
Defend against BPFDoor Malware with AccuKnox
The Attacker Red Menshen, a threat organization based in China, has been observed using the BPFDoor, it is a custom backdoor to target Middle Eastern and Asian telecommunication corporations as well as organizations in the government, education, and logistics sectors into 2021. TCP, UDP, and ICMP are just a few of the protocols that this backdoor support, […]
Reading Time: 8 minutes
Table of Contents
Introduction
This BPFDoor malware leverages reverse shell method. Such a flaw in an application allows an attacker to run remote code on the victim’s computer to start a shell session. The attacker just needs to watch for incoming connections on the right port when the victim unknowingly establishes a connection. Once the connection is made, the attacker has access to the victim’s shell and can perform a variety of fun actions. Let’s assume reverse shell like a tennis ball. It will come back at you if you throw it on a hard object. All you have to do is catch it at the proper moment and location.
💡TL;DR
- This BPFDoor malware leverages the reverse shell method.
- The Attacker Red Menshen, a threat organization based in China, has been observed using the BPFDoor, a custom backdoor to target Middle Eastern and Asian telecommunication corporations as well as organizations in the government, education, and logistics sectors, into 2021.
- Investigation and analysis of BPFdoor, a freshly found backdoor trojan, has been silently attacking Linux and Solaris computers for more than five years.
- We use the deployment to test the malware by using KubeArmor and custom policies.
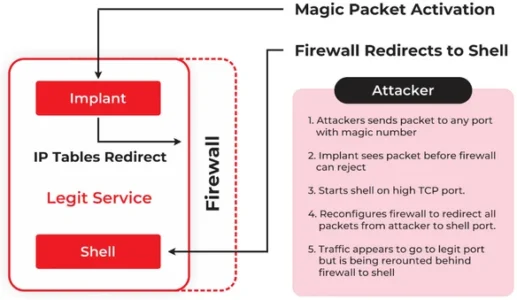
The Attacker
Red Menshen, a threat organization based in China, has been observed using the BPFDoor, it is a custom backdoor to target Middle Eastern and Asian telecommunication corporations as well as organizations in the government, education, and logistics sectors into 2021. TCP, UDP, and ICMP are just a few of the protocols that this backdoor support, for interacting with a C2, giving the threat actor a variety of ways to interact with the implant.
The majority of Red Menshen activity occurred between weekdays with no activity recorded on weekends. with the majority of communication occurring between 01:00 and 10:00 UTC. This trend implies that the threat actor has a regular 8 to 9-hour activity window, that is likely to coincide with local working hours.
How did it originate?
The threat actor employs a wide range of methods in its post-exploitation phase. Custom variants of the shared tool Mangzamel (including Golang variants), custom variants of Gh0st, and open source tools like Mimikatz and Metasploit to help in its lateral movement across Windows PCs are also included and the threat actor delivers orders to BPFDoor victims using Virtual Private Servers (VPSs) hosted by a well-known provider, and that these VPSs are managed through hacked routers headquartered in Taiwan, which the threat actor utilizes as VPN tunnels.
Investigation analysis of BPFDoor
- BPFdoor, a freshly found backdoor trojan, has been silently attacking Linux and Solaris computers for more than five years.
- BPFdoor is a Linux/Unix backdoor that allows threat actors to connect to a Linux shell remotely in order to obtain total access to a compromised device.
- BPFdoor does not require the opening of ports, is unaffected by firewalls, and can respond to orders from any IP address on the internet, making it a perfect weapon for corporate espionage and persistent attacks.
- BPFdoor is a passive backdoor, which means it can listen on one or more ports for incoming packets from one or more hosts, which attackers can exploit to remotely deliver orders to the infiltrated network.
- The virus employs a Berkeley Packet Filter (BPF) sniffer, which operates at the network layer interface and can view all network activity and transmit packets to any destination.
- BPF does not follow any firewall restrictions due to its low-level location.
- BPFdoor solely parses ICMP, UDP, and TCP packets, looking for a certain data value and, for the latter two, a password.
- What distinguishes BPFDoor is its ability to monitor any port for the magic packet, even if such ports are utilized by legal services such as web servers, FTP, or SSH.
- If the TCP and UDP packets include the correct “magic” data and password, the backdoor will execute a supported operation, such as establishing a bind or reverse shell.
- The study discovered BPFdoor activity on networks of companies in a variety of locales, including the United States, South Korea, Hong Kong, Turkey, India, Vietnam, and Myanmar.
- It achieves root-level permissions by exploiting CVE-2019-3010 – a vulnerability in the XScreenSaver component of the Solaris operating system.
| Vulnerable File Path | File Action |
| /tmp/getuid.so | CVE-2019-3010 exploit binary |
| /usr/lib/secure/getuid.so | CVE-2019-3010 exploit binary or log file |
Malware Operation
- Residing in system memory, it performs anti-forensics actions to delete the process environment and albeit unsuccessfully as it leaves it empty.
- Loads a Berkeley Packet Filter (BPF) sniffer, allowing it to view packets in front of any locally operating firewalls.
- When a relevant packet is received, the ‘iptables’ rules are modified to enable adversary access across the local firewall.
- Uses a moniker similar to a common Linux system daemon to disguise the binary.
- It is renamed and executed as /dev/shm/kdmtmpflush.
- Before destroying the binary, it changes the date to October 30, 2008 and this method is called timestomping.
time-stomping
The malware includes many predefined names that correspond to command strings included within pertaining packets.
To construct a bind shell on ports 42391 through 42491, use justtryit, justrobot, and justforfun.
Foolproof BPFDoor with AccuKnox
AccuKnox has Policy-Templates. It has policies for CVEs and Compliances and etcetera. For this particular vulnerability we are going to pick the policy from that policy template. Now let’s reproduce the environment. This malware works on any linux system. For reproducing I am going to use an Ubuntu image.
kind: Deployment
metadata:
div>
We can use this deployment to test the malware. Save this as an YAML file and apply using “kubectl apply -f bpfdoor-deployment.yaml” After that it will be deployed in your cluster.
- The initial point of the malware is that it is creating the file in the system when it’s deployed “/dev/shm/kdmtmpflush” and that’s how it’s designed.
- With KubeArmor blocking that malware is very simple with one policy. Let’s take that policy from the policy templates.
Here in the policy we added Here in the policy we added name: ksp-bpfdoor-malware
- To apply the policy run the below command.
https://raw.githubusercontent.com/kubearmor/policy-templates/main/malware/system/ksp-bpfdoor-malware.yaml
- Here in the policy we added
- As we know that this is the initial point and that’s why we added the “/dev/shm/kdmtmpflush” in process and “/var/run/haldrund.pid” this process ID is created after the execution of “kdmtmpflush” binary.
- We have created another policy for other variants observed. That policy is a very lengthy one to show here. To view the policy click here. To apply the policy run below command.
https://raw.githubusercontent.com/yasin-cs-ko-ak/policy-templates/main/malware/system/ksp-bpfdoor-malware-1.yaml
- But with KubeArmor we are blocking that in the initial stage.
- This is because KubeArmor is using BPF to track sys calls and also that malware is made of BPF too.
- Now we have created the deployment and we have a policy. Let’s see that in action.
- After entering into the pod Clone this repository “https://github.com/yasin-cs-ko-ak/bpfdoor-malware.git”
Compile the “bpfdoor.c” file and execute as shown below.
This is before applying the policy:
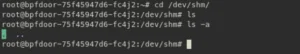
- Here there is no file generated and we haven’t executed any malwares yet.
This is after applying the policy:
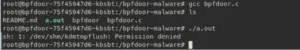
- Here we have compiled the C code into binary and executed. But the binary did not run.
Because we are applying the policy into the infected container. - Now let’s look at the karmor logs and see if it is actually blocking it or not.
karmor logs:
gRPC server: localhost:32767
Created a gRPC client (localhost:32767)
Checked the liveness of the gRPC server
Started to watch alerts
== Alert / 2022-05-23 08:16:34.396628 ==
Cluster Name: default
Host Name: gke-cys-test-may-23-default-pool-1669ba32-br5m
Namespace Name: default
Pod Name: bpfdoor-75f4594❯7d6-fc4j2
Container ID: 52b702f95ff4bbeffc5a7fc05dc77fae3d01fc5855301693b5a646538179ba08
Container Name: ubuntu-1-
Policy Name: ksp-bpfdoor-malware
Severity: 1
Tags: BPF,BPFDOOR,MALWARE
Message: Alert! /dev/shm/kdmtmpflush file detected possible bpfdoor malware.
Type: MatchedPolicy
Source: /bin/dash
Operation: Process
Resource: /bin/rm -f /dev/shm/kdmtmpflush
Data: syscall=SYS_EXECVE
Action: Block
Result: Passed
- Here we got a log for initial access of the malware. The malware rename itself and copy into the “/dev/shm/” directory as “kdmtmpflush”
- It got blocked by KubeArmor and the policy we applied.
Cluster Name: default
Host Name: gke-cys-test-may-23-default-pool-1669ba32-br5m
Namespace Name: default
Pod Name: bpfdoor-75f45947d6-fc4j2
Container ID: 52b702f95ff4bbeffc5a7fc05dc77fae3d01fc5855301693b5a646538179ba08
Container Name: ubuntu-1-container
Policy Name: ksp-bpfdoor-malware
Severity: 1
Tags: BPF,BPFDOOR,MALWARE
Message: Alert! /dev/shm/kdmtmpflush file detected possible bpfdoor malware.
Type: MatchedPolicy
Source: /bin/dash
Operation: Process
Resource: /bin/cp ./a.out /dev/shm/kdmtmpflush
Data: syscall=SYS_EXECVE
Action: Block
Result: Passed
- Here the malware tries to copy itself to the directory “/dev/shm/” and it’s got blocked.
- Here the malware changes its permission to “755” so it can be read and execute access for everyone and also write access for the owner of the file.
- This syscall also blocked by KubeArmor.
Cluster Name: default
Host Name: gke-cys-test-may-23-default-pool-1669ba32-br5m
Namespace Name: default
Pod Name: bpfdoor-75f45947d6-fc4j2
Container ID: 52b702f95ff4bbeffc5a7fc05dc77fae3d01fc5855301693b5a646538179ba08
Container Name: ubuntu-1-container
Policy Name: ksp-bpfdoor-malware
Severity: 1
Tags: BPF,BPFDOOR,MALWARE
Message: Alert! /dev/shm/kdmtmpflush file detected possible bpfdoor malware.
Type: MatchedPolicy
Source: /bin/dash
Operation: Process
Resource: /dev/shm/kdmtmpflush –init
Data: syscall=SYS_EXECVE
Action: Block
Result: Permission denied
- And finally the malware executes itself via “/dev/shm/kdmtmpfluh –init” to run on the system.
- That syscall also blocked by KubeArmor.
- This is how KubeArmor protects our workloads and systems from malware.
- These logs prove how KubeArmor is effective and important for organization.
Conclusion
BPFDoor malware is a stealthy malware that has been hidden for almost five years because of the BPF capabilities. Predominantly BPFDoor malware has escaped most of the firewalls and all defensive systems. Because it works on kernel level and majority of firewalls do not have the visibility at Kernel level.
Hence, AccuKnox Enterprice solution comes into action of protect cloud-native workloads in K8s, VMs and baremetal environments at Static and Runtime levels. KubeArmor uses eBPF capabilities to track syscalls and defend unwanted syscalls made by malwares and threats.
Book a demo at AccuKnox for production grade security and protection for your organization.
Additional resources:
- BPFDoor: Stealthy Linux malware bypasses firewalls for remote access
- https://pastebin.com/kmmJuuQP
- https://www.virustotal.com/gui/file/dc8346bf443b7b453f062740d8ae8d8d7ce879672810f4296158f90359dcae3a/detection/f-dc8346bf443b7b453f062740d8ae8d8d7ce879672810f4296158f90359dcae3a-1567566897
- https://doublepulsar.com/bpfdoor-an-active-chinese-global-surveillance-tool-54b078f1a896
- https://www.sandflysecurity.com/blog/bpfdoor-an-evasive-linux-backdoor-technical-analysis/
- https://www.crowdstrike.com/blog/how-to-hunt-for-decisivearchitect-and-justforfun-implant/
AccuKnox delivers full Enterprise-ready features and this is depicted below.
Reach out to us and we will be glad to lend you a hand in your journey from Zero to Zero trust.
🌍Home: Zero Trust Cloud-Native Application Protection Platform
📄Help: Intro – AccuKnox
📝Blogs: Blog
- Schedule 1:1 Demo
- Product Tour
On an average Zero Day Attacks cost $3.9M

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support



