Open Source
KubeArmor is a runtime Kubernetes security engine. It uses eBPF and Linux Security Modules(LSM) for fortifying workloads based on Cloud Containers, IoT/Edge, and 5G networks. It enforces policy-based controls.
INSTALL KUBEARMOR
Runtime Security Enforcement
Securing Kubernetes, VMs, Containerized and Npon containerized Clusters Effectively
- AccuKnox created KubeArmor in 2021 and donated to CNCF
- In 4years scaled from 0 to 1 million+ downloads
- AccuKnox is the core maintainer for Runtime Security in KubeArmor
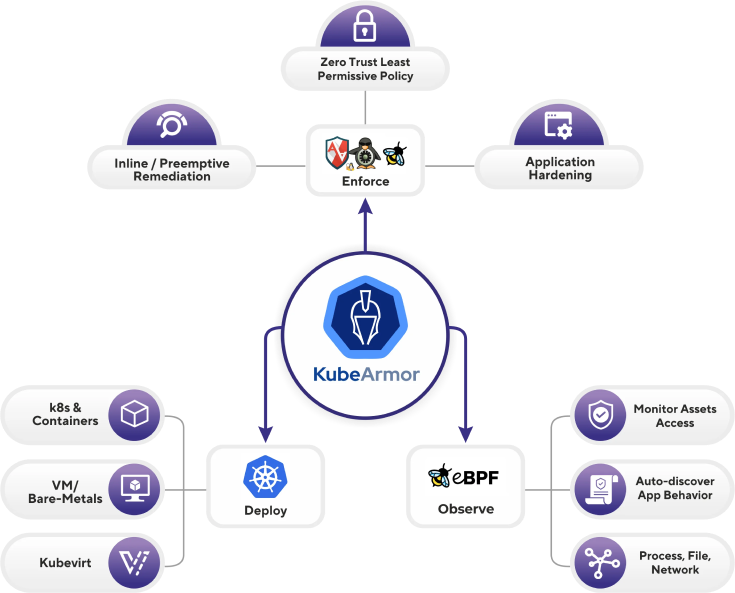

The first K8s Security Engine to leverage BPF-LSM
AccuKnox provides one of the industry’s most comprehensive and integrated CNAPP solution which brings together multiple disparate security modules.
DevSecOps empowering OpenSource Project: KubeArmor
Discover KubeArmor, the renowned open-source project developed by AccuKnox and donated to CNCF. This cutting-edge runtime security solution has gained widespread recognition and adoption among top Global 1000 companies and Cloud Native Unicorns.
KubeArmor github repo can be accessed
here
Unleashing Cloud-Native Runtime Security: The KubeArmor Advantage
KubeArmor stands out as a one-of-a-kind cloud-native runtime security enforcement system. With its exceptional capabilities, KubeArmor effectively restricts the behavior of pods, containers, and nodes at the system level, ensuring robust protection.
Harnessing the Power of Linux Security Modules: Unmatched Policy Enforcement
KubeArmor harnesses the strength of Linux security modules such as AppArmor, SELinux, or BPF-LSM to enforce user-specified policies. This advanced technology forms the backbone of KubeArmor's powerful policy enforcement mechanism.

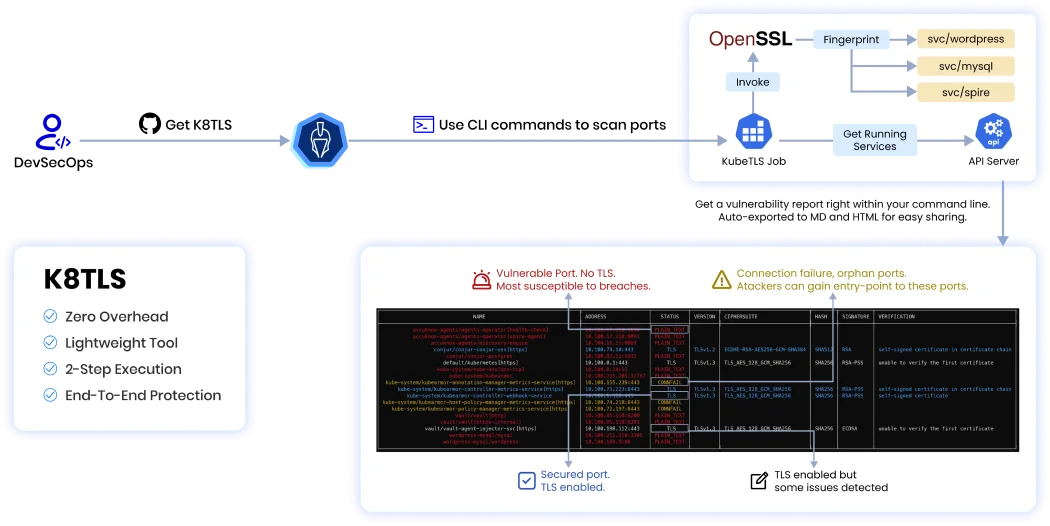
- Verify TLS-enabled server ports and check TLS parameters against best practices.
- Ensure certificates are not expired, revoked. Identify self-signed certificates in the chain.
- Align with compliance frameworks like PCI-DSS, HIPAA, and 5G Security mandates.
- Operates seamlessly in Kubernetes, containerized, and non-containerized environments.
- Automate scanning in CI/CD pipelines for early detection of insecure ports, with JSON reporting for easy integration.
Looking for Kubernetes
Professional Services?
Learn More

KubeArmor OpenSource vs AccuKnox Enterprise
| AccuKnox Runtime Security Features |
|
|
|---|---|---|
| Observability into the workload at granular level |

|

|
| In-line remediation for Zero Day Attacks |

|

|
| Manual apply of Security Policies using CLI |

|

|
| Integration to SIEM for security events and Notification tool |

|

|
| Network security using CNI |

|

|
| Auto-Discovered Behavioural Policies |

|

|
| Recommendation of Hardening Policies based on standard compliance framework – MITRE, NIST, PCI-DSS, CIS |

|

|
| Inventory View of Application |

|

|
| Network Graph View of the Application |

|

|
| Network Microsegmentation in the application |

|

|
| Hardening of the Secrets Managers like Hashicorp Vault, CyberArk Conjur |

|

|
| GitOps based Version Control for Policy Lifecycle Management |

|

|
| Rollback of recently changed Policy governing App Behavior |

|

|
| On-the-fly detection of change in App Behavior through Policies |

|

|
| Multi-Tenant, Multi-Cluster, RBAC for user-management |

|

|
| Comprehensive Dashboard across workloads running in |

|

|
| Managed/Unmanaged Cluster, Containerized environment, VM or Bare Metal |

|

|
| Integration with Registries for Container Image Vuln Scan |

|

|
| Telemetry aggregation (Process executed, File accessed, Network connections made) and Alerts events (Audit, Block) |

|

|

KubeArmor Book
$2.99
KubeArmor is a security solution for Kubernetes and cloud-native platforms that helps protect workloads from cloud attacks. One of the key features of KubeArmor is that it provides these hardening policies out-of-the-box, so you don't have to spend time researching and configuring them yourself. This book provides comprehensive information about open-source cloud security implementation to catalyze your journey to Zero Trust.
ORDER NOWDon’t just take our word for it...

The immense performance efficiencies of Kubernetes can be nullified if they are not hardened appropriately. Kubernetes Hardening Guide from NSA discusses it in good detail. MITRE container security also advocates the security best practices from the attacker's perspective. KubeArmor is the best example of how to achieve NIST & MITRE conformance out-of-the-box. The authors have done a great job of explaining key concepts from the basics, I highly recommend it to Kubernetes practitioners.”
Kubernetes is the de facto Cloud Operating System, yet securing it efficiently and effectively presents a wide-ranging challenge. KubeArmor's use of eBPF for runtime security positions it amongst the next generation of security-enhancing technologies, and this book outlines key concepts in an easily comprehensible format suitable for a wide range of practitioners."
Effective security controls are precise, tailored and targeted. KubeArmor’s approach of leveraging eBPF for kernel telemetry and LSMs for inline remediation provides the deep and precise control needed to thwart advanced zero day attacks. The authors have done an excellent job of explaining key concepts for this new and powerful system.”
KubeArmor achieving tremendous downloads and 1,200+ GitHub stars is a remarkable testimony to how well it is being received by the CNCF community. KubeArmor belongs in every K8 engineer’s open-source tool chest, and consequently, this book is a 'must-read' for every Cloud Native engineer."

Kubernetes has now fully emerged as the de facto Cloud Operating System. Just like in any OS, it is now important to harden and protect it. Linux Security Modules (LSMs) have been used for decades to provide very strong, fundamental proven security. Leveraging these primitives to provide an "armor" to Kubernetes is a natural progression and KubeArmor has achieved this very well. This book is a superb overview that all Cloud Security personnel will benefit from!"

KubeArmor's pioneering use of eBPF for kernel telemetry and LSMs for direct remediation redefines strategies to combat advanced zero-day threats, achieving a significant recognition in the CNCF community, as reflected by its remarkable download numbers and GitHub stars. This publication explores why KubeArmor's is deemed critical for every Cloud Native engineer, acclaimed for its straightforward explanation of intricate security principles. It rectifies and hardens Kubernetes vulnerabilities by enhancing performance and complying with Zero Trust security guidelines. The book demystifies advanced security techniques for a wide audience, from beginners to experts, and its highly recommended for everyone involved in Kubernetes deployment and hardening it as per NIST and MITRE security standards.”
FAQ
KubeArmor supports Workloads deployed as k8s orchestrated containers and VM/Bare-Metals workloads
For Kubernetes, the deployment is a demon set.
With edge computing shifting towards containerized workloads and in a few cases to orchestrated kubernetes workloads, it becomes important to have a security solution.
KubeArmor not only provides enforcement into different forms of deployment but can also provide real-time container-rich observability.
KubeArmor supporting un-orchestrated containers, k8s workloads and bare metal VMs makes it an ideal universal engine. Its kernel-level runtime security enforcement and container-aware observability bring the best of both worlds.












