gaining unauthorized access.
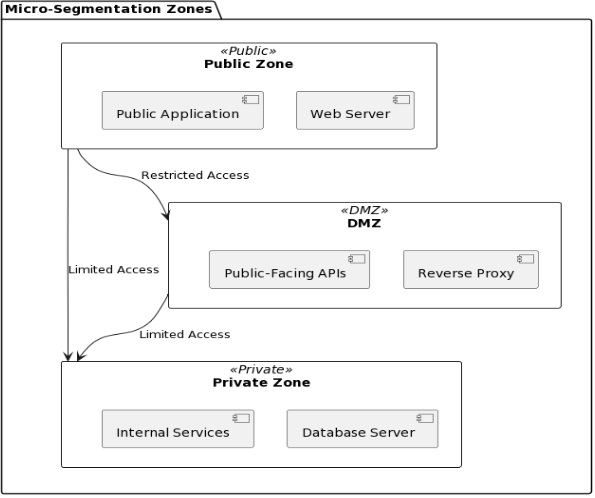
Notable benefits include:
- Enhanced Security. By isolating workloads and applications, you reduce the attack surface. Also, it limits the frequency of breaches. Threats can’t spread throughout the network.
- Granular Control. You can fine-tune communication and enforce precise access policies at the workload level.
- Compliance and Regulatory Requirements. Micro-segmentation helps organizations meet regulatory requirements by enforcing segmentation and access controls. It provides a clear audit trail, making data flow transparent and accessible.
But what sets micro-segmentation apart? Unlike traditional network segmentation, it allows you to set specific security rules. These rules apply over workload or application and are customizable. You have granular control over how they communicate.
At AccuKnox, we offer a comprehensive solution for micro-segmentation. Our solution combines network visibility, policy management, and segmentation enforcement. With AccuKnox, you can isolate workloads, control access, and protect your cloud environment.
Curious to learn more? Visit our AccuKnox Solution page for details on how we achieve micro-segmentation. Explore our architecture diagram and specific AccuKnox features designed to strengthen your security. With micro-segmentation as part of your security strategy, you gain precise control. And that is not all! You also gain stronger defenses, reduced risk of unauthorized access, and faster development iterations.
Application Firewalling: Restrict Access, Restrict Threats
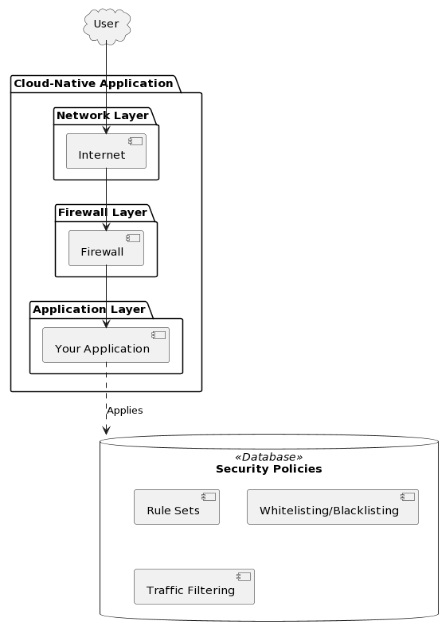
In the context of cloud native applications, application firewalling provides several benefits:
- Enhanced Security. Using application-level firewalls safeguards your applications from known vulnerabilities and malicious activities. It keeps your applications intact and available.
- Granular Access Control. You can define who can access your applications and what they can do. Only whitelisted and authorized traffic reaches your applications, keeping unauthorized access at bay. Open the doors for RSVP’d guests. Reject everyone else right at the door.
- Threat Detection and Prevention. Application firewalls use different techniques to identify and block threats in real time. They stop attacks, such as exploiting vulnerabilities or unauthorized actions. All this safeguards your data and applications.
- Compliance and Data Protection. Application firewalls assist in meeting regulatory requirements and data protection standards. They enforce security policies, protect sensitive data, and track application access and activities. Examples include GDPR, HIPAA, and PCI-DSS.
Real-world examples show how application firewalling makes a difference. In e-commerce, it thwarts SQL injection attacks, protecting customer data. In healthcare, it prevents unauthorized access to patient records. In schools and universities, it blocks students from accessing administration. Achieving compliance with privacy regulations becomes easy.
At AccuKnox, we offer a comprehensive solution for application firewalling. Our solution combines intelligent traffic analysis, filtering, and behavioral analysis. With AccuKnox, you can detect threats, control access, and bar unauthorized entry.
To learn more about our application firewalling approach, visit our AccuKnox Solution page. Add application firewalling as part of your security strategy. Say yes to the availability of your applications. Take the first step to mitigate risks and safeguard sensitive data.
Network Firewalling: Safeguarding Network Traffic
Network firewalling is vital for securing your cloud environment. It controls incoming and outgoing traffic, allowing authorized communication and blocking unauthorized access.
Why should you bother with network firewalling for securing the cloud environment?
- Keeps unauthorized entities out
Your cloud environment is a fortress and the network firewalls are the gatekeepers. They enforce access control policies. Only legitimate traffic enters your network while keeping unauthorized entities at bay.
- Controls incoming traffic
Network firewalls analyze incoming network packets based on predefined rules. If a packet matches a rule that permits the traffic, it is allowed to pass through. If not, the firewall blocks it, protecting your cloud resources from potential threats.
- Manages outgoing traffic
Network firewalls also check and control outgoing traffic from your cloud environment. This prevents data exfiltration attempts from compromised systems within your network. Blocking suspicious or unauthorized outbound traffic, firewalls add an extra layer of security.
- Thwarts network-based attacks
Network firewalls play a major role in preventing various network-based attacks. Identification and blocking DDoS attacks is where network firewalling shines. It doesn’t stop there. Port scanning attempts and intrusion efforts are also evaded. By recognizing and blocking malicious traffic patterns, firewalls safeguard your cloud infrastructure.
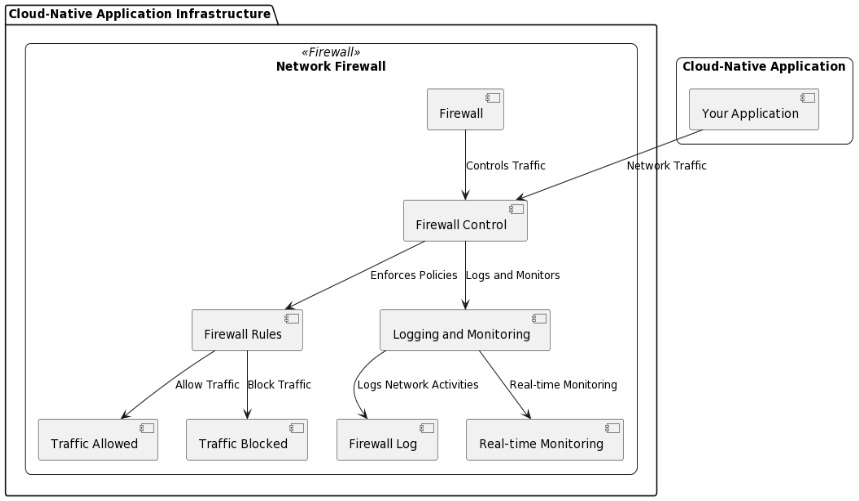
How does AccuKnox deliver advanced network firewalling solutions?
We have specialized network firewalling solutions designed for securing cloud environments.
Robust firewall capabilities
We provide powerful firewall features. We have granular management for incoming and outgoing traffic in your cloud environment.
Cloud-native features
Our solution is tailored to the unique requirements of cloud environments. We take care of seamless integration and optimal performance.
AccuKnox offers bleeding-edge network firewalling solutions. Combine robust capabilities with cloud-native features. Never compromise on control!
Network Firewalling Pros
- Mitigating DDoS attacks
Network firewalls detect and block massive traffic floods from many sources. This minimizes the impact of DDoS attacks and improves the availability of cloud services.
- Preventing malware infections
Blocking suspicious incoming traffic and unauthorized communication is the primary aim. They act as a frontline defense against malware infections.
- Blocking unauthorized access attempts
Firewalls prevent unauthorized access, such as brute-force attacks and unauthorized login attempts, which reduces the risk of unauthorized data breaches.
Network firewalling controls incoming and outgoing traffic, preventing illegal communication and defending against network-based attacks. AccuKnox has advanced firewall solutions tailored for applications running in the cloud. But that’s not all. We also have on-prem air-gapped or VM/Baremetal environments. We ensure robust protection for your cloud infrastructure and its associated application. To learn more about AccuKnox’s approach and architecture, see how we built it.
Continuous Compliance & Workload Hardening: Strengthening Security Posture
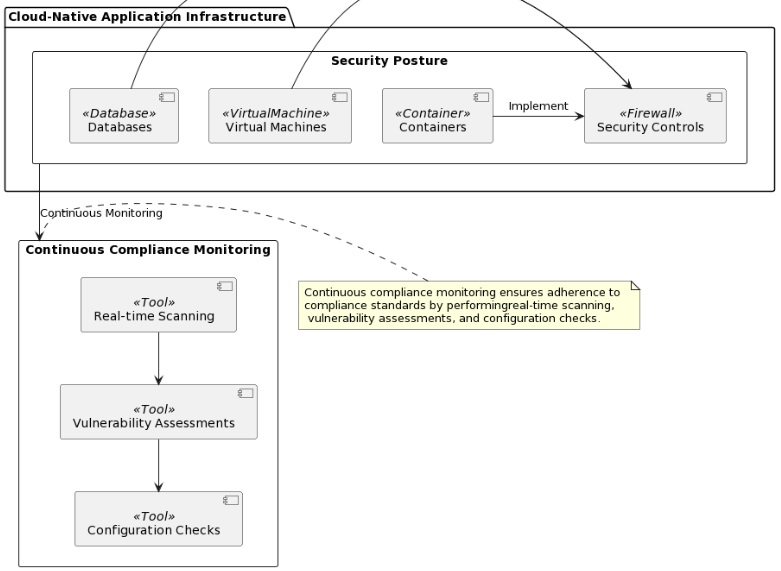
To keep your cloud environment secure, you need to pay attention to two things. Continuous compliance and workload hardening. Let’s understand why these practices are important. This is the first step in making your security defenses stronger.
Why should you care about continuous compliance and workload hardening?
- Continuous compliance keeps you up to date with security standards. Security standards change rapidly, so it’s important to stay updated. Continuous compliance practices assist in following the best security practices. This will help in meeting the required standards.
- Workload hardening reduces attack radius. Workload hardening means taking steps to make your cloud workloads more secure. By doing this, you make it harder for attackers to find vulnerabilities. It will be no easy feat to break into your system.
Continuous compliance and workload hardening are like superheroes. They protect your Cloud Native apps from bad guys.
How do these practices cut vulnerabilities and ensure security standards?
Continuous compliance
- Regular audits and assessments
Conduct security audits. You can find any weaknesses in your cloud environment and fix them. - Automated compliance checks
Using special tools, you can check if you are following the security standards. Take preventative measures and act faster if you’re not. - Auto-remediation and documentation
Keep a record of fixed security systems. This historical data will help you map security policies across new apps. Follow rules, document them, and share them with your team.
Workload hardening
- Patch management
Keep your cloud workloads updated with the latest security patches. This makes it harder for attackers to exploit known vulnerabilities. - Security configuration
Set up strong security settings like strong passwords and an access controls list. There can never be too much protection for your cloud workloads. - Intrusion detection and prevention
Set up strong security settings like strong passwords and an access controls list. There can never be too much protection for your cloudUsing systems that can detect and stop attacks before they do any damage helps keep your cloud safe.
Real-world examples where organizations achieved high compliance and workload hardening:
- Banks and financial institutions follow strict regulations, e.g., Payment Card Industry Data Security Standard (PCI DSS) to protect sensitive customer information.
- Healthcare providers adopt the Health Insurance Portability and Accountability Act (HIPAA). This has regulations and instructions to safeguard patient data.
- Government agencies have tight security requirements to protect sensitive information and national infrastructure.
AccuKnox offers solutions that can help you with these practices. To learn more about how AccuKnox can help, visit our dedicated page. See our architecture diagrams, business logic, and more details on why we are the best choice for you.
Preventing Unauthorized Process Execution and Termination
Unauthorized process execution and termination in cloud native applications is a major threat. It refers to the unauthorized initiation or termination of processes without proper control. How can this be a problem? Well, it can lead to disruptions, security breaches, and data loss.
Let’s look at a real-world example: the attack on Tesla’s AWS infrastructure. An unauthorized third party accessed Tesla’s Kubernetes console. It did not stop there. They began unregulated and unauthorized cryptocurrency mining processes. This caused resource compromise and performance issues.
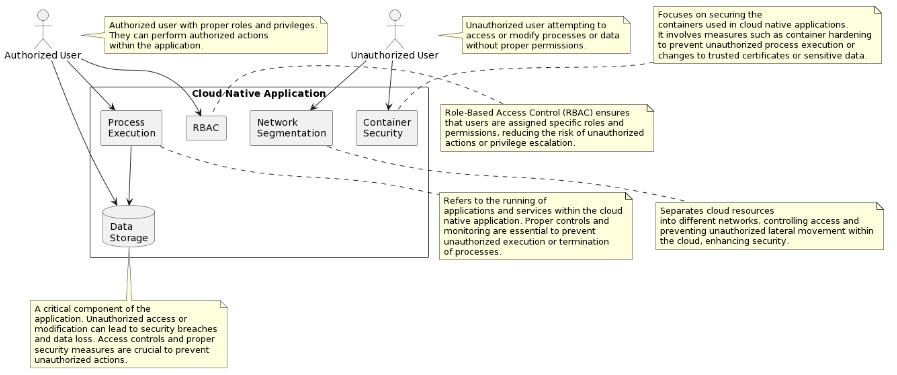
To prevent such unauthorized actions, you need a multi-layered approach. What are some effective methods?
- Put in place role-based access control (RBAC). This means assigning specific privileges to authorized users based on their roles. It limits the chance of unauthorized actions or privilege escalation.
- Use network segmentation.By separating cloud resources into different networks, you can control access and prevent unauthorized lateral movement within the cloud. This reduces the risk of unauthorized lateral movements and reconnaissance.
- Follow container security best practices. Containers are often used in cloud native applications, so secure them. Generally, there are no restrictions or security controls inside a container. Attackers, after gaining access to the container, instantiate a new process (remote code execution), change trusted certificate bundles, and exfiltrate sensitive passwords. To protect these containers against any kind of attacks, container hardening is necessary.
AccuKnox has developed a foolproof solution to combat unauthorized process execution and termination. Some pros are access control, network segmentation, container hardening, and kernel hardening: guaranteed robust protection for your cloud infrastructure and its associated application. Choose AccuKnox to build and ship with confidence.
Preventing Backdoor Fetch-Store-Exec Operations
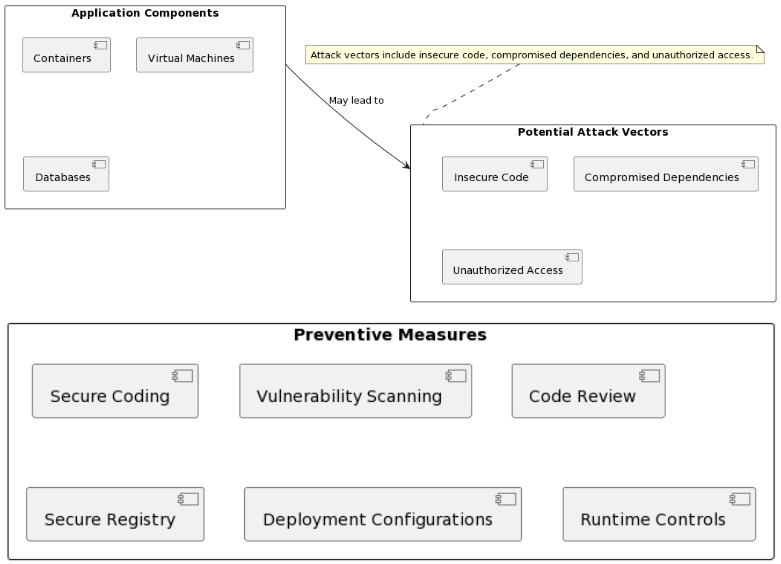
Understanding backdoor fetch-store-exec operations and their potential threats helps you take the necessary precautions.
What are backdoor fetch-store-exec operations and why are they dangerous?
- Backdoor fetch-store-exec operations involve unauthorized retrieval, storage, and execution of malicious code. Illegal execution of commands in a system is also a threat.
- Attackers exploit backdoors to gain unauthorized access and steal sensitive data. In certain cases, they can override system controls and permissions.
- Backdoors can go undetected for long periods. This allows attackers to maintain persistent access.
Backdoor fetch-store-exec operations are like secret tunnels. Attackers sneak into your system and you might never detect it. Not until it is too late.
How can you prevent and detect backdoor activities?
- Use secure coding practices. Prevention is better than cure. Negate the introduction of backdoors during software development.
- Conduct regular vulnerability assessments to identify and patch potential entry points. Say goodbye to insecure backdoors.
- Do not suffer another backdoor insertion attack. Enforce strong access controls to limit access to critical systems.
- Set up network monitoring tools. They detect unusual network traffic patterns and suspicious activities.
- Use intrusion detection systems to identify and alert you to potential backdoor activity. Get it installed.
- Conduct security audits and establish an incident response plan. This will help you in addressing backdoor termination failure.
Real-world case study showcasing the impact of preventing backdoor activities:
- In the SolarWinds supply chain attack, attackers inserted a backdoor. It gave them root access to SolarWinds’ software update system. This compromised organizations that relied on SolarWinds and led to a loss of confidence.
Early detection of backdoor activities can mitigate the impact of such an attack.
This attack highlights the importance of robust security measures. Taking care of insecure backdoors is a good first step for organizations. Especially those who have a distributed cloud workload.
AccuKnox offers advanced security solutions designed to prevent backdoor fetch-store-exec operations. Learn more about our solutions and how it has helped our customers. Visit our dedicated page that narrates our success in stopping attackers. Right at the backdoor!
Restricting Unauthorized Network Interface Usage
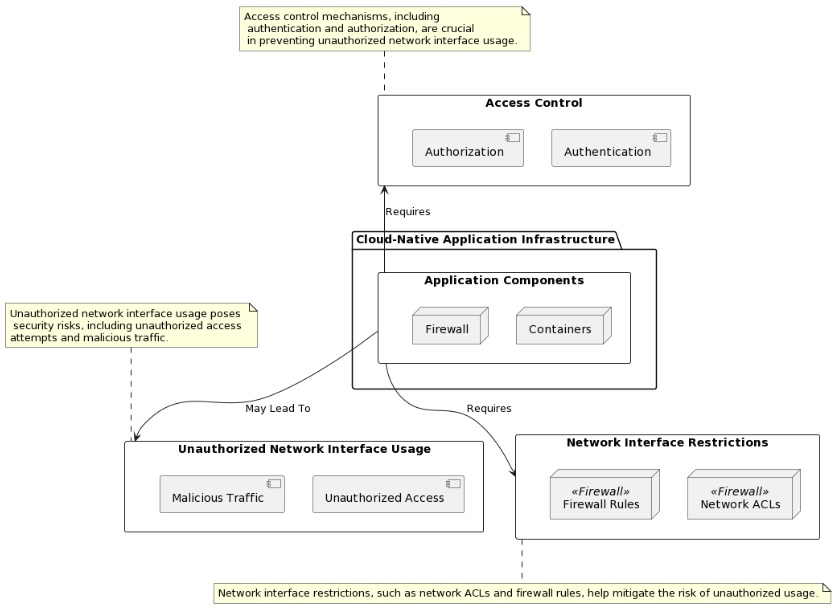
Unauthorized network interface usage in cloud environments can cause major problems.
Data breachesUnauthorized access to network interfaces leads to theft of personal data.
Malware and ransomware attacks
Hackers and crackers use it to their benefit to sneak in nasty computer viruses. These encrypt system files and then propose a ransom. It’s like a thief breaking into your house and making a big mess!
Unauthorized system changes
They can make changes to the system that usually cause catastrophic losses. It’s like someone hacking into your video game and messing up all your progress!
Resource abuse
Unauthorized network interface usage hogs up all the computer resources. This may include bandwidth, processing power, locking files, and storage. This makes everything slow and glitchy. It’s like someone using up all the water in the swimming pool, leaving nothing for you to swim in!
To keep things safe, we can use these methods to control and check network interfaces:
Network segmentation
Imagine dividing your room into sections. This helps keep things separate and makes it harder for someone to sneak into your stuff. The same goes for network interfaces!
Access controls and authentication
It’s like having a super secret password or a special fingerprint that only you can use to open your diary. Strong passwords and challenges help to verify identity. Only authorized people can use network interfaces.
Encryption
Encryption is like turning messages into secret codes. This means messages can only be deciphered by people intended to read them – people who have the key to the code. A good technique to take care of this is Transport Layer Security (TLS). This fortifies the communication between network interfaces. Hence, it keeps the bad guys from listening in.
Monitoring and logging
We can set up cameras and keep a record of who comes in and out of a room, right? The same goes for network interfaces! We can keep an eye on what’s happening. Check network traffic and keep logs, so we can catch any suspicious activities.
Intrusion detection and prevention systems (IDPS)
Use special software that analyzes the network. This will let you know about any unauthorized activities in real time. You install a security personnel that never rests: airtight security. Early detection is the key to maximizing security.
Regular security assessments
It’s important to check for any weak spots and fix them before the bad guys find them. It’s like checking your bike’s brakes before riding. We can test the security of network interfaces to make sure everything is safe and sound. Documentation of this process and having a checklist is a good idea.
Restricting network interface usage has proven effective in real-world situations.
Here are a couple of examples:
1. Bank controls kept hackers away, securing customer information and money.
2. Hospital restrictions blocked unauthorized access, protecting patient privacy and care.If you want to learn more about how AccuKnox can help control and track network interfaces in the cloud, check out the AccuKnox Solution page.
Mitigating Unauthorized File System Manipulations
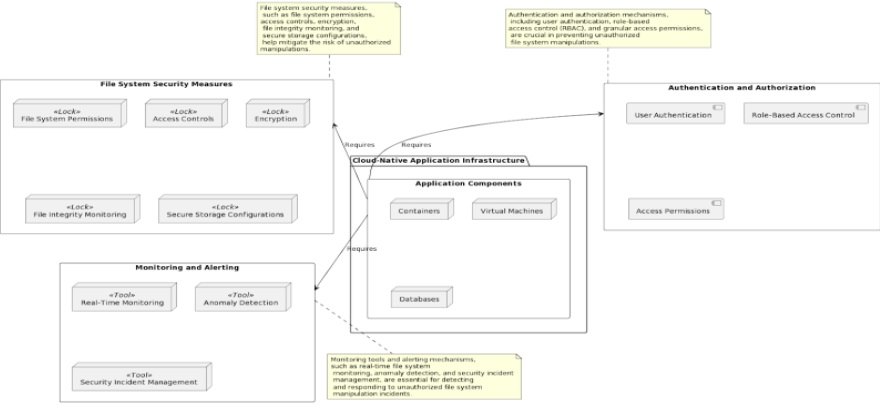
Unauthorized file system access results in disruptive changes to files, directories, or structures without permission – which risks data loss, corruption, disruptions, and security breaches. Prevent it with security measures and access controls.
Risks of unauthorized file system manipulations in the cloud:
Data loss or corruption
Imagine someone sneaking into your computer and deleting or changing important files. Unauthorized file system manipulations lead to the loss or corruption of important files. It’s like losing all your favorite photos or having your important work go poof!
Service disruptions
When someone messes with the file system, it can cause things to stop working. It’s like the electricity going out and your favorite TV show getting interrupted.
Security breaches
Unauthorized file system manipulations can let malicious entities access sensitive information.
Apply the tactics given below to stay foolproof
Access permissionsThink of access permissions like having locks on doors. We can set up permissions on files and folders to control who can read, write, or delete them. It’s like having a secret code that only the right people know. That way, no one else can mess with your files!
Audit trails
It’s like being a detective! We can keep a record of all the actions taken in the file system, and a log of all the activities and events. That way, if something goes wrong, we can track down who did it and stop them in their tracks!
Encryption
In a nutshell, encryption means turning files into secret codes that only the right people can understand. We can use special techniques to protect our files with encryption. Even if someone tries to mess with them, they won’t be able to make sense of anything. It’s like having an invisible shield around your files!
Integrity checks
Use integrity checks to make sure our files haven’t corrupted. It’s like having a special seal that shows if something has been opened or changed. You want to make sure our files stay the way they are!
Mitigating unauthorized file system manipulations has made a big impact in real-world situations:
In large enterprises, strict access controls prevent employees from deleting important project files. This saves everyone from a big headache and extra work.
Government agencies encrypt sensitive documents to keep them safe from unauthorized access. This ensures the privacy and security of important information. Double protection!
Discover how AccuKnox can help mitigate unauthorized file system manipulations in the cloud. Check out our dedicated page highlighting all the details. We have architecture diagrams and behind-the-scenes information that powers our solutions.
Safeguarding Against Unauthorized Administrative Functions and Command Invocations
- Unauthorized admin functions and commands can compromise security.
- They may lead to data breaches and system instability.
- Implement strong access controls and permissions to tackle this.
Potential dangers of unauthorized actions
Data breaches. Unauthorized access to administrative functions results in sensitive data compromise. It is a catalyst for financial losses and reputational damage.
System instability. Illegal invocation of commands can lead to unintended system changes, which further causes failures, downtime, and disruption of business operations.
Malicious activities. Malicious activities allow attackers to execute malicious code and install backdoors, gaining permanent unauthorized control over the system. Bypassing security becomes trivial.
Strategies to put in place strong access controls and permissions:
Principle of least privilege. Grant users only the least privileges needed. Limit access to sensitive functions and commands.
Role-based access control (RBAC). Define user roles with specific permissions. Allow access based on job requirements and permit no other access. This will reduce the risk of unpermitted and illegal actions.
Multi-factor authentication (MFA). Add layers of authentication for administrative functions. Leave no gap in defenses.
Real-world examples highlighting the importance of safeguards:
The 2013 Target data breach. Attackers exploited the credentials of a third-party vendor to gain access to administrative systems. This led to the theft of customer credit card data.
The 2018 GitHub attack. Vulnerabilities in GitHub allowed unauthorized access to source code repositories. Hackers inject malicious code for cryptocurrency mining.
The 2020 Twitter hack. This caused high-profile account takeovers and a Bitcoin scam affecting many users.
Implementing proper safeguards and access controls is vital to protect against impending threats. For a detailed solution on how to achieve this check out how we deal with this issue.
Implementing Strong Identity Management for Cross-Container Communications
Interaction and information sharing across several containers in a computing system is known as cross-container communication. Applications and their dependencies are encapsulated in discrete, lightweight containers. Although independent entities, they cooperate as a coordinated system because of this communication. It resembles a group of persons successfully interacting and sharing knowledge. Combine the functionality of several containers to develop more sophisticated and potent apps by permitting cross-container communication. People can collaborate, share information, and plan their activities to achieve a singular aim.
Importance of robust identity management
Protect sensitive data. Strong identity management makes sure that only authorized containers can communicate: aggressive prevention of unauthorized access to sensitive information.
Mitigate security risks. Establish trust among containers to reduce the chances of malicious entities infiltrating communication channels. Cut off all unauthorized actions.
Ensure compliance. Robust identity management enforces strict authentication and authorization protocols. This boosts regulatory and compliance standards and meets expected requirements.
Let’s explore the techniques used for identity and access management. These techniques authenticate and allow secure communication channels:
Mutual TLS authentication
Install mutual TLS authentication using unique digital certificates for containers. Verify sender and receiver identities.
Role-based access control (RBAC)
Define and manage container roles with specific permissions based on their functions. Only allow authorized containers to interact with designated communication channels.
Secure token-based authentication
JSON Web Tokens (JWT) is the new kid on the block. A secure token authentication system prevents clients from tampering with the data.
Tips to maintain an air-tight infrastructure:
- In a microservices architecture, strong identity management safeguards communication channels. Additionally, it prevents unauthorized containers from tampering with or intercepting sensitive data.
- Enforce network microsegmentation to isolate workloads and restrict lateral movements
- Ensure container hardening to only allow specific process execution and network access which will make it difficult for cross-container communications for activities that are unusual.
Visit our dedicated page. We discuss a comprehensive solution for implementing strong identity management for cross-container communications there.
Enforcing Fine-Grain App-Level Audits and Alerts
App-level audits and alerts in cloud-native apps refer to monitoring and recording of application-level activities. They generate real-time notifications for specific events or violations.
- Audits track user actions, system events, and access attempts.
- Get instant notifications for static and runtime threats or unauthorized activities.
- Both audits as well as alerts provide visibility into potential security breaches.
- Audits help identify permission violations and unauthorized actions.
- Alerts enable prompt response and mitigation of security risks.
Significance
Detecting permission violations: Audits and alerts reveal unauthorized or suspicious activities.
Mitigating security risks: Identify breaches and prevent unauthorized access or data leaks.
Meeting compliance: Ensure adherence to security policies and regulatory standards.
Logging and monitoring practices provide visibility into breaches
Comprehensive logging: Detailed logs trace incidents and permit violations.
Real-time monitoring: Analyze logs for suspicious activities and generate instant alerts.
Behavioral analytics: Detect anomalies and identify security breaches or insider threats.
Real-world examples prove the value of audits and alerts:
- Unauthorized access attempts trigger alerts, preventing data breaches.
- If critical records in healthcare services and applications are changed, the administrators and managers get an immediate alert notifying the location, time with the option to restore the previous data checkpoint.
- Audits and alerts identify suspicious behaviors, preventing fraud in e-commerce.
For an in-depth read, visit the AccuKnox Solution page.
Leveraging Container Forensics for Deep Observability and Debugging
Container forensics means analyzing containers for security incidents and issue resolution.
Examples
- Investigating compromised containers to find attack vectors and the extent of breaches.
- Analyzing container logs, memory dumps, and disk artifacts for detecting malicious activities.
- Examining container network traffic for spotting potential threats and abnormal behavior.
Tips for container forensics
- Enable comprehensive logging to capture detailed container activities.
- Use real-time monitoring tools to detect anomalies and unauthorized activities.
- Perform memory and disk analysis for evidence of malicious actions.
- Analyze container network traffic for identifying threats and unauthorized communication.
- Stay updated with container security best practices.
Container forensics is essential for incident response and deep observability.
Benefits
Analyze security incidents and understand their extent.
Debug issues and improve application performance.
Ease incident response and cut impact.
Faster root cause analysis and context of the attack
Methods
Capture detailed logs and watch container activities.
Analyze memory dumps and disk artifacts for evidence.
Inspect container network traffic for patterns and threats.
Real-world scenarios
Detecting unauthorized access attempts and mitigating breaches.
Resolving performance issues through forensic analysis.
Unveiling suspicious behavior and preventing attacks.
For a comprehensive container forensics solution, visit our dedicated page for this.
Conclusion
We explored several ways to leverage the Zero Trust architecture to your benefit. With AccuKnox, go one step ahead and strengthen your cloud native architecture today.
- We protect against threats with kernel hardening, micro-segmentation, and application firewalling.
- Ensure compliance, workload hardening, and strong identity management.
- Provide deep observability and app-level audits with container forensics.
Ready to step up your security game? Take a moment to schedule a free demo call with us. Experience firsthand the cutting-edge capabilities of AccuKnox. Our solutions leave no room for doubt!
Get The Best Developer and Security ROI
Zero Trust Security
Code to Cloud
AppSec + CloudSec

Prevent attacks before they happen
Schedule 1:1 Demo




