
Securing Kubernetes – Addressing Common Pitfalls and Enhancing Security with AccuKnox CNAPP
Kubernetes is the most widely used open-source platform for container orchestration. It automates a variety of container management-related operations. Deployment, scalability, testing, management, etc are simplified. This blog will go through some typical Kubernetes blunders that most businesses make. The list includes all the major problems faced by several enterprises that have adopted Kubernetes. We’ll […]
Reading Time: 12 minutes
Table of Contents
Kubernetes is the most widely used open-source platform for container orchestration. It automates a variety of container management-related operations. Deployment, scalability, testing, management, etc are simplified. This blog will go through some typical Kubernetes blunders that most businesses make. The list includes all the major problems faced by several enterprises that have adopted Kubernetes. We’ll talk about the issues while emphasizing how to prevent or resolve them. We recommend maintaining a checklist of all the good practices. It should be referred to time and time again to use Kubernetes to its full potential. Testing in a Kubernetes environment demands a full understanding of the platform’s architecture and components. Without thorough testing practices in place, organizations usually encounter unexpected bugs or failures in their applications. Effective management of Kubernetes clusters is also crucial for smooth operations.

Top 10 Kubernetes Mistakes to Avoid

| Kubernetes Mistake | Security | Availability | Scalability | Resource Efficiency | Maintainability | Compliance | Cost |
|---|---|---|---|---|---|---|---|
| Exposed Secrets | 4 | 2 | 1 | 1 | 2 | 3 | 1 |
| Inadequate RBAC | 4 | 2 | 1 | 1 | 3 | 3 | 1 |
| Unpatched Vulnerabilities | 4 | 3 | 2 | 1 | 2 | 4 | 3 |
| No Resource Limits | 2 | 3 | 3 | 4 | 2 | 1 | 4 |
| Unmonitored Resources | 2 | 2 | 2 | 3 | 2 | 1 | 2 |
| Using Host Path Volumes | 3 | 1 | 2 | 1 | 2 | 2 | 1 |
| Privileged Containers | 4 | 2 | 3 | 3 | 3 | 3 | 2 |
| Skipping Config Backups | 3 | 2 | 1 | 1 | 2 | 2 | 2 |
| Deprecated API Usage | 3 | 2 | 1 | 1 | 2 | 2 | 1 |
| Ignoring Network Policies | 4 | 2 | 3 | 2 | 3 | 3 | 2 |
| Manual Scaling | 2 | 3 | 3 | 3 | 2 | 1 | 2 |
| No Failover Planning | 3 | 4 | 2 | 2 | 2 | 2 | 2 |
| Unencrypted Data Transit | 4 | 2 | 2 | 2 | 2 | 3 | 1 |
| Pod Misconfigurations | 3 | 2 | 2 | 2 | 2 | 2 | 2 |
| Using Default Credentials | 4 | 2 | 1 | 1 | 1 | 4 | 1 |
* Scale: 0 = Lowest | 4 = Highest
Exposed Secrets
Sensitive data is compromised when secrets in Kubernetes setups are exposed. This leaves gaps for unauthorized access. The Tesla AWS breach exposed critical data because their Kubernetes cluster lacked proper access restrictions. By 2023, 90% of firms will experience a security breach as a result of improperly maintained secrets, according to a Gartner analysis. Services are disrupted by unauthorized access. Potential data breaches or unauthorized changes also affect availability. It prevents further scaling efforts by introducing security flaws. Before the systems’ expansion, these must be removed. Imagine that a hacker gains unauthorized access to a Kubernetes deployment. They may modify the application’s parameters causing critical system failure. It requires some maintainability but does not reduce resource efficiency. Regular audits and securing secrets add to the maintenance overhead. It violates compliance standards such as GDPR or HIPAA. Expect legal and financial consequences. This also includes legal penalties and damage to reputation.
- A more sophisticated approach would be to use external secret management tools like HashiCorp Vault or CyberArk Conjur
- Use Kubernetes Secrets to securely store sensitive information like passwords and API keys.
- Implement encryption and access controls for secrets to prevent unauthorized access.
- Regularly rotate secrets to minimize the impact of potential breaches. Auditing is also necessary.
AccuKnox prevents ransomware attacks on HashiCorp Vault and CyberArk Conjur by identifying default security postures, applying whitelisting approach to the least permissive controls, in-line mitigation from the anomalies.

Inadequate role-based access control
Weak RBAC settings cause unauthorized access. Illegal users might disrupt services, causing availability issues. For example, a user with excessive permissions may accidentally delete critical resources. Although scalability is unaffected, it causes inefficiencies by allowing needless access and taxing resources. Without it, access control becomes challenging. The number of mistakes and problems with user administration increases. 2020 saw the occurrence of a security issue impacting the Kubernetes GitHub repository as a result of an internal privilege leak. In a CyberArk survey, 73% of businesses felt their privileged access restrictions needed to be strengthened. Additionally, it violates compliance standards that demand controlled access to sensitive information. Ineffective RBAC leads to security breaches that result in monetary losses and reputational damage. The least privilege principle should be established and followed when assigning roles and permissions. RBAC configurations should always be checked for updates.
- Implement Role-Based Access Control (RBAC) to restrict access permissions based on user roles.
- Regularly review and update RBAC policies to ensure the least privileged access.
- Utilize Kubernetes audit logs to monitor and detect any unauthorized access attempts.
- Just-in-time provision of the access and revoking after a certain duration becomes critica

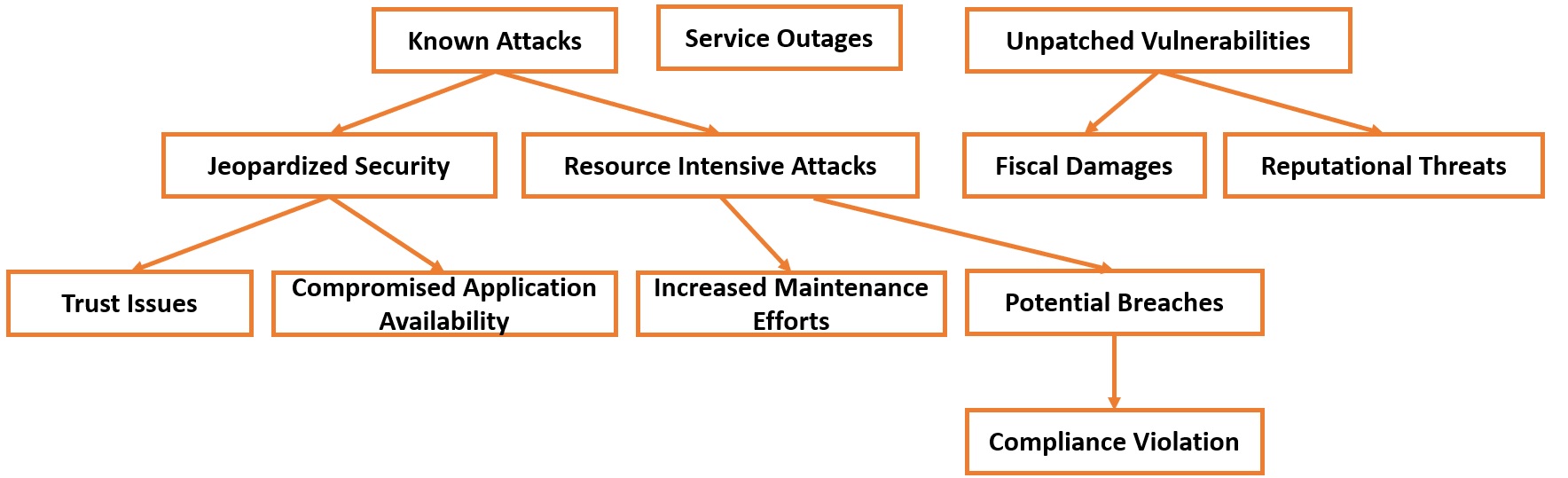
Unpatched Vulnerabilities
They expose Kubernetes clusters to known attacks, jeopardizing security. It also hampers trust due to service outages or compromises the availability of applications. Resource-intensive attacks that consume system resources. Failing to apply patches regularly increases maintenance efforts as you deal with potential breaches. Attackers exploit a known Kubernetes vulnerability to deploy unauthorized pods. Operating with unpatched vulnerabilities may violate compliance standards demanding up-to-date security measures. The Kubernetes CVE-2020-8555 vulnerability allowed attackers to bypass API access restrictions. The Ponemon Institute’s Cost of a Data Breach Report found that unpatched vulnerabilities extended the average data breach lifecycle by 26%. They cause significant fiscal damages, not to mention reputational threats and collusion.
- The easiest way to solve this is by installing a regular patch management process and automating patch deployment.
- Kubernetes clusters should often be upgraded and patched in order to protect against known vulnerabilities.
- Use a vulnerability management toolto scan and assess the security of the container image.
- Based on tool’s capability and coverage known vulnerabilities may be highlighted or prioritized. However, the threat from unknown vulnerabilities or zero-day attacks will still make cluster vulnerable
AccuKnox assumes those known and unknown (zero-day attack) vulnerabilities to be present in the cluster. It will ensure to detect current vulnerability leveraging multiple tools and ensure to achieve a Zero-Trust least permissive posture for overall cluster resiliency and over and above threats from rutime attack vectors. AccuKnox is built upon Zero Trust security controls to prevent unauthorized access, backdoor operations, network interface usage, file system manipulations, process execution, and administrative functions. We also produce fine-grained app-level audits and alerts.

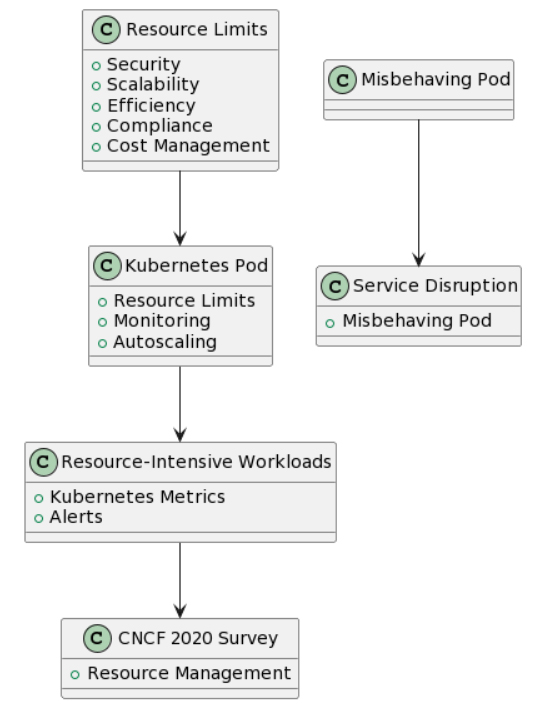
No resource limits
Since unbounded resources lead to resource exhaustion attacks, they are directly related to security. This degrades the availability of other services. Without proper rate limiting, resource contention hinders the scalability of applications. All this will lead to inefficient resource use as some pods consume more than required. Consider a scenario where a misbehaving pod consumes excessive resources, causing a service disruption. Managing applications becomes complex and challenging to troubleshoot. It impacts compliance by enabling resource abuse. Unnecessary infrastructure costs will also rise. We recommend setting resource limits for CPU and memory on pods, monitoring resource utilization, and adjusting limits accordingly. A high-resource consumption pod affects the performance of other applications in the cluster. The CNCF 2020 Survey revealed that resource management was a top challenge for Kubernetes users.
- Set Kubernetes pod resource limitations to avoid resource conflict and guarantee equitable distribution.
- Resource-intensive workloads may be identified and optimized by keeping an eye on resource usage using Kubernetes metrics and alerts. AccuKnox provides continuous compliance reports for cloud resources and applications, including NIST, MITRE, CIS, and DISA standards, with alerts for violations and a namespace-based compliance summary.
- To dynamically modify resources based on workload needs, use auto scaling techniques.
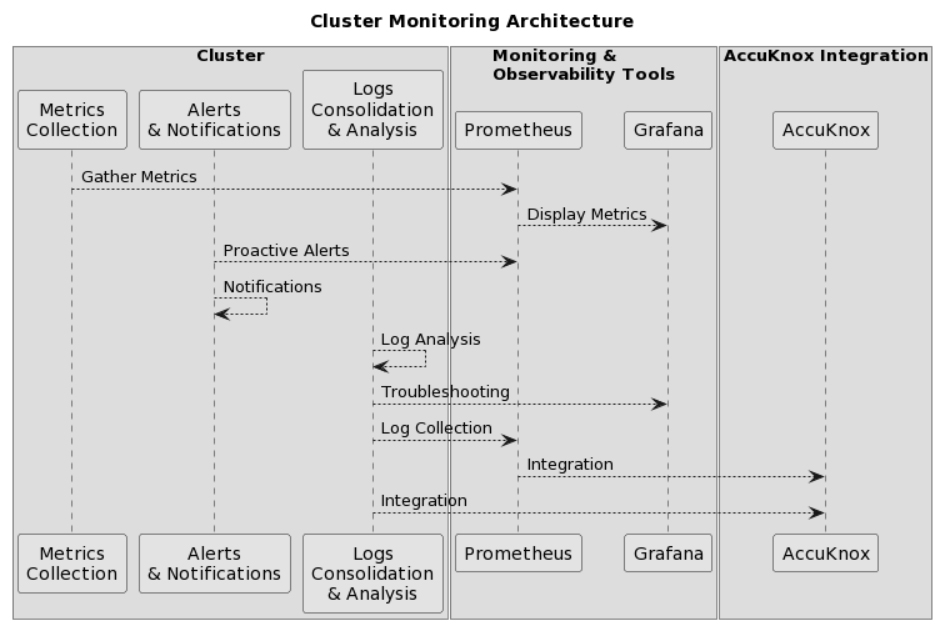
Unmonitored Resources
Lack of monitoring leaves clusters susceptible to undetected security breaches or anomalies. Without monitoring, service disruptions or performance issues might go unnoticed, affecting availability. Scaling issues are bound to come up sooner or later if you’re unaware of resource demands. It also prevents efficient resource use optimization. Troubleshooting without monitoring data becomes challenging, increasing maintenance efforts. In regulated industries, inadequate monitoring can lead to non-compliance with audit requirements. The cost of outages or resource waste will also ramp up. For example, a sudden spike in CPU usage remains unnoticed. This will increase the response time for an application. Consider implementing all-in-one monitoring and alerting using tools like Prometheus and Grafana. AccuKnox integrates with Grafana very well. A gradual memory leak in a container goes unnoticed until it affects application performance. The State of DevOps Report found that organizations with mature monitoring practices had three times lower change failure rates.
- To gather and display cluster metrics, and set up monitoring and observability tools like Prometheus and Grafana.
- Use alerts and notifications to proactively identify performance problems or breakdowns and take appropriate action.
- To consolidate and analyze logs for troubleshooting and debugging, create Kubernetes logging frameworks.
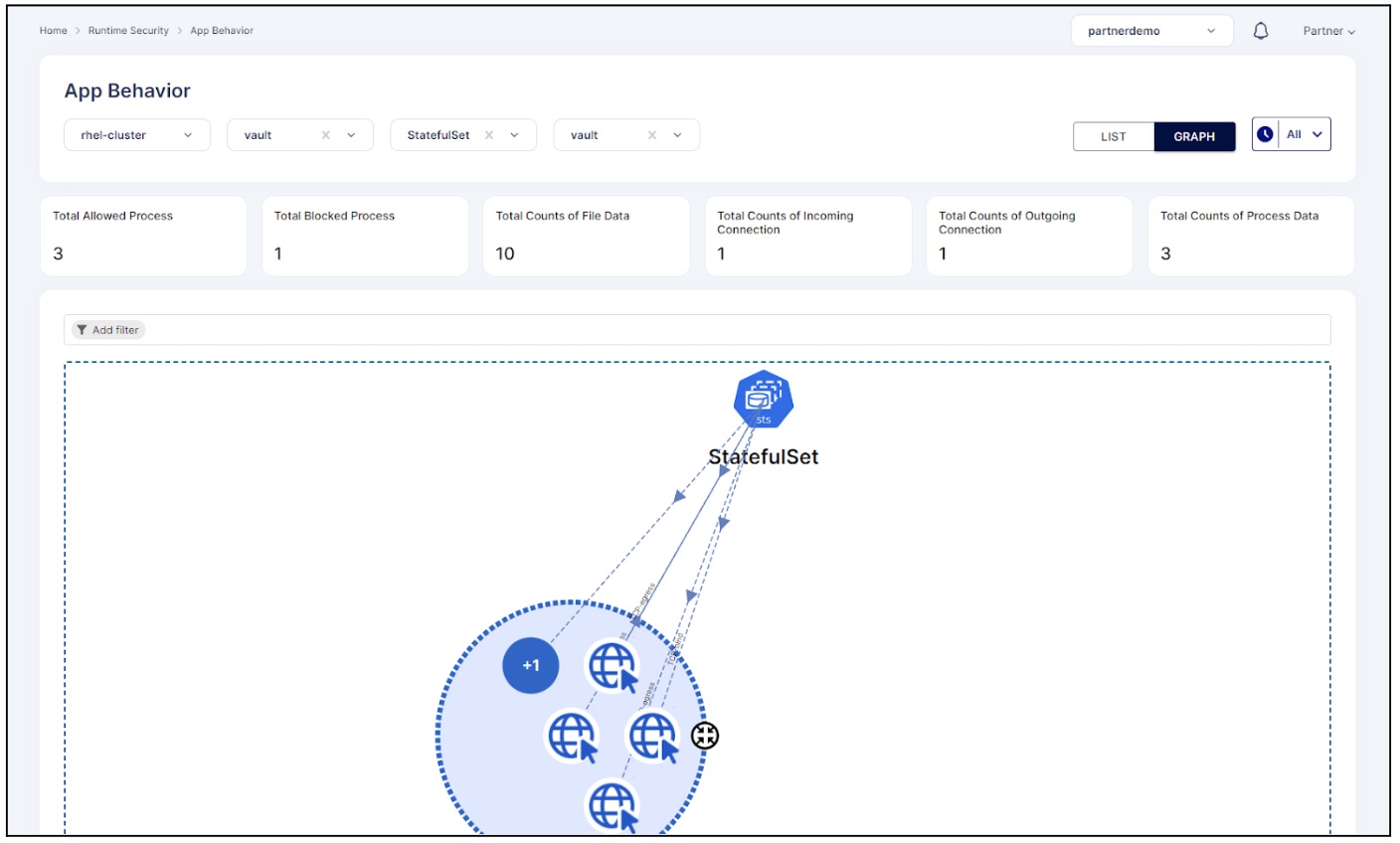
AccuKnox provides a way to showcase application behavior through network graphs with interactive view of ingress and egress connections. AccuKnox also helps in Continuous Monitoring of the workload and provide integrations with SIEM tools such as Splunk, Azure Sentinel etc.
Privileged Containers
A compromised privileged container grants attackers access to the host system. The 2020 Container Security Survey found that 44% of respondents believed privileged containers increased security risks. Such containers have elevated permissions. The attack surface rises, and so do security risks. Misused privileged containers compromise system stability and lead to service disruptions. They also consume more resources, affecting the efficiency of other applications. Managing privileged containers adds complexity and risk to maintenance operations. It violates compliance requirements for the least privilege. Security breaches or resource inefficiencies in privileged containers cause fiscal damage. Avoid using them unless absolutely necessary. Instead, go for fine-grained security contexts and capabilities.
- Unless absolutely required, avoid running containers with privileged access.
- Apply Kubernetes Pod Security Policies (PSPs) to privileged containers to impose limitations.
- Review and update PSPs often to ensure compliance with security best practices
Skipping Configuration Backups
Without proper backups, accidental misconfigurations or failures cause data loss and downtime. It also increases the complexity of restoring services to a stable state after incidents. Skipping configuration backups leaves no recovery option in case of security incidents or data loss. Imagine a situation where an administrator mistakenly applies a configuration change that results in a service outage, with no backup available. In regulated industries, it is a big indicator of non-compliance. Data loss from skipped backups can cause a lot of trouble for cloud infrastructure, companies, and users. Administrations must regularly back up configuration files, manifests, and other critical data. This can be done using version control systems or backup tools. A misconfigured update causes data corruption, and without backups, the previous stable state can’t be restored.
- Provision automated backup programs for manifests and configuration files used by Kubernetes.
- To guarantee data availability and integrity, verify the backup and restoration procedure often.
- Backups should be kept in a safe, remote place to avoid illegal access.
Reliance on deprecated APIs
Typically, they have flaws that are well-known and that attackers could use to compromise security. According to the 2021 Global State of Multi-Cloud Report, 53% of enterprises have suffered cloud data loss. Growth is hampered by a lack of features necessary for effective scaling. Suboptimal methods will lead to ineffective resource allocation. It makes maintenance more difficult because they might not get updates or support. Modern security measures are necessary for compliance with industry requirements; this will categorically fail. Deprecated API vulnerabilities can cause serious financial losses as a result of security breaches. Keep up with Kubernetes version updates and switch from obsolete APIs to supported replacements. If deprecated APIs are deleted or become incompatible, relying on them could cause service interruptions. The Kubernetes 1.16 release deprecated the extensions/v1beta1 API, encouraging users to migrate to the apps/v1 API. A 2021 CNCF survey revealed that 25% of respondents were still using deprecated Kubernetes APIs. A Kubernetes update removes a deprecated API, causing applications that rely on it to fail.
- Keep current with API changes by often checking the release notes and deprecation policies for Kubernetes.
- Applications should be changed to switch from deprecated APIs to those that are recommended.
To make sure that Kubernetes is compatible with the most recent APIs, use versioning and upgrade techniques.

Ignored Network Policies
A database is accessed by unauthorized pods as a result of missing network policies. Ignoring network regulations results in uncontrolled communication between pods, which raises the danger of intrusion by unauthorized parties or data leakage. It impacts the availability of the application by causing congestion or interference. Another major issue will be resource conflict, which will result in ineffective resource use. Lackluster network restrictions in the Capital One hack allowed attackers to roam laterally throughout the system. Elite performers were 1.5 times more likely to adopt automated security policy enforcement, according to the 2020 State of DevOps Report. To regulate and secure communication between pods, it is advised to establish and execute network policies.
Ignoring network policies complicates troubleshooting and maintenance by introducing unexpected traffic flows. Failing to implement network policies hints at non-compliance with data protection regulations.
- In order to manage traffic between pods, use network rules.
- On the basis of pod labels and namespaces, provide specific ingress and egress rules to limit communication.
- Review and update network policies often to make sure they meet application demands and security specifications.
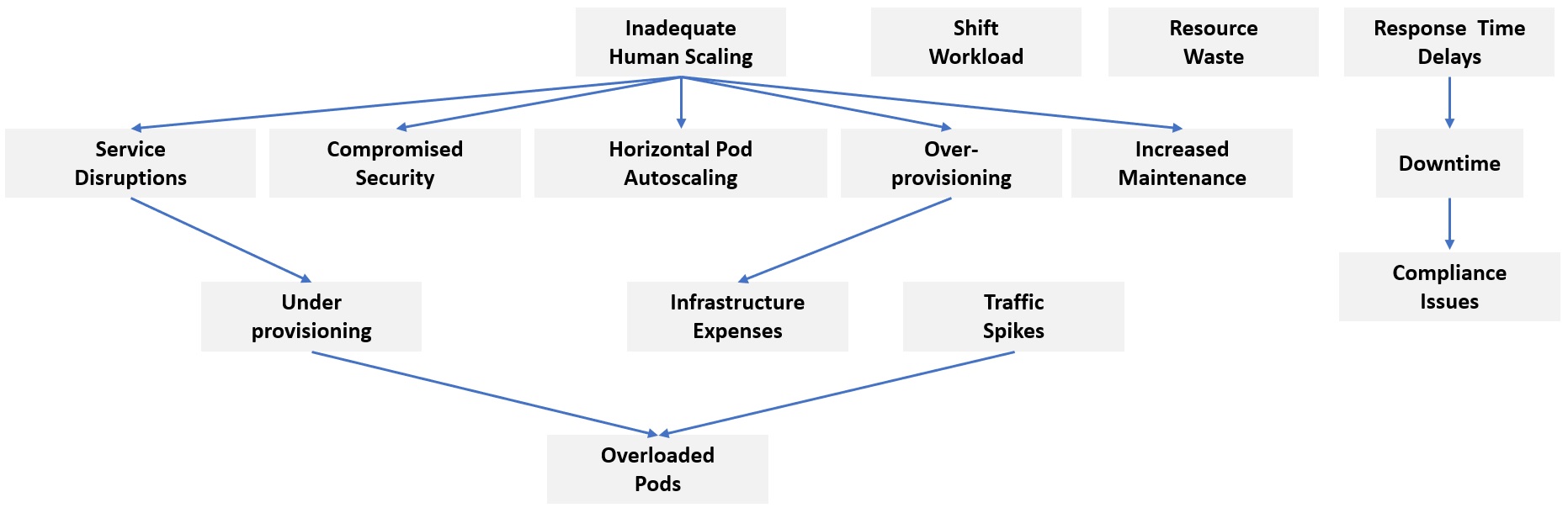
Manual Scaling
The main cause of service disruptions with abrupt increases in demand is inadequate human scaling. When traffic spikes occur, manual scaling may result in under-provisioning, which compromises security by failing to meet demand. Manually scaled pods become overloaded by a sudden increase in traffic, disrupting service. According to the CNCF 2021 Survey, 65% of participants used horizontal pod autoscaling. The capacity to swiftly adjust to shifting workloads is limited when manual scaling is the only method used. Other typical errors include over-provisioning and resource waste during times of lesser demand. It needs ongoing observation and management, increasing maintenance requirements. Response times dramatically lengthen as a result of manual scaling delays brought on by increased traffic brought on by release or version rollouts. Because scaling problems may generate downtime that lowers the Service Level Agreement (SLA), it obviates compliance indirectly. Manual scaling leads to overprovisioning, which increases infrastructure expenses. To automatically change the number of replicas based on resource usage, implement horizontal pod autoscaling.
- Analyze workload trends on a regular basis to fine-tune scaling thresholds and guarantee optimal resource allocation.
- To dynamically change the number of replicas based on CPU or custom metrics, use horizontal pod autoscaling (HPA).
- Scale depending on metrics particular to an application with Kubernetes Custom Metrics APIs.
No failover planning
Lack of one may cause security problems, extended downtime, and financial losses. Processes for service recovery and maintenance are also compromised. Non-compliance with availability criteria and monetary losses are also an issue. Due to failover absence, a significant pod failure results in service unavailability. Kubernetes replica or stateful sets with appropriate failover configurations will prove handy. Due to database errors, e-commerce websites frequently face hours of outage. The 2021 State of IT Resilience Report states that 51% of enterprises encountered irrecoverable data events.
- Set up numerous replicas of crucial components like etcd, the control plane, and worker nodes to implement Kubernetes High Availability (HA) settings.
- To enable automated failover and resilience, use Kubernetes Deployments with StatefulSets.
- Test and replicate failure situations often to verify failover procedures and guarantee system dependability.

Unencrypted Data Transit
Sensitive information is vulnerable to eavesdropping during data transmission. Scalability, resource efficiency, maintenance, compliance, and prices are impact points. Without encryption, sensitive data can be stored or sent. This is against compliance regulations. Use TLS or SSL for communication between pods and services to increase security. The hefty expenses connected with breaches brought on by unencrypted data are highlighted in the 2023 Cost of a Data Breach Report. Attackers have the chance to intercept private information sent between pods.
- Encrypt communication between Kubernetes components and outside services using Transport Layer Security (TLS).
- At the cluster edge, terminate SSL/TLS connections with Kubernetes Ingress Controllers.
- To safeguard data while it is being sent, containerized apps should enforce HTTPS encryption methods.
Pod Misconfigurations
They expose vulnerabilities, cause unauthorized access, and lead to performance issues or downtime. To prevent breaches, use Kubernetes security tools. They scan for misconfigurations and follow best practices when defining pod specifications. A Gartner report estimates that by 2025, 99% of cloud security breaches will be due to customer misconfigurations. In this scenario, a misconfigured pod exposes a service to the public internet.
- To impose best practices and security configurations on pods, leverage Kubernetes Pod Security Policies (PSPs).
- Apply specialized tools or built-in Kubernetes capabilities to routinely audit and scan pods for misconfigurations.
- Pre-deployment checks and CI/CD pipelines should be used to avoid misconfiguration problems.
Using default credentials
An attacker can easily gain access to a Kubernetes cluster and compromise the entire system. Default credentials go against security best practices and make access control more complicated. Change them as soon as you install the software to increase security. The Mirai botnet infiltrated IoT devices, causing massive outages. Verizon’s 2021 Data Breach Investigations Report indicates that 61% of incidents involved stolen or shoddy credentials.
- To enforce distinct and non-default credentials, use robust authentication techniques like Kubernetes RBAC (role-based access control).
- Passwords and service account tokens should be periodically audited and changed.
- Kubernetes secrets or third-party secret management tools are recommended for securely storing and managing credentials
Conclusion
Kubernetes is a powerful open-source container orchestration platform. It simplifies several container management operations. However, businesses often face challenges in achieving their full potential. These include:
- Scalability planning
- End-to-end testing
- Effective K8s cluster management
- Staying current with deprecated APIs
- Configuring network policies
- Automation
- Security
- Data protection in transit.
Scalability planning is crucial to avoid performance bottlenecks and unwarranted expenditures. Testing helps uncover hidden bugs and application failures. Management of Kubernetes clusters prevents security breaches and resource mismanagement. Staying updated with deprecated APIs is essential for long-term success. Network policies should be embraced to protect Kubernetes environments from unauthorized access and breaches. Automation is essential for swift adaptation and recovery of Kubernetes resources. It also promotes resilience and continuous uptime. Security is a top priority, with regular updates, role-based access control, and encryption to mitigate risks. Encrypting data during transit ensures its integrity and confidentiality. By developing a checklist of best practices you may navigate the Kubernetes landscape with confidence. Implement these strategies with AccuKnox, to optimize Kubernetes deployments. We ensure a seamless, secure, and cost-effective journey into the world of container orchestration.
All Advanced Attacks are Runtime Attacks
Zero Trust Security
Code to Cloud
AppSec + CloudSec

Prevent attacks before they happen
Schedule 1:1 Demo




